What is VictorOps and Its Use Cases?
Efficient incident management and real-time collaboration are essential for modern IT operations. VictorOps, now part of Splunk, is a powerful platform designed to streamline on-call management, incident response, and team collaboration. VictorOps enables IT and DevOps teams to address incidents proactively, reduce downtime, and ensure service reliability.
VictorOps integrates seamlessly with monitoring tools to provide real-time alerts, context-rich notifications, and collaborative resolution workflows. By fostering a culture of accountability and continuous improvement, it helps teams resolve issues quickly and effectively.
What is VictorOps?
VictorOps is an incident management platform that focuses on on-call scheduling, alert routing, and team collaboration for incident response. The platform helps teams detect, manage, and resolve incidents efficiently by providing actionable alerts and real-time communication tools.
VictorOps centralizes alerts from monitoring tools, enriches them with contextual information, and routes them to the appropriate on-call team members. With its emphasis on collaboration and transparency, VictorOps ensures that incidents are addressed promptly while fostering a culture of continuous improvement.
Top 10 Use Cases of VictorOps
- Incident Management
Manage critical incidents with real-time alerts and collaborative resolution workflows. - On-Call Scheduling
Automate and manage on-call rotations to ensure round-the-clock coverage. - Alert Routing
Route alerts to the right team members based on severity, service, or predefined rules. - Collaboration During Incidents
Enable cross-team collaboration with integrated chat tools and context-rich notifications. - Automated Escalations
Escalate unresolved incidents to higher-level personnel automatically. - Post-Incident Analysis
Generate post-incident reports to analyze response times and identify areas for improvement. - Proactive Monitoring
Integrate with tools like Splunk, Nagios, or New Relic to monitor systems proactively and resolve issues before they escalate. - Service Reliability Management
Ensure service uptime and reliability by addressing incidents quickly. - Customer Support Integration
Notify customer support teams about issues impacting end-user experiences. - Security Incident Response
Coordinate responses to security alerts and vulnerabilities to mitigate risks effectively.
What Are the Features of VictorOps?
- Real-Time Alerts
Receive actionable alerts enriched with contextual information to speed up resolution. - On-Call Scheduling
Create and manage automated on-call rotations with fair scheduling. - Customizable Routing Rules
Define flexible alert routing to ensure the right team members are notified. - Integrated Collaboration
Collaborate during incidents with built-in chat tools and integrations with Slack or Microsoft Teams. - Post-Incident Reporting
Generate detailed incident timelines and reports for continuous improvement. - Mobile App Support
Manage incidents on the go with the VictorOps mobile app. - Multi-Channel Notifications
Send alerts through email, SMS, push notifications, and phone calls. - Integration Ecosystem
Connect VictorOps with monitoring tools like Splunk, Datadog, and Prometheus. - Escalation Policies
Configure escalation rules to ensure critical incidents are addressed promptly. - Analytics and Metrics
Track incident trends and response times to improve team performance.
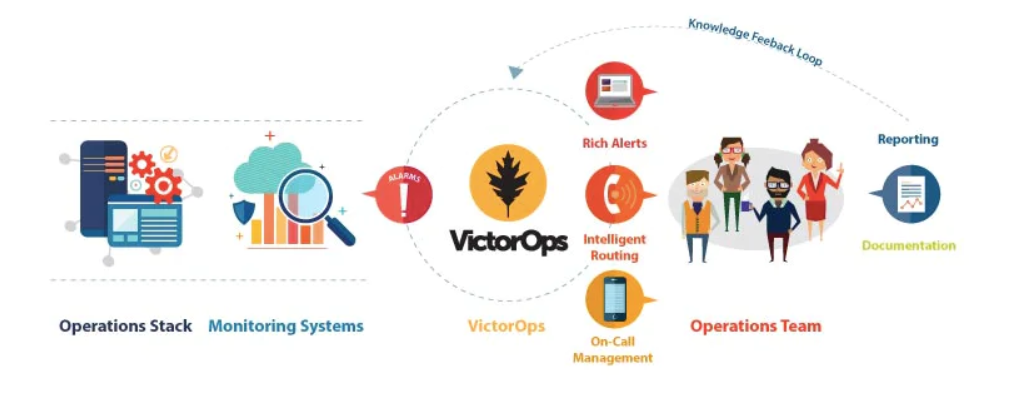
How VictorOps Works and Architecture
How It Works:
VictorOps acts as a central hub for incident alerts, collecting signals from monitoring tools and routing them to the appropriate on-call teams. Its collaborative features enable teams to resolve incidents quickly and efficiently.
Architecture Overview:
- Signal Collection:
VictorOps receives alerts from integrated monitoring tools. - Alert Enrichment:
Alerts are enriched with contextual information to provide actionable insights. - Routing and Escalation:
Alerts are routed to the right teams based on predefined rules, with automatic escalations if needed. - Collaboration:
Teams collaborate in real-time using integrated chat tools and shared incident timelines. - Post-Incident Reporting:
Generate detailed reports to analyze and improve incident response workflows.
