CyberSponse, now rebranded as DFLabs after its acquisition, is a security orchestration, automation, and response (SOAR) platform that helps organizations improve their incident response workflows and automate security operations. It provides a centralized platform to integrate various security tools, streamline processes, and enhance collaboration among security teams. CyberSponse allows for the creation of automated workflows for detecting, investigating, and responding to cybersecurity threats, reducing manual effort, improving efficiency, and accelerating response times. The platform supports real-time alerts, incident tracking, and reporting, making it easier for organizations to manage and respond to security incidents in a coordinated manner.
CyberSponse is widely used across industries like finance, healthcare, and government for incident management, threat intelligence integration, and compliance reporting. It helps security operations teams automate repetitive tasks, such as data enrichment and threat analysis, enabling them to focus on more complex and critical issues. Its integration with various security tools like SIEMs, firewalls, and endpoint protection systems also makes it valuable for security operations centers (SOCs) in enhancing the effectiveness of their threat detection and response capabilities. Overall, CyberSponse is critical in improving security posture by reducing response times and ensuring more consistent and accurate handling of security incidents.
What is CyberSponse?
CyberSponse is a SOAR platform designed to streamline and automate security operations. It integrates with an organization’s existing security tools, providing a centralized interface to manage incidents, automate workflows, and enhance collaboration among security teams. CyberSponse helps organizations handle the growing complexity of cybersecurity threats by improving the speed and efficiency of incident response.
Key Characteristics of CyberSponse:
- Automation-Driven: Reduces manual intervention by automating repetitive security tasks.
- Centralized Platform: Combines incident management, case management, and workflow orchestration into one solution.
- Customizable Playbooks: Allows teams to create tailored workflows to address specific threats.
- Tool Integration: Works seamlessly with SIEMs, firewalls, endpoint detection tools, and more.
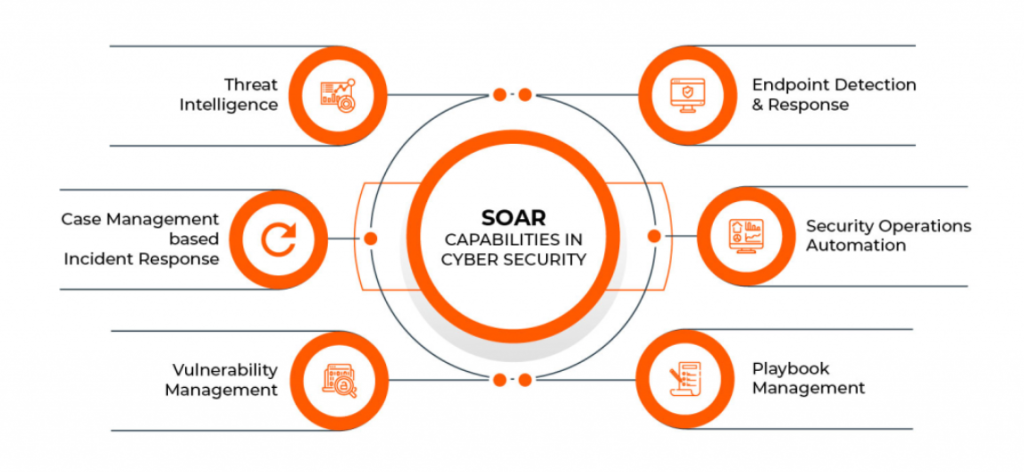
Top 10 Use Cases of CyberSponse
- Incident Response Automation
- Automates the investigation and response to security incidents, reducing time to resolution.
- Threat Intelligence Management
- Aggregates threat intelligence feeds and correlates data with incidents to prioritize and address threats effectively.
- Phishing Response
- Automates the identification and remediation of phishing attacks, reducing the burden on security analysts.
- Malware Analysis
- Orchestrates sandbox analysis and automates containment and remediation workflows for malware incidents.
- Vulnerability Management
- Integrates with vulnerability scanners to prioritize and remediate vulnerabilities based on risk levels.
- Compliance Reporting
- Automates the generation of reports to ensure compliance with regulations like GDPR, HIPAA, and PCI-DSS.
- Endpoint Security Orchestration
- Coordinates endpoint protection tools to quarantine compromised devices and prevent lateral movement.
- SIEM Integration and Alert Management
- Enriches and triages alerts from SIEM tools, helping analysts focus on high-priority incidents.
- Security Policy Enforcement
- Automates the application of security policies across the organization’s tools and environments.
- Collaboration and Team Coordination
- Facilitates collaboration between security teams with case management and automated workflows.
Features of CyberSponse
- Automated Playbooks – Predefined and customizable playbooks automate incident response workflows.
- Real-Time Collaboration – Enables teams to collaborate on cases in real-time for faster resolution.
- Comprehensive Integration – Connects with hundreds of security tools, including SIEMs, EDRs, and threat intelligence platforms.
- Case Management – Tracks and manages incidents from detection to resolution.
- Drag-and-Drop Workflow Builder – Simplifies the creation of custom workflows without coding.
- Threat Intelligence Integration – Enriches incidents with actionable threat intelligence.
- Dashboard and Reporting – Provides detailed analytics and reports on incident trends and team performance.
- Role-Based Access Control (RBAC) – Ensures secure and controlled access to sensitive data.
