Google Cloud Security Command Center (SCC) is a centralized security management platform designed to help organizations detect, protect, and respond to security threats across their Google Cloud Platform (GCP) resources. SCC provides real-time visibility into security vulnerabilities, threats, and misconfigurations in your cloud environment, enabling security teams to take proactive measures to protect critical assets and maintain compliance.
What is Google Cloud Security Command Center?
Google Cloud Security Command Center is a cloud-native security and risk management solution built specifically for GCP environments. It acts as a single dashboard where users can monitor their cloud resources, identify vulnerabilities, and detect potential threats. By aggregating security data from various Google Cloud services and third-party tools, SCC offers actionable insights to improve security posture and reduce risk.
Key Characteristics of SCC:
- Centralized Visibility: Provides a unified view of security data across all GCP resources.
- Real-Time Threat Detection: Identifies and alerts on active threats and vulnerabilities.
- Compliance Monitoring: Tracks security posture against regulatory and industry standards.
- Automated Responses: Integrates with Google Cloud workflows to automate incident responses.
Top 10 Use Cases of Google Cloud Security Command Center
- Threat Detection and Response
- Identifies and responds to threats such as malware, phishing, and unauthorized access in real time.
- Vulnerability Management
- Scans workloads and applications for known vulnerabilities and misconfigurations.
- Cloud Security Posture Management (CSPM)
- Monitors your cloud environment for security best practices and compliance requirements.
- Data Protection
- Detects and prevents data exposure in cloud storage services like Google Cloud Storage.
- Application Security
- Protects containerized and serverless applications by identifying vulnerabilities in Kubernetes and Cloud Functions.
- Compliance Management
- Helps organizations meet regulatory requirements like PCI DSS, GDPR, and HIPAA by automating security audits.
- User Behavior Monitoring
- Tracks user activity to detect anomalies and prevent insider threats.
- Risk Prioritization
- Provides a risk-based view of vulnerabilities, helping teams focus on the most critical issues.
- Integration with SIEM Tools
- Connects with third-party SIEM platforms for advanced threat analytics and reporting.
- Security Automation
- Automates repetitive tasks, such as alerting and incident response, using Google Cloud workflows and automation tools.
Features of Google Cloud Security Command Center
- Asset Inventory – Automatically discovers and lists all resources in your GCP environment.
- Threat Detection – Uses Google Cloud services like Event Threat Detection and Web Security Scanner to identify threats.
- Vulnerability Scanning – Identifies vulnerabilities in container images, virtual machines, and serverless environments.
- Compliance Management – Provides built-in compliance checks for standards like PCI DSS and CIS benchmarks.
- Real-Time Alerts – Generates alerts for high-severity security findings, allowing immediate action.
- Data Loss Prevention (DLP) – Monitors sensitive data and detects unauthorized exposure or access.
- Custom Security Policies – Allows creation of custom policies tailored to organizational needs.
- Integration with Google Cloud Tools – Seamlessly integrates with GCP services like Cloud Logging, BigQuery, and Cloud Monitoring.
- Access Insights – Tracks IAM policies and permissions to identify overly permissive access.
- Centralized Dashboard – Consolidates findings from multiple sources for streamlined management.
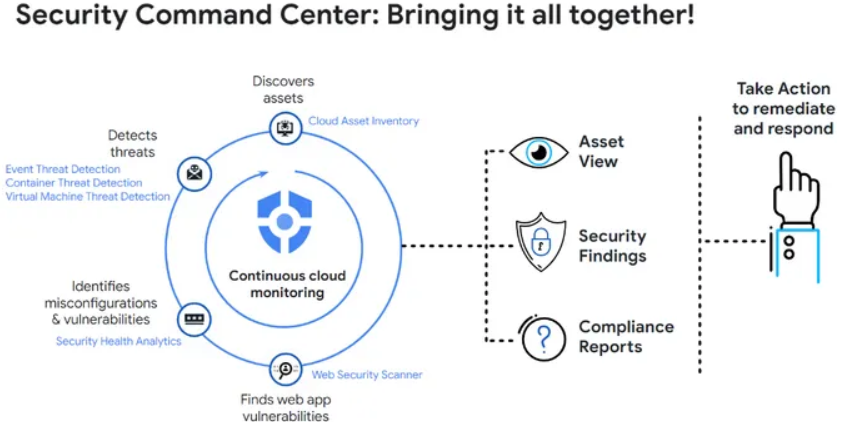
How Google Cloud Security Command Center Works and Architecture
1. Data Aggregation
SCC collects security data from Google Cloud services, third-party tools, and custom integrations. It consolidates this data into a single dashboard for analysis.
2. Threat and Vulnerability Analysis
SCC applies advanced analytics and machine learning models to identify risks, detect threats, and prioritize vulnerabilities.
3. Real-Time Alerts and Notifications
The platform generates real-time alerts for high-priority security findings, enabling teams to respond quickly.
4. Automation and Integration
SCC integrates with Google Cloud workflows and automation tools, such as Cloud Functions and Pub/Sub, to automate security responses and remediation.
5. Continuous Monitoring
The platform continuously monitors resources, ensuring that security policies are enforced and risks are addressed promptly.
How to Install Google Cloud Security Command Center
Google Cloud Security Command Center (SCC) is a centralized security and risk management platform that helps organizations assess, manage, and respond to security vulnerabilities and risks in their Google Cloud environment. Installing and configuring Google Cloud SCC programmatically can be done using Google Cloud CLI, Cloud APIs, or Terraform.
Here’s a step-by-step guide on how to install and configure Google Cloud SCC programmatically using the Google Cloud CLI and APIs.
1. Prerequisites
Before proceeding, ensure you meet the following prerequisites:
- Google Cloud Project: Ensure you have a Google Cloud project set up.
