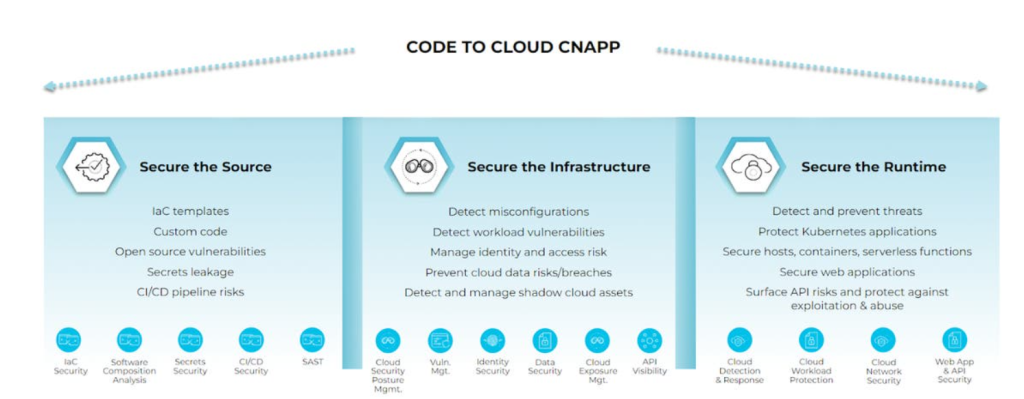
Palo Alto Prisma Cloud is a comprehensive cloud-native security platform designed to protect applications, workloads, and infrastructure across hybrid and multi-cloud environments. It offers advanced security capabilities, including threat detection, compliance management, runtime protection, and vulnerability management. Prisma Cloud provides centralized visibility and control, ensuring that organizations can confidently secure their cloud-native applications and infrastructure.
What is Palo Alto Prisma Cloud?
Palo Alto Prisma Cloud is a cloud-native security solution that delivers a unified approach to securing applications, data, and workloads across public and private cloud environments. It integrates seamlessly with popular cloud providers like AWS, Azure, and Google Cloud, offering protection for containers, Kubernetes, serverless functions, and virtual machines.
Key Characteristics of Prisma Cloud:
- Comprehensive Security: Covers all aspects of cloud security, including DevSecOps, runtime protection, and compliance.
- Centralized Management: Provides a unified platform to monitor and manage security across multi-cloud environments.
- Cloud-Native Integration: Natively integrates with cloud platforms and services for seamless deployment.
- Automated Compliance: Ensures continuous compliance with industry regulations and best practices.
Top 10 Use Cases of Palo Alto Prisma Cloud
- Cloud Security Posture Management (CSPM)
- Monitors and remediates misconfigurations across cloud environments to ensure compliance and reduce risks.
- Container Security
- Secures containerized applications and Kubernetes clusters by providing runtime protection and vulnerability scanning.
- Infrastructure as Code (IaC) Scanning
- Analyzes IaC templates (e.g., Terraform, CloudFormation) to identify misconfigurations before deployment.
- Runtime Protection
- Monitors running workloads and applications for suspicious behavior and protects them against threats.
- Vulnerability Management
- Scans images, containers, and virtual machines for vulnerabilities and provides actionable remediation steps.
- Serverless Security
- Protects serverless functions against misconfigurations, code vulnerabilities, and runtime threats.
- Threat Detection
- Uses machine learning and threat intelligence to identify malicious activities across cloud environments.
- Compliance Management
- Automates compliance reporting and ensures adherence to standards like GDPR, HIPAA, PCI DSS, and SOC 2.
- Identity and Access Management (IAM) Security
- Detects overly permissive IAM roles and ensures least privilege access across cloud accounts.
- Data Security and Visibility
- Monitors data flows and protects sensitive information stored in cloud services from exposure.
Features of Palo Alto Prisma Cloud
- Cloud Security Posture Management (CSPM) – Continuously monitors and remediates cloud misconfigurations.
- Cloud Workload Protection (CWP) – Protects workloads, containers, serverless functions, and VMs.
