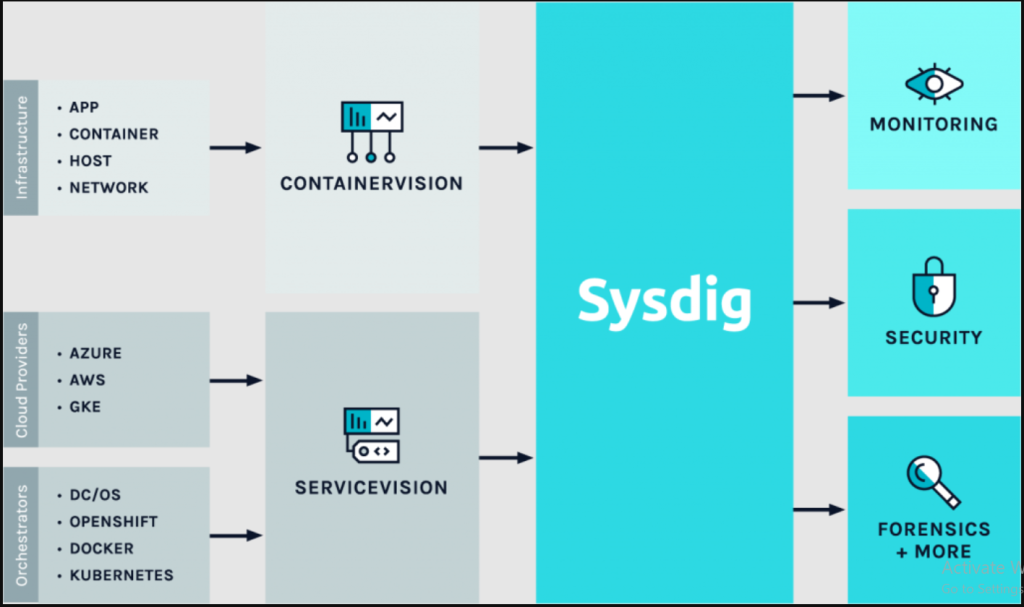
With the rise of cloud-native environments, containers, and Kubernetes, organizations need deep visibility, security, and compliance for their cloud workloads. Sysdig is a cloud-native security and monitoring platform designed to help businesses detect threats, secure workloads, and optimize performance in real time. It provides unified security, compliance, and observability for cloud infrastructure, containers, and Kubernetes.
Sysdig simplifies incident response, vulnerability scanning, runtime security, and compliance enforcement, making it a must-have tool for DevOps and security teams.
This blog will explore what Sysdig is, its use cases, features, architecture, installation, and step-by-step tutorials for getting started.
What is Sysdig?
Sysdig is an open-source and enterprise-grade platform that provides security, monitoring, and compliance for cloud-native environments. Originally started as an open-source troubleshooting tool, Sysdig has evolved into a powerful security and observability platform tailored for Kubernetes, containers, and cloud infrastructure.
Key Highlights of Sysdig:
- Container Security & Threat Detection: Monitors workloads in real time for vulnerabilities, runtime threats, and misconfigurations.
- Cloud Security Posture Management (CSPM): Ensures compliance with frameworks like PCI-DSS, NIST, SOC2, and CIS Benchmarks.
- Kubernetes & Cloud-Native Observability: Provides deep visibility into Kubernetes clusters, workloads, and network activity.
- Forensic Analysis & Incident Response: Captures system activity for post-breach investigation and threat detection.
- Runtime Security & Compliance: Detects suspicious behavior, privilege escalation, and unauthorized access attempts.
Sysdig is widely used for cloud-native security, DevSecOps, compliance monitoring, and performance optimization in AWS, Azure, Google Cloud, and hybrid cloud environments.
Top 10 Use Cases of Sysdig
1. Container Security and Runtime Threat Detection
Sysdig continuously monitors running containers and Kubernetes workloads to detect anomalies, unauthorized access, and malware attacks.
2. Kubernetes Security & Compliance
It ensures Kubernetes cluster security by enforcing policies, monitoring API calls, and identifying misconfigurations.
3. Cloud Security Posture Management (CSPM)
Sysdig detects misconfigurations in cloud services, securing IAM policies, storage buckets, network configurations, and workloads.
4. Incident Response & Forensic Analysis
It captures system calls, logs, and network traffic, enabling post-breach forensic investigations to determine the root cause of security incidents.
5. Vulnerability Scanning & Image Security
Sysdig scans container images for vulnerabilities before deployment, ensuring only secure images run in production.
6. Compliance Monitoring & Reporting
Ensures continuous compliance with industry standards like CIS, NIST, GDPR, SOC2, and PCI-DSS through automated audits and reporting.
7. Kubernetes Performance Monitoring
Monitors CPU, memory, disk, and network metrics for Kubernetes pods, nodes, and clusters, ensuring optimal performance.
8. Zero Trust Security for Containers and Workloads
Sysdig enables zero-trust policies, preventing unauthorized processes and network connections from running in containers.
9. Cloud-Native Network Security
Detects suspicious network activity, lateral movement, and container-to-container communication threats using Sysdig Falco.
10. Integration with DevOps & SIEM Tools
Sysdig integrates with Splunk, AWS Security Hub, Azure Sentinel, Prometheus, Grafana, and SIEM tools for security alerts and threat intelligence.
What Are the Features of Sysdig?
1. Real-Time Cloud and Kubernetes Security
- Detects unauthorized access, privilege escalation, and malicious activity in real time.
- Uses Sysdig Falco, an open-source runtime security tool for Kubernetes.
