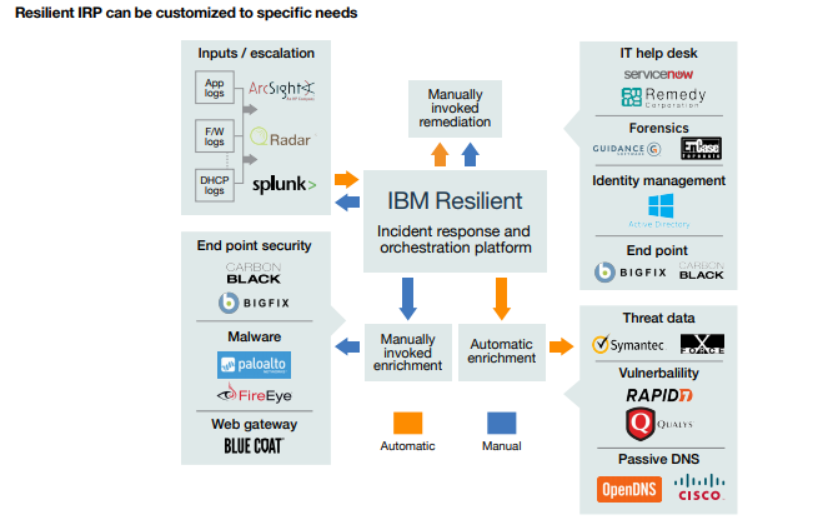
IBM Resilient is a comprehensive security orchestration, automation, and response (SOAR) platform that helps organizations manage and respond to security incidents efficiently. It automates incident response workflows, integrates with various security tools, and provides real-time visibility into threats, enabling faster and more coordinated reactions. IBM Resilient streamlines the entire incident management lifecycle, from detection and analysis to resolution and reporting, improving response times and reducing manual effort.
Use cases for IBM Resilient include automating incident response, integrating threat intelligence, incident tracking and reporting, and compliance management. It is widely used in security operations centers (SOCs), financial institutions, and government organizations to enhance security posture, reduce operational risks, and improve regulatory compliance.
What is IBM Resilient?
IBM Resilient is a SOAR platform that enhances an organization’s ability to detect, respond to, and recover from cybersecurity incidents. It integrates seamlessly with existing security tools to provide automated and orchestrated workflows, helping organizations reduce response times, mitigate threats, and improve overall security posture.
Key Characteristics of IBM Resilient:
- Orchestration and Automation: Simplifies incident response through automated playbooks and integrations.
- Centralized Management: Provides a unified platform for tracking, managing, and resolving incidents.
- Scalability: Suitable for organizations of all sizes, from small businesses to large enterprises.
- Compliance: Helps organizations meet regulatory requirements by providing detailed audit trails and reporting.
Top 10 Use Cases of IBM Resilient
- Incident Response Automation
- Automates repetitive tasks, such as triaging and assigning incidents, to improve response times.
- Phishing Detection and Response
- Identifies and mitigates phishing attacks by analyzing suspicious emails and automating remediation.
- Malware Analysis and Containment
- Integrates with malware analysis tools to automate the containment and remediation of infected systems.
- Threat Intelligence Enrichment
- Aggregates threat intelligence from multiple sources to enrich incident data and improve decision-making.
- Security Event Triage
- Prioritizes and escalates security alerts based on predefined criteria, ensuring critical incidents are addressed promptly.
- Vulnerability Management
- Automates the process of identifying, prioritizing, and mitigating vulnerabilities.
- Compliance and Audit Readiness
- Generates detailed reports and maintains audit trails for regulatory compliance, such as GDPR and HIPAA.
- Data Breach Management
- Provides workflows for managing data breaches, including notification processes and legal reporting.
- Endpoint Threat Detection and Response
- Coordinates with endpoint detection tools to isolate compromised devices and prevent lateral movement.
- Collaboration and Communication
- Facilitates cross-team collaboration and communication during incident resolution.