- Vulnerability Management – Identifies and addresses vulnerabilities in cloud environments and images.
- Compliance Automation – Provides pre-built and customizable compliance frameworks for regulatory standards.
- Threat Detection and Response – Leverages machine learning to detect and respond to advanced threats.
- Runtime Protection – Monitors workloads for anomalous behaviors and enforces runtime security policies.
- DevSecOps Integration – Integrates security into CI/CD pipelines, ensuring vulnerabilities are addressed during development.
- IAM Security – Audits and enforces least privilege access policies for cloud resources.
- Centralized Visibility – Offers dashboards and reports to provide a comprehensive view of the cloud security posture.
- Multi-Cloud Support – Works seamlessly with AWS, Azure, Google Cloud, and other cloud providers.
How Palo Alto Prisma Cloud Works and Architecture
1. Data Collection and Analysis
Prisma Cloud collects data from cloud accounts, workloads, containers, and serverless environments. This data is analyzed for security risks, compliance violations, and potential threats.
2. Threat Detection
The platform uses advanced analytics, machine learning, and threat intelligence to identify and prioritize threats.
3. Policy Enforcement
Prisma Cloud enforces security policies across cloud environments, workloads, and applications, ensuring continuous compliance and runtime protection.
4. Integration with DevOps Tools
The platform integrates with CI/CD pipelines, allowing security checks to be embedded into the development lifecycle.
5. Centralized Management
Administrators can monitor and manage security across multiple cloud environments from a unified console, with detailed dashboards and reports.
How to Install Palo Alto Prisma Cloud
Palo Alto Prisma Cloud (formerly RedLock) is a comprehensive cloud-native security platform designed to provide visibility, compliance, and threat detection for cloud infrastructure. It integrates with major cloud providers like AWS, Azure, and Google Cloud to ensure security across workloads, containers, and serverless functions.
While the Palo Alto Prisma Cloud platform itself is typically set up via a web interface, you can automate parts of the deployment and configuration process through scripts and APIs.
Steps to Install and Configure Palo Alto Prisma Cloud Programmatically
1. Sign Up for Prisma Cloud
First, sign up for Palo Alto Prisma Cloud at Prisma Cloud Website. You’ll need access to your Prisma Cloud API keys and management credentials for further automation.
2. System Requirements
Ensure that the system meets the minimum requirements for Prisma Cloud:
- Cloud Providers: Prisma Cloud works with major cloud environments such as AWS, Microsoft Azure, and Google Cloud.
- Supported Platforms: Typically, Prisma Cloud is integrated with Kubernetes, Docker, and other container orchestration platforms.
- API Access: Ensure API access is enabled for the cloud platforms you’re using (AWS, Azure, GCP).
3. Obtain Prisma Cloud Installer
Prisma Cloud itself is a cloud-native solution, so you typically don’t install it on a physical server. However, the components of Prisma Cloud that need to be deployed (such as the Prisma Cloud Defender) require installation.
- Download the required installation components from the Prisma Cloud Console (available once you log into your account).
- For Kubernetes environments, you’ll deploy Prisma Cloud Defender as a container.
4. Install Prisma Cloud Defender (Kubernetes Example)
In a Kubernetes environment, Prisma Cloud Defender is installed using Helm or kubectl.
Step 1: Download Prisma Cloud Defender Installer for Kubernetes
# Add the Prisma Cloud Helm repository
helm repo add paloaltonetworks https://charts.paloaltonetworks.com
# Update the Helm chart repository
helm repo update
Step 2: Install Prisma Cloud Defender with Helm
# Install Prisma Cloud Defender in Kubernetes using Helm
helm install defender paloaltonetworks/prisma-cloud-defender --set global.accessKey=<your-access-key> --set global.secretKey=<your-secret-key>
- Replace
<your-access-key>and<your-secret-key>with the appropriate keys from your Prisma Cloud account.
You can also configure other settings like global.region and global.clusterName based on your setup.
