SentinelOne is a cutting-edge cybersecurity platform that provides endpoint protection, detection, and response through AI-driven threat prevention and real-time monitoring. As an autonomous endpoint security solution, SentinelOne combines next-generation antivirus (NGAV), endpoint detection and response (EDR), and extended detection and response (XDR) capabilities. It is designed to protect endpoints against a wide range of threats, including malware, ransomware, fileless attacks, and advanced persistent threats (APTs).
What is SentinelOne?
SentinelOne is an AI-powered endpoint security platform designed to detect, prevent, and respond to cyber threats across endpoint devices. Its autonomous capabilities allow organizations to defend against known and unknown threats with minimal human intervention. By leveraging machine learning, SentinelOne provides real-time visibility and automated remediation, ensuring a robust and scalable cybersecurity framework.
Key Characteristics of SentinelOne:
- Autonomous Threat Prevention: Uses AI to detect and block threats in real-time.
- Behavioral Analysis: Identifies malicious activities based on file and process behaviors.
- Extended Detection and Response (XDR): Provides visibility and security across endpoints, cloud workloads, and IoT devices.
- Rapid Response and Remediation: Automates containment, remediation, and rollback of malicious activities.
Top 10 Use Cases of SentinelOne
- Next-Generation Antivirus (NGAV)
- Protects against malware, ransomware, and fileless attacks with signature-less detection.
- Endpoint Detection and Response (EDR)
- Provides real-time monitoring, threat detection, and incident response capabilities.
- Ransomware Protection
- Detects and prevents ransomware attacks using behavioral analysis and automated rollback.
- Zero-Day Threat Detection
- Identifies and mitigates previously unknown vulnerabilities and threats.
- Threat Hunting
- Allows security teams to proactively search for potential threats across endpoint environments.
- IoT Security
- Secures Internet of Things (IoT) devices by monitoring activity and detecting anomalies.
- Cloud Workload Protection
- Protects cloud-hosted workloads and containers against cyber threats.
- Incident Response Automation
- Automates threat containment and remediation, reducing the need for manual intervention.
- Regulatory Compliance
- Simplifies compliance with regulations like GDPR, HIPAA, and PCI-DSS by providing detailed reporting and audit trails.
- Integration with SIEM and SOAR
- Enhances security operations by integrating with tools like Splunk, QRadar, and ServiceNow.
Features of SentinelOne
- AI-Powered Threat Prevention – Detects and blocks threats using machine learning and behavioral analysis.
- Automated Remediation – Isolates compromised endpoints, removes malicious files, and rolls back changes automatically.
- Extended Detection and Response (XDR) – Provides visibility and protection across endpoints, cloud workloads, and IoT devices.
- Forensic Data Collection – Captures detailed forensic data for incident analysis and reporting.
- Real-Time Visibility – Offers a centralized dashboard for monitoring endpoint activities and security alerts.
- Attack Surface Reduction – Enforces policies to minimize the attack surface of endpoints.
- Threat Intelligence Integration – Leverages global threat intelligence to stay updated on emerging threats.
- Cloud-Native Architecture – Provides scalable, cloud-based deployment options with minimal system resource impact.
- Custom Detection Rules – Allows organizations to create and enforce tailored security rules.
- Seamless Integration – Works with SIEM, SOAR, and other third-party tools for enhanced security operations.
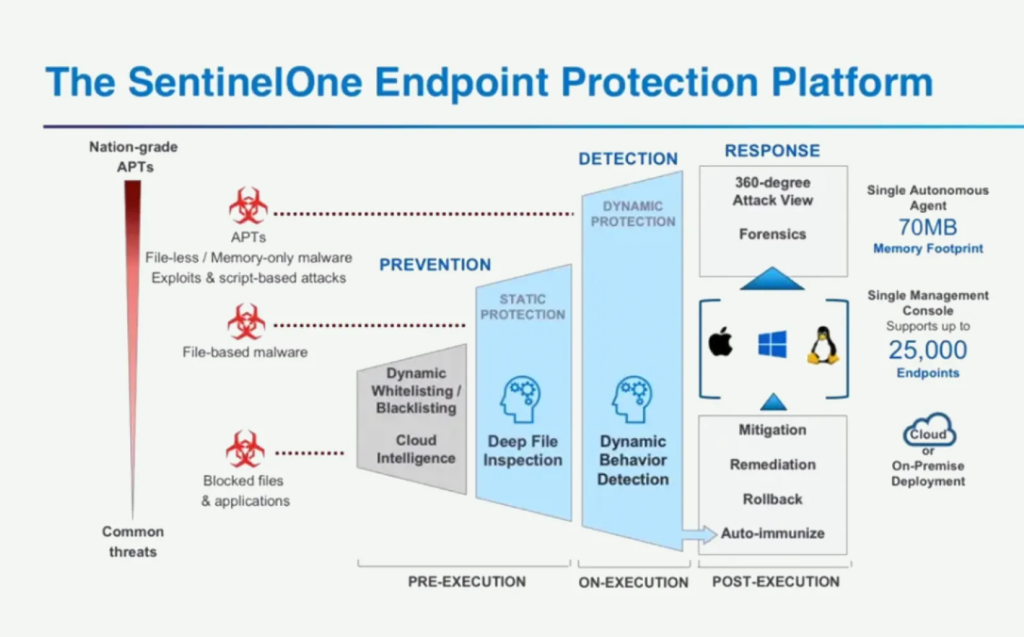
How SentinelOne Works and Architecture
1. Lightweight Agent
SentinelOne uses a lightweight agent installed on endpoints to monitor activity, detect threats, and enforce security policies. The agent operates autonomously, requiring minimal network bandwidth and system resources.