Features of IBM Resilient
- Automated Playbooks – Predefined and customizable workflows automate incident response processes.
- Case Management – Centralized case management system for tracking and resolving incidents.
- Threat Intelligence Integration – Connects with threat intelligence platforms to enrich incident data.
- Real-Time Dashboards – Provides real-time visibility into incident trends and team performance.
- Integration Ecosystem – Supports integration with SIEMs, EDRs, and other security tools.
- Drag-and-Drop Workflow Builder – Simplifies the creation of custom workflows.
- Multi-Tenancy Support – Allows Managed Security Service Providers (MSSPs) to support multiple clients.
- Compliance Support – Helps organizations maintain compliance with regulations by providing detailed audit trails.
- AI-Powered Insights – Leverages machine learning to identify patterns and predict potential threats.
- Mobile Accessibility – Enables incident management on the go via mobile devices.
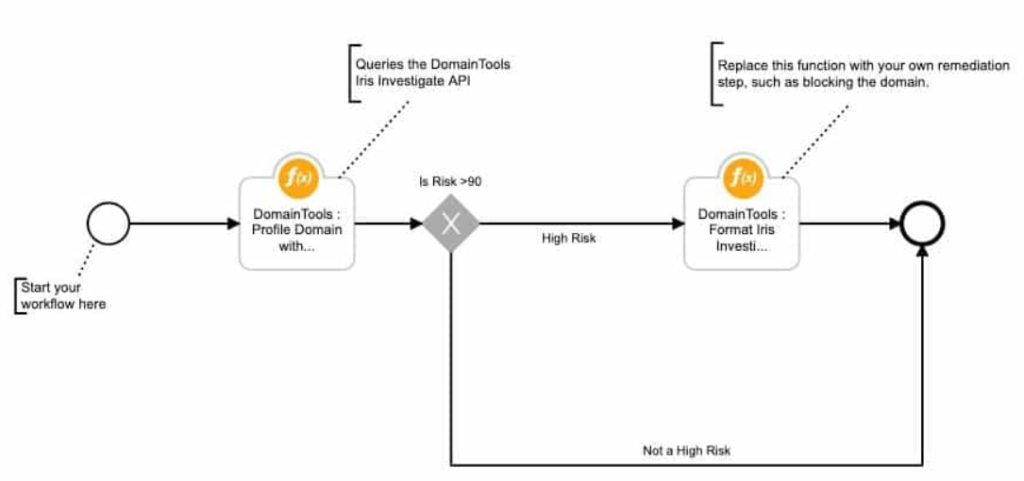
How IBM Resilient Works and Architecture
1. Integration Layer
IBM Resilient connects with an organization’s existing security tools, such as SIEMs, firewalls, and endpoint protection platforms, to gather and analyze data.
2. Workflow Automation
Incident response workflows are defined using automated playbooks, which can execute tasks such as data enrichment, threat containment, and communication.
3. Case Management
The platform provides a centralized hub for managing incidents, tracking progress, and maintaining detailed records for auditing and compliance.
4. Orchestration Engine
IBM Resilient orchestrates actions across integrated tools, ensuring seamless communication and execution of tasks.
5. Reporting and Analytics
The platform offers advanced reporting and analytics features to monitor incident trends, team performance, and compliance metrics.
How to Install IBM Resilient
IBM Resilient, now part of the IBM Security suite, is a Security Orchestration, Automation, and Response (SOAR) platform that helps organizations manage and automate their security incident response processes. IBM Resilient is typically deployed and managed via its web-based interface and configuration tools, but it also supports integration and automation through APIs.
While the installation of IBM Resilient is not done directly “in code,” it can be programmatically integrated into your security infrastructure once it is set up. Here’s a guide to help you understand the process of installing IBM Resilient and integrating it programmatically.
Steps to Install IBM Resilient
1. Obtain IBM Resilient
- Trial or Purchase: First, sign up for a trial or purchase IBM Resilient through the IBM Security website. You will need an active license to deploy the solution.