- Multi-Tenancy – Supports multiple environments for MSSPs and large organizations.
- Scalability – Handles large volumes of alerts and incidents for enterprise-scale security operations.
How CyberSponse Works and Architecture
1. Integration Layer
CyberSponse integrates with existing security tools such as SIEMs, firewalls, endpoint detection systems, and threat intelligence platforms to aggregate data and trigger workflows.
2. Playbook Execution
Playbooks automate security workflows by defining a series of actions for specific incident types, such as quarantining a device or blocking an IP.
3. Case Management
The platform centralizes incident management, allowing analysts to track progress, collaborate, and close cases efficiently.
4. Orchestration Layer
CyberSponse orchestrates workflows across tools, ensuring seamless communication between systems and automating repetitive tasks.
5. Analytics and Reporting
CyberSponse provides dashboards and reports to monitor security trends, team performance, and compliance metrics.
How to Install CyberSponse
CyberSponse now rebranded as DFLabs, is a Security Orchestration, Automation, and Response (SOAR) platform, and typically, it is deployed on enterprise environments using a web-based interface or cloud service. Since CyberSponse is an enterprise-grade solution, it doesn’t follow the typical “install in code” style like open-source software. Instead, it is typically installed on a server, with the necessary configuration done via the platform’s user interface or API. Below is a general guide on how to set up DFLabs (formerly CyberSponse) in your environment:
1. Sign Up and Access DFLabs (CyberSponse)
To use DFLabs (CyberSponse), you will need to sign up for an account or request a demo through the DFLabs website.
- Visit the DFLabs website: DFLabs
- Contact the sales or support team to get access to the platform.
For on-premise installation or self-hosted setups, you will likely need to engage directly with the DFLabs team for access to the software and a license.
2. Install CyberSponse (DFLabs) Platform
DFLabs (formerly CyberSponse) can be installed either on-premises or accessed via their cloud platform. The on-premise installation process typically involves these steps:
- On-Premise Installation: This will require you to have a dedicated server or virtual machine. The DFLabs team typically provides an installation package and documentation for setting up the platform on your own infrastructure.
- Cloud Platform: Alternatively, you can opt for the cloud version where DFLabs is hosted on cloud infrastructure (AWS, Azure, etc.), and there is no installation required on your local servers. This version allows you to access the platform via the web interface.
3. System Requirements
Before installing, ensure the system meets DFLabs’ hardware and software requirements:
- Operating System: DFLabs may require specific Linux-based distributions (like CentOS or Ubuntu) or Windows Server environments.
- Dependencies: Ensure you have necessary dependencies like Python, Docker (for containerized environments), or PostgreSQL database if required for the setup.
- Firewall and Ports: Ensure necessary ports are open for communication between your internal security tools (SIEM, firewalls, etc.) and the DFLabs platform.
4. Use DFLabs APIs for Integration
Once installed and set up, you can integrate CyberSponse with your other security tools using DFLabs’ APIs for automation and orchestration.
For example, to interact with the API, you would typically use authentication tokens and perform API calls to fetch or manipulate incidents. Here’s an example of using Python to interact with the DFLabs (CyberSponse) API:
import requests
# Define the API URL and token
base_url = "https://your-cybersponse-instance.com/api/v1"
api_token = "your_api_token_here"
headers = {
"Authorization": f"Bearer {api_token}",
"Content-Type": "application/json"
}
# Example: Fetch incidents
response = requests.get(f"{base_url}/incidents", headers=headers)
if response.status_code == 200:
incidents = response.json()
print("Incidents:", incidents)
else:
print("Failed to fetch incidents", response.status_code)
Replace your-cybersponse-instance.com with your actual instance URL, and provide your API token for authentication.
5. Configure Playbooks and Workflows
After installation, you will need to configure playbooks and automated workflows for managing security incidents. DFLabs provides an intuitive interface to design playbooks that can be customized based on your organization’s response procedures.
Steps to create and configure workflows:
- Define your incident response plans using the built-in editor.
- Automate repetitive tasks such as data enrichment, threat intelligence lookup, or generating tickets.
- Integrate with external systems such as SIEMs, endpoint protection, and firewall systems to automatically gather data and initiate responses based on predefined triggers.
6. Monitoring and Reporting
After the system is set up and integrated with your security tools, you can use the DFLabs dashboard to monitor ongoing incidents, generate reports, and track your security operations.
7. Maintenance and Updates
Regularly check for updates or patches from DFLabs to ensure your platform remains secure and up-to-date. Most cloud versions will update automatically, but for on-premise setups, you may need to manually install patches or upgrades.
Basic Tutorials of CyberSponse: Getting Started
Step 1: Log In to the Dashboard
- Access the CyberSponse platform using your credentials and explore the interface.
Step 2: Add Integrations
- Navigate to the integrations section and connect security tools, such as SIEMs, firewalls, and threat intelligence feeds.
Step 3: Create a Playbook
- Go to the Playbook Builder.
- Drag and drop actions (e.g., quarantine, block IP) to define the workflow for specific incident types.
Step 4: Automate a Response
- Assign the playbook to an incident type (e.g., phishing) to automatically trigger workflows when such incidents are detected.
Step 5: Monitor Cases
- Use the case management dashboard to track active incidents, collaborate with team members, and resolve cases.
Step 6: Generate Reports
- Access the reporting section to generate compliance and performance reports.