Source:-cmswire.com
In an ideal world, cybersecurity would take care of itself. But even with microservices, a contemporary architecture type with significant advantages over monolithic architectures, security remains an issue. In fact, some security issues are actually harder to resolve in a microservices architecture.
While this topic is open to debate, CMSWire has spoken to industry experts for their views and insights.
What Are the Security Issues Associated With a Microservices Architecture?
Eric Sheridan, chief scientist at WhiteHat Security, explained that a microservices application has, on average, 180 vulnerabilities, whereas a monolithic has approximately 39. “The issue with a microservices architecture is it frequently utilizes vulnerable third-party components,” he said. For example, say you ask developers to imagine that they are responsible for maintaining a monolithic application that declares and makes use of a vulnerable third-party component. “Once the component is declared, it’s represented as a single vulnerability. Now, imagine you are decomposing that same application into 25 separate microservices. Assuming those microservices leverage the same third-party component, you now have 25 vulnerabilities represented,” Sheridan said.
Sheridan went on to say that the use of vulnerable third-party components will become a common security issue for the next several years, which is why ensuring your brand possesses the ability to identify these vulnerable components is critical.
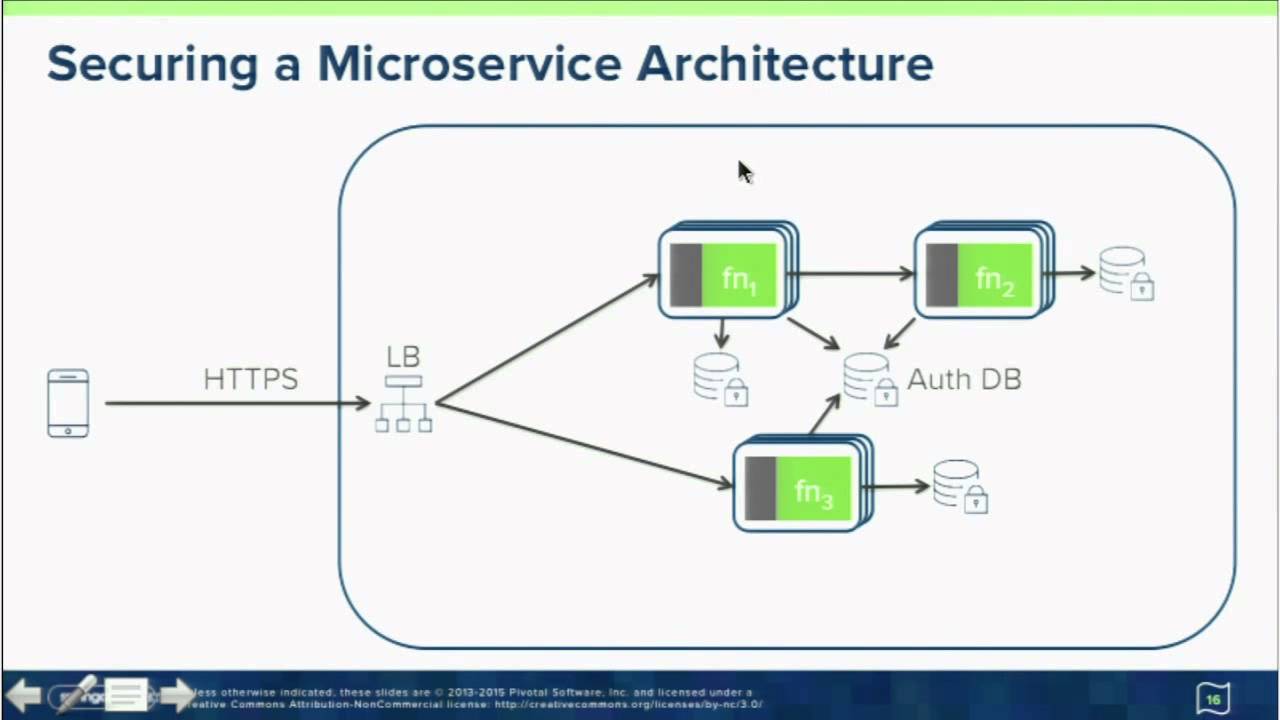
The other security issue associated with microservices, as identified by Jonathan DiVincenzo, head of product at Signal Sciences, are the new attack vectors. “What were once internal calls within an application — inside the monolith — are now delivered across the network, and across the internet, to other services. In this context, application security is one of the largest gaps of microservices,” said DiVincenzo.
“[Since] most microservices run via HTTP, the same security concerns as traditional application security apply from data injection attacks, cross-site scripting and privilege escalation to command execution. If sufficient monitoring or defense solutions aren’t put into place, you run the risk of being vulnerable to business logic attacks that could ultimately go undetected,” said DiVincenzo.
So how can organizations ensure that their microservices architecture is secure? Below our interviewees share 3 tips.
1. Implement a Web Application Firewall
A firewall can protect your microservices from recognized cyberthreats. However, “to stay ahead of attacks, you must have a modern web application firewall (WAF) that is not only capable of monitoring and identifying common web application attacks, but one that has the ability to detect business logic flaws, user account takeovers, or monitor any application flow users need,” said DiVincenzo.
DiVincenzo added that ATO is one the “biggest” concerns for organizations. DiVincenzo suggested utilizing a WAF that has a “specific ATO story” to protect your microservices against “unauthorized account access.”
2. Develop Each Microservice With “Fault-Tolerance”
Best practices and methodology should be followed when developing a microservice. Usually, in a microservices architecture, a microservice will have been designed and developed with its own development framework. Each of these frameworks will have its own security protocols, which can be difficult to manage.
OJ Ngo, CTO and co-f ounder of DH2i, advised brands to design and develop each microservice with an “agreed” best practice for the whole product. “Each service should be developed with fault-tolerance. A failed service should not be allowed to compromise or disrupt the entire stack. Each and every service should be developed and following the same testing and reporting methodology,” said Ngo.
By ensuring each service follows the same methodology, it will enable developers to quickly identify and resolve any issues.
3. Implement Authorization and Authentication
With the significantly larger number of independent services, there needs to be a measure of access control and authorization. OAuth is the industry standard as far as authorization goes, but as Jake Lumetta, CEO and co-founder of ButterCMS, explained, it is critical to create proper network boundaries.
“For securing microservices, one problem area is creating the proper network boundaries for services and understanding which services will be on the ‘edge’ and available to the public and which services will be ‘internal’ and should only be able to speak to other trusted microservices. Depending on who is consuming the service (public vs. internal) different levels of authentication and authorization will be needed,” said Lumetta.