2. AI-Driven Detection
The platform employs machine learning and behavioral analysis to identify malicious activities based on file and process behaviors, eliminating reliance on traditional signature-based methods.
3. Autonomous Remediation
SentinelOne automatically contains and remediates threats without manual intervention. It can also roll back malicious changes to restore the system to a clean state.
4. Centralized Management Console
A single console provides administrators with visibility into endpoint activity, threat detections, and remediation actions across the organization.
5. Cloud and On-Premises Support
SentinelOne supports both cloud-hosted and on-premises deployments, providing flexibility to meet diverse business needs.
How to Install SentinelOne
To install SentinelOne on endpoints programmatically, you typically need to download the appropriate installer package from the SentinelOne Management Console. Then, you can use command-line options or scripts to automate the installation on multiple systems. SentinelOne provides a straightforward method for deploying its endpoint protection solution, but the process involves obtaining an installer, configuring it, and running it on the target systems.
Here is a guide to help you install SentinelOne using code, focusing on both Windows and Linux systems.
Steps to Install SentinelOne Programmatically
1. Obtain the SentinelOne Installer
- Sign in to the SentinelOne Management Console.
- Download the appropriate installer for Windows or Linux (depending on your environment). You can download installers from the “Downloads” section of the console.
2. Install SentinelOne on Windows (Command Line)
For Windows systems, you can run a silent installation using the downloaded SentinelOne installer.
Step 1: Download the SentinelOne Installer for Windows
Download the Windows installer package (usually an .exe file).
Step 2: Install SentinelOne Silently
You can run the installer silently via the Command Prompt or PowerShell with the /quiet flag to avoid any user interaction. Here’s how you can do it:
# Silent installation of SentinelOne on Windows
Start-Process -FilePath "C:\path\to\SentinelOneInstaller.exe" -ArgumentList "/quiet" -Wait
/quiet: Runs the installer silently without user input or prompts.-Wait: Ensures the script waits for the installation to complete before proceeding.
Step 3: Verify Installation
After the installation is complete, you can verify if SentinelOne is running by checking for the SentinelOne Service:
Get-Service -Name "SentinelAgent"
Alternatively, check if the SentinelOne agent is listed in Task Manager.
3. Install SentinelOne on Linux (Command Line)
For Linux systems, SentinelOne provides .deb and .rpm packages for installation.
Step 1: Download the SentinelOne Installer for Linux
Download the appropriate .deb or .rpm package for Linux from the SentinelOne Management Console.
Step 2: Install SentinelOne Silently (RPM-based Systems)
For RPM-based systems (e.g., CentOS, RHEL, Fedora), use the following command:
sudo rpm -ivh sentinelone-installer.rpm
Step 3: Install SentinelOne Silently (DEB-based Systems)
For DEB-based systems (e.g., Ubuntu, Debian), use this command:
sudo dpkg -i sentinelone-installer.deb
Step 4: Verify Installation
After installation, you can verify the status of the SentinelOne Agent on Linux:
sudo systemctl status sentinel-agent
Or check for the running processes:
ps aux | grep sentinel
4. Automate Installation on Multiple Machines (Windows Example)
You can use PowerShell to automate the deployment of SentinelOne across multiple Windows machines. Here’s an example of how to automate installation on remote computers.
Step 1: Create a List of Computers
Create a text file (computers.txt) with the list of target computers:
computer1
computer2
computer3
Step 2: PowerShell Script for Remote Installation
# List of computers to install SentinelOne
$computers = Get-Content -Path "C:\computers.txt"
foreach ($computer in $computers) {
Invoke-Command -ComputerName $computer -ScriptBlock {
Start-Process -FilePath "C:\path\to\SentinelOneInstaller.exe" -ArgumentList "/quiet" -Wait
}
}
This script reads from computers.txt and installs SentinelOne on each machine in the list.
5. Automate Installation on Multiple Machines (Linux Example)
For Linux, you can use SSH or Ansible to automate the installation of SentinelOne across multiple machines.
Step 1: Using SSH
You can create a Bash script to automate installation on remote Linux machines via SSH:
#!/bin/bash
# List of servers
servers=("server1" "server2" "server3")
# Path to SentinelOne installer
installer="/path/to/sentinelone-installer.rpm"
# Install on each server
for server in "${servers[@]}"
do
ssh user@$server "sudo rpm -ivh $installer"
done
This script remotely connects to each server listed and installs SentinelOne.
Step 2: Using Ansible
Alternatively, you can use Ansible to automate the installation of SentinelOne across a fleet of Linux machines. Here’s an example playbook:
- name: Install SentinelOne
hosts: all
become: yes
tasks:
- name: Install SentinelOne
rpm:
name: /path/to/sentinelone-installer.rpm
state: present
This Ansible playbook installs SentinelOne on all the machines specified in your inventory.
6. Monitor and Manage SentinelOne
Once the SentinelOne agents are installed, you can manage and monitor them through the SentinelOne Management Console. The console allows you to:
- View agent statuses.
- Configure security policies.
- Perform incident response tasks.
Basic Tutorials of SentinelOne: Getting Started
Step 1: Log in to the SentinelOne Console
- Use your admin credentials to access the management dashboard and explore its features.
Step 2: Deploy Agents
- Download the SentinelOne agent installer from the console.
- Deploy the agent on endpoint devices and verify connectivity.
Step 3: Configure Policies
- Navigate to the Policy section.
- Create and apply policies for malware detection, endpoint isolation, and compliance.
Step 4: Monitor Threats
- Use the Threats dashboard to view detected threats, analyze activities, and track remediation actions.
Step 5: Perform Threat Hunting
- Utilize SentinelOne’s search and analysis tools to proactively hunt for potential threats.
Step 6: Generate Reports
- Access the Reports section to create detailed reports on endpoint security and compliance.