Step 3: Verify the Installation
To verify the installation, you can run:
# Check if Prisma Cloud Defender is installed successfully in Kubernetes
kubectl get pods -n prisma-cloud
This command will list the pods deployed by Prisma Cloud, including Prisma Cloud Defender.
5. Install Prisma Cloud Defender for AWS or Other Cloud Platforms
If you’re working with AWS, you will need to configure Prisma Cloud Defender for AWS manually by deploying it as an EC2 instance or using CloudFormation templates provided by Palo Alto Networks.
Step 1: Configure AWS IAM Permissions
Before deploying Prisma Cloud Defender for AWS, ensure that you have the necessary IAM roles and policies in place. Create an IAM policy with sufficient permissions, such as access to CloudTrail, S3, EC2, Lambda, and CloudWatch.
Step 2: Deploy Prisma Cloud Defender via CloudFormation
You can deploy Prisma Cloud Defender using the CloudFormation template provided by Palo Alto Networks. Follow these steps:
- Go to the Palo Alto Networks documentation and download the CloudFormation template for Prisma Cloud.
- Deploy the template via the AWS Management Console:
# Deploy Prisma Cloud Defender via AWS CloudFormation
aws cloudformation create-stack --stack-name prisma-cloud-defender --template-body file://prisma-cloud-defender-template.yaml
This will automatically deploy Prisma Cloud Defender to your AWS environment.
Step 3: Verify Installation in AWS
You can verify that the Prisma Cloud Defender is running in your AWS environment by checking the deployed EC2 instance and security monitoring configurations in the Prisma Cloud Console.
6. Automating Prisma Cloud Configuration with REST APIs
After installation, you can automate the configuration and management of Prisma Cloud using its REST API.
Here’s an example of how to interact with the Prisma Cloud REST API to list the available Defenders:
import requests
# Prisma Cloud API endpoint and credentials
base_url = "https://<prisma-cloud-console-url>/v1"
access_key = "your-access-key"
secret_key = "your-secret-key"
# Authenticate using the access keys
auth_data = {
"username": "your-username",
"password": "your-password"
}
auth_response = requests.post(f"{base_url}/auth/login", data=auth_data)
if auth_response.status_code == 200:
token = auth_response.json().get('token')
headers = {
"Authorization": f"Bearer {token}"
}
# Example: List Defenders
defenders_response = requests.get(f"{base_url}/defenders", headers=headers)
if defenders_response.status_code == 200:
defenders = defenders_response.json()
print("Defenders:", defenders)
else:
print(f"Failed to authenticate: {auth_response.status_code}")
This script authenticates to the Prisma Cloud API and retrieves a list of Defender instances.
7. Access Prisma Cloud Console
Once Prisma Cloud Defender is installed and configured, access the Prisma Cloud Console by navigating to https://<prisma-cloud-console-url>. Log in with the credentials you set during setup.
8. Post-Installation Tasks
After installation, some common post-installation tasks include:
- Setting up policies for monitoring and alerting.
- Configuring data sources such as S3 buckets, EC2 instances, or Kubernetes clusters for security analysis.
- Reviewing security alerts and responding to incidents.
You can configure all of this through the Prisma Cloud Console or by using the API.
Basic Tutorials of Palo Alto Prisma Cloud: Getting Started
Step 1: Access the Prisma Cloud Console
- Log in to the Prisma Cloud console using your admin credentials.
Step 2: Add Cloud Accounts
- Navigate to Settings > Cloud Accounts.
- Add AWS, Azure, or Google Cloud accounts to enable monitoring and protection.
Step 3: Deploy Defenders
- Go to Manage > Defenders and deploy lightweight agents to secure workloads and applications.
Step 4: Configure Compliance Policies
- Use the Compliance tab to select or customize frameworks like GDPR, HIPAA, or PCI DSS.
Step 5: Enable Threat Detection
- Activate advanced threat detection and configure alerts for high-priority incidents.
Step 6: Monitor and Respond
- Use the Dashboard and Alerts sections to monitor security events and respond to threats.