Amazon Web Services (AWS) Security Hub is a centralized security management service that provides a comprehensive view of your security posture across all your AWS accounts. It collects, aggregates, and prioritizes security findings from AWS services and third-party tools, helping organizations monitor compliance, detect threats, and respond to incidents efficiently. With AWS Security Hub, security teams can streamline their operations and maintain consistent security standards across their cloud environments.
What is AWS Security Hub?
AWS Security Hub is a cloud-native security service that consolidates security findings from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, and AWS Config, as well as third-party security tools. It uses built-in security standards and frameworks to assess your environment and provide actionable insights. AWS Security Hub enables continuous monitoring and helps organizations improve their security posture in real time.
Key Characteristics of AWS Security Hub:
- Centralized Security View: Provides a single dashboard to view and manage security findings across AWS accounts.
- Automated Compliance Checks: Evaluates your environment against security frameworks like CIS AWS Foundations Benchmark and PCI DSS.
- Integration Capabilities: Seamlessly integrates with AWS services and third-party security solutions.
- Customizable Insights: Allows customization of security rules and alerts to meet specific organizational requirements.
Top 10 Use Cases of AWS Security Hub
- Centralized Security Management
- Consolidates security findings from AWS services and third-party tools into a unified view.
- Threat Detection and Response
- Identifies and prioritizes security threats by integrating with services like Amazon GuardDuty and AWS WAF.
- Compliance Monitoring
- Continuously monitors and evaluates your environment against compliance standards like CIS, PCI DSS, and AWS Foundational Security Best Practices.
- Multi-Account Security Management
- Simplifies security management across multiple AWS accounts and regions.
- Cloud Resource Monitoring
- Detects misconfigurations and vulnerabilities in AWS resources, such as S3 buckets, EC2 instances, and IAM roles.
- Incident Investigation and Forensics
- Provides detailed security findings for incident analysis and root cause determination.
- Integration with SIEM Tools
- Integrates with SIEM solutions like Splunk and Datadog for enhanced security event analysis.
- Automation and Remediation
- Automates security tasks using AWS Lambda to remediate identified issues.
- Custom Security Rules
- Enables the creation of custom security rules tailored to organizational needs.
- Real-Time Alerts
- Generates real-time alerts and notifications for critical security findings.
Features of AWS Security Hub
- Centralized Dashboard – Provides a unified view of security findings across AWS accounts and regions.
- Automated Security Checks – Continuously evaluates your environment against best practices and compliance frameworks.
- Integration with AWS Services – Works seamlessly with GuardDuty, Inspector, AWS Config, and more.
- Third-Party Integration – Supports integration with leading security tools like Trend Micro, McAfee, and Palo Alto Networks.
- Custom Actions – Allows automated responses to security findings using AWS Lambda functions.
- Consolidated Findings – Aggregates findings from various sources to reduce noise and prioritize critical issues.
- Multi-Account Support – Simplifies security management for organizations with multiple AWS accounts.
- Compliance Frameworks – Includes pre-built frameworks such as CIS AWS Foundations Benchmark and PCI DSS.
- Detailed Reporting – Offers detailed insights and recommendations for security improvements.
- Scalable and Cost-Effective – Scales with your AWS environment and operates on a pay-as-you-go pricing model.
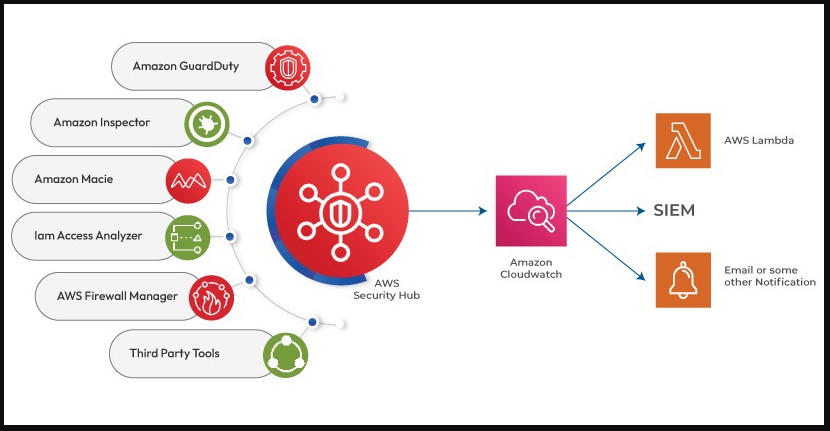
How AWS Security Hub Works and Architecture
1. Data Collection
- AWS Security Hub collects security findings from AWS services like GuardDuty, AWS Config, and Inspector, as well as third-party tools via APIs and integrations.
2. Findings Aggregation
- Findings are aggregated, normalized, and deduplicated to reduce noise and provide a clear view of security risks.
3. Compliance Evaluation
- The service automatically checks your resources against compliance frameworks and provides detailed results and recommendations.
4. Prioritization and Visualization
- Security Hub prioritizes findings based on severity and risk level, displaying them in a centralized dashboard.
5. Integration and Automation
- Integrates with AWS Lambda and other AWS services to automate responses and remediation for identified security issues.
How to Install AWS Security Hub
AWS Security Hub is a comprehensive security service that provides centralized visibility into the security state of your AWS environment. It helps aggregate, organize, and prioritize security findings from various AWS services (e.g., AWS GuardDuty, AWS Inspector, and AWS Macie) as well as from third-party security solutions.