- Permissions: You must have sufficient permissions, such as Owner or Security Admin roles, to enable APIs and configure SCC.
- Google Cloud SDK: You should have the Google Cloud SDK installed and authenticated. If not, you can install it by following the instructions here.
2. Enable Google Cloud Security Command Center (SCC) API
The first step is to enable the Security Command Center API for your Google Cloud project. This can be done using the Google Cloud CLI.
Step 1: Install Google Cloud SDK (if not installed)
# Install Google Cloud SDK
curl https://sdk.cloud.google.com | bash
# Restart the shell to ensure that the Google Cloud SDK is available
exec -l $SHELL
Step 2: Authenticate with Google Cloud
Authenticate your Google Cloud account using:
gcloud auth login
Step 3: Set Your Project
Set the active project in which you want to enable the Security Command Center:
gcloud config set project YOUR_PROJECT_ID
Step 4: Enable the Security Command Center API
Run the following command to enable the Security Command Center API:
gcloud services enable securitycenter.googleapis.com
This command enables the Google Cloud Security Command Center service in your Google Cloud project.
3. Enable Security Command Center and Configure Sources
Once the API is enabled, the next step is to enable Security Command Center and configure its sources.
Step 1: Enable the Security Command Center in Your Project
To enable the Security Command Center in your project, use the following command:
gcloud beta securitycenter settings enable
This will enable the Security Command Center for your Google Cloud project.
Step 2: Configure Data Sources
Next, configure various data sources that the Security Command Center will monitor. For example, you can enable integrations with Cloud Asset Inventory, Cloud Security Scanner, and Security Health Analytics.
Enable Cloud Asset Inventory
gcloud services enable cloudasset.googleapis.com
Enable Security Health Analytics
gcloud services enable securityhealthanalytics.googleapis.com
Enable Google Cloud Security Scanner
gcloud services enable securityscanner.googleapis.com
These services will send relevant security information to the Security Command Center.
4. Access Google Cloud Security Command Center
After enabling Google Cloud SCC, you can access the Security Command Center Console via the Google Cloud Console:
gcloud console open
Alternatively, navigate to the Security Command Center from the Google Cloud Console at:
https://console.cloud.google.com/security-center
5. Automate Configuration with APIs
Google Cloud SCC can be managed programmatically using REST APIs. You can interact with the SCC API to retrieve security findings, configure security sources, and manage the security configuration of your Google Cloud environment.
Step 1: Get API Access
To interact with the Google Cloud SCC API, you need an OAuth2 token. Here’s how you can obtain a token using Google Cloud CLI:
gcloud auth application-default print-access-token
This command returns the access token needed to make API requests.
Step 2: Example: List Findings Using Google Cloud SCC API
Here’s an example of using curl to list findings from Security Command Center using the API:
curl -X GET \
"https://securitycenter.googleapis.com/v1p1beta1/projects/YOUR_PROJECT_ID/sources/-/findings" \
-H "Authorization: Bearer $(gcloud auth application-default print-access-token)"
This request retrieves security findings for your project. Replace YOUR_PROJECT_ID with your Google Cloud project ID.
Step 3: Example: Create a Custom Source Using API
You can create custom sources programmatically. Here’s an example using curl to create a source:
curl -X POST \
"https://securitycenter.googleapis.com/v1p1beta1/projects/YOUR_PROJECT_ID/sources" \
-H "Authorization: Bearer $(gcloud auth application-default print-access-token)" \
-H "Content-Type: application/json" \
-d '{
"sourceProperties": {
"displayName": "Custom Security Source",
"description": "A custom source for security findings."
}
}'
This creates a custom security source in your project.
6. Enable Integration with Google Cloud Services
You can integrate Security Command Center with various Google Cloud services such as Google Cloud Asset Inventory, Google Cloud Security Scanner, and Google Cloud Identity and Access Management (IAM). These integrations allow Security Command Center to ingest data from multiple sources and provide centralized security visibility.
Step 1: Enable IAM Integration
gcloud services enable iam.googleapis.com
Step 2: Enable Vulnerability Scanning Integration
gcloud services enable containeranalysis.googleapis.com
7. Monitoring and Responding to Findings
After setting up Security Command Center, you can monitor security findings using the Google Cloud Console, or you can use the API to retrieve findings and take actions. Use the API to query findings and integrate them into your security operations workflows.
8. Automate with Terraform
If you prefer infrastructure-as-code, you can use Terraform to automate the deployment and configuration of Google Cloud SCC. Below is an example of a Terraform configuration to enable Security Command Center.
provider "google" {
project = "YOUR_PROJECT_ID"
}
resource "google_project_service" "securitycenter" {
project = "YOUR_PROJECT_ID"
service = "securitycenter.googleapis.com"
}
resource "google_security_center_settings" "default" {
security_center_settings {
enable_security_center = true
}
}
Run the following Terraform commands to deploy:
terraform init
terraform apply
This will automatically enable Google Cloud SCC in your project using Terraform.
Basic Tutorials of Google Cloud Security Command Center: Getting Started
Step 1: Access the SCC Dashboard
- Log in to the Google Cloud Console and navigate to Security Command Center.
Step 2: Review Asset Inventory
- Use the Assets tab to view an inventory of your GCP resources and identify any security risks.
Step 3: Enable Threat Detection Services
- Go to the Settings tab in SCC.
- Activate services like Event Threat Detection and Security Health Analytics.
Step 4: Monitor Security Findings
- Check the Findings tab to view and prioritize security issues across your environment.
Step 5: Configure Alerts
- Set up real-time alerts for critical findings to notify your security team of potential threats.
Step 6: Generate Compliance Reports
- Use the Compliance tab to monitor adherence to industry standards and generate reports for audits.