How to Install VictorOps
Steps to Get Started with VictorOps:
Step 1: Create a VictorOps Account
- Visit the Official Website:
Navigate to VictorOps and click on the “Get Started” or “Free Trial” button. - Sign Up:
- Enter your organization’s details, including email, team name, and phone number.
- Choose a plan (free trial or paid) based on your requirements.
- Verify Email:
Check your email inbox for a verification link, and click it to activate your account. - Login to Your Dashboard:
Use your credentials to log in and access the VictorOps interface.
Step 2: Set Up Teams and On-Call Schedules
- Add Team Members:
- Navigate to the “Teams” section in the dashboard.
- Invite team members by entering their email addresses.
- Assign roles such as Admin, User, or Responder.
- Create On-Call Schedules:
- Go to the “On-Call Schedules” section.
- Define shift rotations and assign team members to ensure 24/7 incident coverage.
- Set up escalations to route unresolved alerts to backup personnel automatically.
Step 3: Install the VictorOps Mobile App
- Download the App:
- For Android: Visit the Google Play Store.
- For iOS: Visit the Apple App Store.
- Search for “VictorOps” or “Splunk On-Call” and install the app.
- Login to the App:
Use your VictorOps credentials to access the mobile interface. - Enable Push Notifications:
Allow the app to send notifications so you can receive real-time alerts on the go.
Step 4: Integrate Monitoring Tools
VictorOps integrates with numerous monitoring tools such as Prometheus, Splunk, Datadog, Nagios, and New Relic. Follow these steps to set up integrations:
- Navigate to the Integrations Section:
- In the VictorOps dashboard, go to the “Integrations” tab.
- Search for the monitoring tool you want to integrate.
- Set Up the Integration:
- For tools like Prometheus:
- Copy the API key from VictorOps.
- Update your Prometheus configuration file (
alertmanager.yml) with the VictorOps API key. - Define routing rules in the configuration file to send alerts to VictorOps.
- For tools like Datadog:
- Install the VictorOps integration from the Datadog marketplace.
- Provide your VictorOps API key in the Datadog settings.
- Test the integration by triggering an alert from Datadog.
- For tools like Prometheus:
- Test the Integration:
Trigger a sample alert from the monitoring tool to ensure it is routed correctly to VictorOps.
Step 5: Configure Alert Routing
- Define Routing Rules:
- Go to the “Routing Rules” section.
- Define rules based on alert severity, source, or specific tags.
- Route critical alerts to high-priority teams and less severe alerts to secondary teams.
- Set Up Escalations:
- Add escalation policies to ensure that unresolved alerts are automatically routed to higher-level personnel.
- Example: If a Level 1 responder doesn’t acknowledge an alert within 5 minutes, escalate it to the Level 2 team.
Step 6: Customize Notifications
VictorOps supports multi-channel notifications, including email, SMS, phone calls, and push notifications. Configure your preferences as follows:
- Go to Notification Settings:
- Access the “User Preferences” section in your profile.
- Select Notification Channels:
- Enable your preferred channels (e.g., SMS and email for critical alerts, push notifications for others).
- Set Quiet Hours (Optional):
- Define quiet hours during non-working periods.
- Specify backup contacts to handle alerts during your off-hours.
Step 7: Test Alerts and Escalations
- Trigger a Test Alert:
- Use the integrated monitoring tool or VictorOps’s built-in testing feature to send a sample alert.
- Verify Routing and Notifications:
- Check that the alert is routed to the correct team.
- Ensure all notifications (SMS, email, phone, or push) are delivered as configured.
- Simulate Escalations:
- Test the escalation policy by leaving the alert unresolved for the escalation duration.
Step 8: Explore Advanced Features
- Post-Incident Reporting:
- Use the “Reports” section to generate timelines and analyze incident response performance.
- Integrate Collaboration Tools:
- Connect VictorOps with platforms like Slack, Microsoft Teams, or Zoom for real-time collaboration during incidents.
- Set Up Automation Rules:
- Automate routine tasks or recurring incident responses using VictorOps’s workflow automation features.
Step 9: Deploy VictorOps in Production
- Monitor Performance:
- Track incident trends and response times using VictorOps analytics.
- Adjust on-call schedules and routing rules as needed.
- Optimize Configurations:
- Regularly review integration settings, routing rules, and notification preferences to ensure optimal performance.
- Train Your Team:
- Provide training sessions for team members to familiarize them with VictorOps’s features and workflows.
Basic Tutorials of VictorOps: Getting Started
- Creating On-Call Schedules
Define on-call rotations and assign team members to ensure 24/7 coverage. - Setting Up Escalation Policies
Create multi-level escalation rules to address unresolved incidents promptly. - Integrating Monitoring Tools
Connect a monitoring tool (e.g., Splunk) to VictorOps to generate actionable alerts. - Testing Alerts
Send a test alert to ensure routing and notification configurations are correct. - Collaborating During Incidents
Use built-in chat tools to enable cross-team collaboration during incident resolution. - Analyzing Incidents
Review incident timelines and generate reports to identify trends and areas for improvement.