To install and configure AWS Security Hub programmatically, you can use AWS CLI commands, AWS SDKs, or AWS CloudFormation templates. Below are the steps and code snippets to help automate the installation and configuration of AWS Security Hub using the AWS CLI and CloudFormation.
1. Prerequisites
Before starting, make sure you have the following:
- AWS CLI installed and configured with your credentials.
- IAM Permissions: Ensure you have the necessary IAM permissions to create and configure AWS Security Hub (e.g.,
securityhub:EnableSecurityHub,securityhub:DescribeHub, etc.).
2. Enable AWS Security Hub Using AWS CLI
To enable AWS Security Hub, you can use the AWS CLI. Here’s how you can enable it programmatically.
Step 1: Enable AWS Security Hub
Use the following AWS CLI command to enable AWS Security Hub in your AWS account:
aws securityhub enable-security-hub
This command enables AWS Security Hub in your current AWS region. You should see a confirmation output indicating that the service has been enabled.
Step 2: Enable Security Standards
You can enable various security standards such as AWS Foundational Security Best Practices, CIS AWS Foundations Benchmark, or others. For example, to enable the AWS Foundational Security Best Practices:
aws securityhub enable-security-standards --standards-arn arn:aws:securityhub:us-east-1::standards/aws-foundational-security-best-practices/v/1.0.0
This enables the AWS Foundational Security Best Practices standard in AWS Security Hub.
Step 3: Enable AWS Config Integration (Optional)
If you want to integrate AWS Config with Security Hub to collect configuration and compliance data:
aws securityhub enable-import-findings-from-securityhub --import-findings
3. Set Up AWS Security Hub Using AWS SDK
You can also use AWS SDKs (e.g., Python boto3) to automate the process of enabling and configuring AWS Security Hub.
Step 1: Install the AWS SDK (boto3 for Python)
If you’re using Python, install the boto3 library:
pip install boto3
Step 2: Enable AWS Security Hub using boto3
Here’s an example using Python and boto3 to enable AWS Security Hub:
import boto3
# Create a SecurityHub client
client = boto3.client('securityhub')
# Enable AWS Security Hub
response = client.enable_security_hub()
# Print the response
print(response)
This script uses the AWS SDK for Python to enable Security Hub in your AWS account.
Step 3: Enable Security Standards using boto3
Here’s how you can enable the AWS Foundational Security Best Practices standard programmatically:
# Enable AWS Foundational Security Best Practices
response = client.enable_security_standards(
StandardsArn='arn:aws:securityhub:us-east-1::standards/aws-foundational-security-best-practices/v/1.0.0'
)
print(response)
This script enables the AWS Foundational Security Best Practices standard for security assessments.
4. Set Up AWS Security Hub Using CloudFormation
You can also enable and configure AWS Security Hub via AWS CloudFormation. Below is an example CloudFormation template to enable Security Hub.
Step 1: CloudFormation Template to Enable Security Hub
AWSTemplateFormatVersion: '2010-09-09'
Resources:
EnableSecurityHub:
Type: 'AWS::SecurityHub::Hub'
Properties:
Tags:
Name: 'SecurityHubSetup'
This CloudFormation template enables Security Hub in the AWS environment.
Step 2: Deploy CloudFormation Template Using AWS CLI
Once you have your CloudFormation template (securityhub-setup.yaml), you can deploy it using the following command:
aws cloudformation create-stack --stack-name EnableSecurityHubStack --template-body file://securityhub-setup.yaml
This will create a CloudFormation stack that enables AWS Security Hub.
5. Integrate Findings from Other AWS Services
Once you have enabled Security Hub, you can start aggregating findings from other services like AWS GuardDuty, AWS Macie, and AWS Inspector.
Step 1: Enable GuardDuty Findings in Security Hub
If you have Amazon GuardDuty enabled, you can automatically send findings from GuardDuty to Security Hub:
aws securityhub enable-import-findings-from-source --source-type "GuardDuty"
Step 2: Enable Macie Findings in Security Hub
If you are using Amazon Macie for sensitive data discovery, you can send Macie findings to Security Hub:
aws securityhub enable-import-findings-from-source --source-type "Macie"
6. View Security Hub Findings
Once everything is set up, you can view the security findings using the AWS Management Console or by querying Security Hub using AWS CLI or boto3.
For example, to list findings using AWS CLI:
aws securityhub get-findings
Or using boto3:
# Retrieve findings from Security Hub
response = client.get_findings()
# Print findings
for finding in response['Findings']:
print(finding)
7. Enable Security Hub in Multiple Regions
If you want to enable AWS Security Hub across multiple regions, you need to manually enable it in each region or use automation scripts to deploy across your regions.
For example, with AWS CLI, you can set the --region flag for each region:
aws securityhub enable-security-hub --region us-west-2
aws securityhub enable-security-hub --region eu-west-1
Basic Tutorials of AWS Security Hub: Getting Started
Step 1: Enable Security Hub
- Go to the AWS Management Console, search for Security Hub, and enable the service.
Step 2: Add AWS Services
- Navigate to Settings in the Security Hub console.
- Enable integrations with services like GuardDuty, AWS Config, and Inspector.
Step 3: Configure Compliance Checks
- Select and enable security frameworks (e.g., CIS AWS Foundations Benchmark) for continuous compliance monitoring.
Step 4: View Security Findings
- Access the Findings tab to view aggregated security alerts and prioritize critical issues.
Step 5: Automate Actions
- Use AWS Lambda to create automated workflows for responding to specific findings.
Step 6: Generate Reports
- Use the Compliance tab to generate detailed compliance reports for your AWS environment.