- Cloud or On-Premise: You can choose either a cloud-based deployment or an on-premises installation based on your needs.
2. Set Up IBM Resilient (Web Interface)
- Cloud-based: If you choose the cloud option, IBM Resilient will be hosted in IBM Cloud, and you can access it via your browser. You’ll only need to configure your system (e.g., user permissions, integrations).
- On-premise: For on-premise setups, follow the installation guide that IBM provides after purchasing the solution. It involves setting up a server, installing necessary dependencies (like Java), and configuring the environment.
3. Configure IBM Resilient
After installing or accessing IBM Resilient, you’ll need to configure:
- Security Playbooks: Define workflows for incident response.
- Integrations: Connect Resilient with external security tools such as SIEMs, firewalls, endpoint protection, and more.
4. Using IBM Resilient REST API for Integration
Once IBM Resilient is installed, you can use its REST API to integrate the platform with your other tools or automate processes. Here’s how to interact with IBM Resilient programmatically:
API Authentication:
To interact with the IBM Resilient API, you’ll first need an authentication token. Here’s an example of how to authenticate and interact with the IBM Resilient API:
import requests
# IBM Resilient API URL
base_url = "https://your-resilient-instance.com/api"
# API credentials (usually obtained from your IBM Resilient admin)
api_user = "your_username"
api_password = "your_password"
# Basic authentication for API requests
response = requests.get(f"{base_url}/incidents", auth=(api_user, api_password))
# Check the response status
if response.status_code == 200:
incidents = response.json()
print("Incidents:", incidents)
else:
print("Error:", response.status_code, response.text)
Example: Create a New Incident
You can use the IBM Resilient API to create new incidents programmatically. Here’s an example of creating a new incident using Python:
incident_data = {
"name": "New Security Incident",
"description": "Suspicious activity detected in the network",
"severity": "High",
"status": "New"
}
response = requests.post(
f"{base_url}/incidents",
auth=(api_user, api_password),
json=incident_data
)
if response.status_code == 201:
print("Incident created successfully:", response.json())
else:
print("Failed to create incident:", response.status_code, response.text)
Example: Retrieve Incident Details
To get details of a specific incident, you can use the incident ID to make a GET request:
incident_id = 12345 # Example incident ID
response = requests.get(f"{base_url}/incidents/{incident_id}", auth=(api_user, api_password))
if response.status_code == 200:
incident = response.json()
print("Incident Details:", incident)
else:
print("Error fetching incident:", response.status_code, response.text)
5. Advanced API Integrations
- Automate Playbook Execution: Trigger automated playbooks for incident response.
- Integrate Threat Intelligence: Pull threat data from external feeds and integrate it into IBM Resilient.
- Data Enrichment: Enrich incident data by integrating external sources such as threat intelligence platforms or vulnerability databases.
6. Monitor and Automate Workflows
- Use IBM Resilient’s API to monitor ongoing incidents, automate responses, and integrate with other systems for data sharing, alerting, and remediation.
Basic Tutorials of IBM Resilient: Getting Started
Step 1: Access the Dashboard
- Log in to the IBM Resilient platform using your credentials.
- Explore the dashboard to view incident trends and team activity.
Step 2: Configure Integrations
- Navigate to the Integrations section.
- Add and configure integrations with your existing security tools (e.g., SIEMs, threat intelligence platforms).
Step 3: Create a Playbook
- Go to the Playbook Builder and select Create New Playbook.
- Use the drag-and-drop interface to define actions, triggers, and workflows for specific incident types.
Step 4: Automate Incident Response
- Assign a playbook to a specific incident type (e.g., phishing or malware).
- Enable automation to trigger workflows based on incident detection.
Step 5: Monitor and Resolve Incidents
- Use the Case Management dashboard to track and manage incidents.
- Collaborate with team members to resolve cases and update incident statuses.
Step 6: Generate Reports
- Access the Reports section to generate custom reports on incident trends, SLA compliance, and team performance.