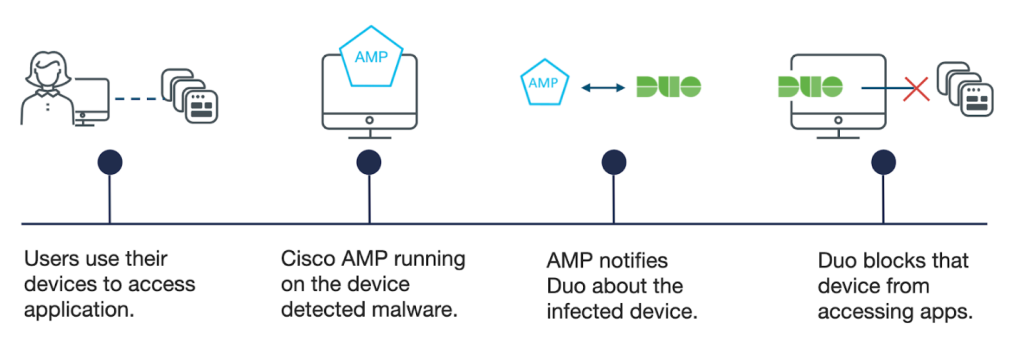
Cisco AMP for Endpoints (Advanced Malware Protection) is a security solution designed to detect, prevent, and respond to advanced threats targeting endpoints, such as desktops, laptops, and mobile devices. It combines signature-based detection, behavioral analysis, and machine learning to identify known and unknown threats. Cisco AMP offers real-time threat intelligence, continuous monitoring, and automated response capabilities to mitigate risks and reduce the impact of cyberattacks. It integrates with other Cisco security products, providing a unified defense strategy.
Use cases for Cisco AMP for Endpoints include malware detection and prevention, where it protects against a wide range of threats like viruses, ransomware, and fileless attacks; endpoint visibility, providing detailed insights into activities and potential security incidents; incident response, enabling security teams to investigate and remediate threats quickly; and compliance management, ensuring that endpoints adhere to organizational security policies and regulatory standards. It is widely used across industries like finance, healthcare, and education to safeguard endpoints from evolving cyber threats.
What is Cisco AMP for Endpoints?
Cisco AMP for Endpoints is an endpoint protection platform that leverages cloud-based analytics, continuous monitoring, and retrospective security to defend against advanced threats. By monitoring endpoints in real time and analyzing behaviors, it enables organizations to prevent, detect, and respond to attacks more effectively.
Key Characteristics of Cisco AMP for Endpoints:
- Behavioral Analytics: Identifies malicious activity based on file behavior rather than just file signatures.
- Retrospective Security: Tracks and analyzes threats over time, even after initial detection.
- Cloud-Native Architecture: Uses cloud-based threat intelligence and analytics for real-time protection.
- Integration with Cisco SecureX: Provides centralized management and enhanced threat response capabilities.
Top 10 Use Cases of Cisco AMP for Endpoints
- Advanced Malware Detection
- Detects and prevents malware, including zero-day threats, using machine learning and threat intelligence.
- Ransomware Protection
- Protects endpoints against ransomware attacks by blocking suspicious file behaviors.
- Fileless Threat Detection
- Identifies and mitigates fileless attacks by monitoring memory processes and script behaviors.
- Threat Hunting
- Enables security teams to proactively hunt for potential threats across the endpoint environment.
- Incident Response
- Provides real-time visibility and detailed forensic data to streamline investigation and remediation.
- Behavioral Monitoring
- Monitors endpoint activity in real time to detect anomalous behaviors that could indicate an attack.
- Retrospective Analysis
- Reanalyzes previously observed files to uncover threats that were initially classified as benign.
- Cloud Security Integration
- Protects cloud-based endpoints and integrates seamlessly with cloud security solutions.
- Policy Enforcement
- Ensures consistent application of security policies across endpoints to reduce risks.
- Compliance and Reporting
- Generates detailed reports for compliance purposes and security audits.
Features of Cisco AMP for Endpoints
- Advanced Threat Detection – Leverages Cisco Talos threat intelligence to identify and block known and emerging threats.
- Continuous Monitoring and Recording – Tracks all endpoint activity for real-time detection and retrospective analysis.
- Exploit Prevention – Protects against vulnerabilities in applications and operating systems.
- File Analysis and Sandbox – Analyzes suspicious files in a secure environment to detect hidden threats.
- Retrospective Security – Reassesses previously scanned files to detect delayed or evolving threats.
- Cloud-Native Platform – Provides centralized, scalable protection with cloud-based analytics.
- Endpoint Isolation – Quarantines compromised devices to prevent lateral movement of threats.
- Integration with SecureX – Enhances visibility and automation across Cisco’s security ecosystem.
- Custom Detection Rules – Allows administrators to create tailored detection rules for specific threats.
- Detailed Reporting and Dashboards – Offers actionable insights and analytics for better security posture management.
How Cisco AMP for Endpoints Works and Architecture
1. Cloud-Based Threat Intelligence
Cisco AMP for Endpoints uses Cisco Talos threat intelligence, one of the largest threat intelligence organizations globally, to continuously update its detection capabilities.
2. Endpoint Agents
Lightweight agents installed on endpoints monitor activities, detect threats, and enforce security policies.
3. Continuous Monitoring
AMP continuously records all endpoint activity, enabling real-time detection and retrospective analysis of suspicious behaviors.