2. Container & Image Vulnerability Scanning
- Scans Docker images for vulnerabilities before deployment.
- Ensures compliance with security policies.
3. Threat Detection & Response
- Monitors system calls and network activity to detect security threats.
- Provides detailed forensic analysis for security incidents.
4. Kubernetes & Container Monitoring
- Tracks CPU, memory, disk, and network usage for Kubernetes pods and containers.
- Supports Prometheus and OpenTelemetry metrics collection.
5. Compliance and Audit Reporting
- Automates compliance enforcement for PCI-DSS, SOC2, HIPAA, and GDPR.
- Generates compliance reports for audits.
6. Cloud Security Posture Management (CSPM)
- Detects cloud misconfigurations and security risks in AWS, Azure, and GCP.
- Enforces least privilege policies for IAM users.
7. Kubernetes Network Security
- Monitors container-to-container network connections for suspicious traffic.
- Detects unauthorized API calls and lateral movement attacks.
8. Integration with SIEM and DevOps Tools
- Works with Splunk, AWS Security Hub, Azure Sentinel, Grafana, and Prometheus.
- Sends security alerts to Slack, PagerDuty, and Teams.
9. Runtime Security Policies
- Defines security rules using Falco policy rules to block threats.
- Prevents execution of unauthorized binaries inside containers.
10. Multi-Cloud Support & Scalability
- Works across AWS, Azure, GCP, and hybrid cloud environments.
- Scales security monitoring for large enterprises.
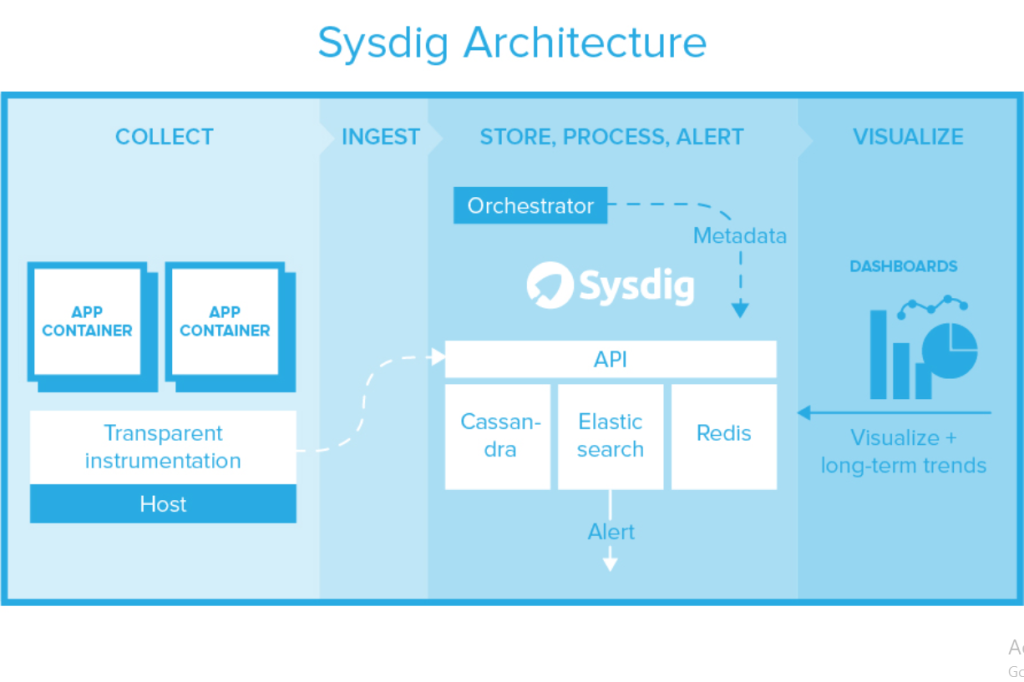
How Sysdig Works and Architecture
How Sysdig Works
Sysdig uses kernel-level monitoring to collect system activity data, analyze network traffic, and enforce security policies.
Sysdig Architecture Overview
- Sysdig Agent (Data Collector)
- Installed on Kubernetes nodes, cloud instances, and on-prem servers.
- Collects security, compliance, and performance metrics.
- Sysdig Secure (Threat Detection & Compliance)
- Uses Falco rules and machine learning to detect threats.
- Provides compliance enforcement and audit reports.
- Sysdig Monitor (Observability & Performance Monitoring)
- Tracks Kubernetes pod metrics, network activity, and resource consumption.
- Supports Prometheus and OpenTelemetry metrics.
- Sysdig Cloud (SaaS & Self-Hosted Dashboard)
- Provides centralized dashboards for security and monitoring.
- Integrates with DevOps and SIEM tools.
How to Install Sysdig
Installing Sysdig on Kubernetes
Step 1: Install Sysdig Agent
kubectl apply -f https://download.sysdig.com/kubernetes/sysdig-agent-daemonset.yamlStep 2: Verify Installation
kubectl get pods -n sysdig-agentInstalling Sysdig on Linux
Step 1: Install Sysdig
curl -s https://s3.amazonaws.com/download.draios.com/install-agent | bashStep 2: Start Sysdig
sudo systemctl start sysdig-agentStep 3: Verify Installation
sysdigBasic Tutorials of Sysdig: Getting Started
1. Running a Sysdig Security Scan
sysdig -c security_events2. Monitoring Kubernetes Cluster
sysdig -c k8s_event_count3. Filtering Logs for Suspicious Activity
sysdig -c list_login_attempts4. Setting Up Security Alerts with Falco
falco -r /etc/falco/falco_rules.yaml5. Checking Running Containers
sysdig -c containers