4. Retrospective Security
Even after files are initially scanned, AMP tracks them over time. If a file’s behavior changes or a new threat signature is discovered, AMP can retrospectively block and remediate the threat.
5. Integration with SecureX
Cisco AMP integrates with the SecureX platform to provide a unified security ecosystem, enabling faster detection, automated responses, and improved threat visibility.
How to Install Cisco AMP for Endpoints
To install Cisco AMP for Endpoints programmatically, you typically follow these steps, leveraging the AMP for Endpoints installer and using deployment scripts or tools. The installation process itself isn’t purely “code-based,” but it can be automated using command-line tools or scripting languages like PowerShell for Windows and Bash for Linux.
Here’s how you can install Cisco AMP for Endpoints using command-line options and automate the process.
1. Obtain Cisco AMP for Endpoints Installer
- You can download the Cisco AMP for Endpoints installer from the Cisco Threat Response portal or the Cisco Security website. You will need a valid Cisco AMP for Endpoints subscription to access the installer.
2. System Requirements
Ensure that your system meets the minimum requirements for running Cisco AMP for Endpoints:
- Operating System: Windows (7, 8.1, 10, Server 2012, 2016) or Linux (various distros).
- Memory: Minimum of 2 GB of RAM (4 GB recommended).
- Disk Space: Minimum 1 GB free.
3. Install Cisco AMP for Endpoints on Windows (Command Line)
Cisco AMP for Endpoints can be installed silently on Windows using the command-line options.
Example of Silent Installation on Windows:
Download the AMP for Endpoints installer (e.g., ampagent_installer.exe) and run the following command in PowerShell or Command Prompt:
# Run the installer silently with the following arguments
Start-Process -FilePath "C:\path\to\ampagent_installer.exe" -ArgumentList "/quiet /install" -Wait
/quiet: Ensures the installation runs without any UI prompts (silent installation)./install: Executes the installation process.
This command will install Cisco AMP for Endpoints on the machine without requiring further user interaction.
4. Install Cisco AMP for Endpoints on Linux (Command Line)
For Linux systems, the process involves using the appropriate .rpm or .deb installer packages.
Example: For CentOS/RHEL (RPM-based Systems):
sudo rpm -ivh ampagent_installer.rpm
Example: For Ubuntu/Debian (DEB-based Systems):
sudo dpkg -i ampagent_installer.deb
These commands will install Cisco AMP for Endpoints on Linux systems. If necessary, you may need to resolve any dependency issues using:
sudo apt-get install -f # For Ubuntu/Debian systems
5. Verify Installation
After installation, you can verify if the AMP agent is running correctly. On Windows, you can check the Task Manager for the ampagent process or use PowerShell:
Get-Process | Where-Object { $_.Name -like "ampagent" }
On Linux, you can verify the status of the AMP agent with:
ps aux | grep ampagent
6. Automate Installation on Multiple Machines (Using PowerShell for Windows)
If you need to deploy Cisco AMP for Endpoints to multiple Windows machines, you can automate the installation using a PowerShell script. For example:
# List of remote computers
$computers = Get-Content -Path "C:\computers.txt"
# Loop through each computer and install AMP agent
foreach ($computer in $computers) {
Invoke-Command -ComputerName $computer -ScriptBlock {
Start-Process -FilePath "C:\path\to\ampagent_installer.exe" -ArgumentList "/quiet /install" -Wait
}
}
This script reads a list of machine names from computers.txt and installs the AMP agent remotely.
7. Monitor and Manage Cisco AMP for Endpoints
After installation, Cisco AMP for Endpoints should automatically register with your Cisco AMP console for centralized management. You can use the Cisco AMP for Endpoints Dashboard to monitor and manage endpoints, configure policies, and receive alerts.
8. Advanced Configuration with AMP APIs
If you’re looking to automate configuration, reporting, or policy management, Cisco provides APIs that can be used to interact with the AMP for Endpoints service. Here’s an example of how you might use the API to retrieve device status:
import requests
# Define your API endpoint and key
api_url = "https://api.amp.cisco.com/v1/endpoints"
api_key = "your_api_key_here"
# Set headers for API request
headers = {
"Authorization": f"Bearer {api_key}",
"Content-Type": "application/json"
}
# Fetch endpoint data
response = requests.get(api_url, headers=headers)
if response.status_code == 200:
endpoints = response.json()
print("Endpoints:", endpoints)
else:
print("Error fetching data", response.status_code)
Replace your_api_key_here with the actual API key from your Cisco AMP account.
Basic Tutorials of Cisco AMP for Endpoints: Getting Started
Step 1: Log in to the Console
- Use your Cisco credentials to access the AMP for Endpoints management console.
Step 2: Add Endpoints
- Download the AMP agent installer from the console.
- Install the agent on devices and ensure they connect to the AMP cloud.
Step 3: Configure Policies
- Navigate to the Policies section.
- Set up policies for malware detection, quarantine actions, and behavioral monitoring.
Step 4: Monitor Threats
- Use the Dashboard to view detected threats, endpoint activity, and security alerts.
Step 5: Incident Response
- Isolate affected endpoints from the network to contain threats.
- Use forensic tools in the console to investigate and remediate the issue.
Step 6: Generate Reports
- Access the reporting feature to create detailed reports for compliance and security posture analysis.