Introduction to Continuous Security Testing
In today’s world, where cybercrime is at an all-time high, it has become crucial for businesses to ensure they protect their applications and infrastructure from potential vulnerabilities. One way to achieve this objective is through continuous security testing.
What is Continuous Security Testing?
Continuous Security Testing (CST) is a process of testing applications and infrastructure for security vulnerabilities on an ongoing basis. It involves the use of automated tools, techniques, and processes to identify vulnerabilities, provide feedback, and remediate issues. CST helps ensure that security vulnerabilities are detected and addressed before they can be exploited by hackers.
Why is Continuous Security Testing Important?
Continuous Security Testing is essential because it helps businesses identify and remedy security vulnerabilities before they can be exploited by attackers. By regularly testing applications and infrastructure for vulnerabilities, businesses can prevent data breaches, loss of customer trust, and damage to their reputation. Additionally, continuous security testing helps businesses stay compliant with regulatory requirements such as GDPR, HIPAA, and PCI DSS.
Benefits of Using Continuous Security Testing Tools
Improved Security Posture
Continuous Security Testing tools help businesses improve their security posture by identifying vulnerabilities in their applications and infrastructure that may be missed by manual testing. The tools provide a comprehensive view of the security landscape and offer in-depth analysis of vulnerabilities, enabling businesses to prioritize and remediate issues quickly.
Early Detection of Security Vulnerabilities
Continuous Security Testing tools detect security vulnerabilities early in the development process, reducing the likelihood of vulnerabilities being introduced into production code. Early detection of vulnerabilities leads to quicker remediation, reducing the overall cost of fixing vulnerabilities.
Cost Savings
Continuous Security Testing tools can help businesses save money in the long run by detecting vulnerabilities early in the development process, before they can be exploited. Detecting vulnerabilities early leads to quicker remediation, reducing the overall cost of fixing vulnerabilities. Additionally, continuous security testing can help businesses avoid the high cost of data breaches, loss of customer trust, and damage to their reputation.
Types of Continuous Security Testing Tools
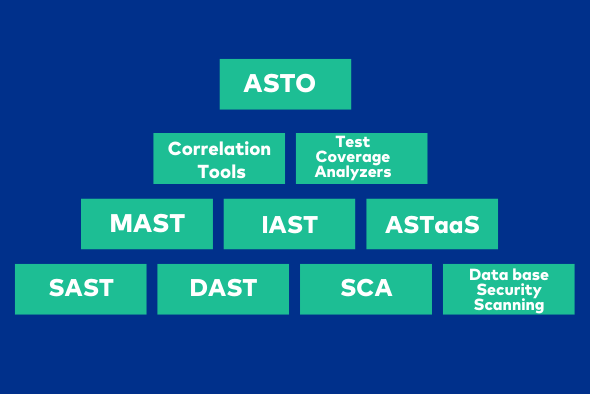
Static Application Security Testing (SAST)
SAST tools analyze the source code of an application for security vulnerabilities. SAST tools are used early in the development cycle, providing developers with an immediate view of potential vulnerabilities.
Dynamic Application Security Testing (DAST)
DAST tools are used to identify vulnerabilities in web applications by simulating an attack on the application. DAST tools detect vulnerabilities that may not be detected by SAST tools and provide a comprehensive view of the application’s security posture.
Interactive Application Security Testing (IAST)
IAST tools combine features of SAST and DAST tools to analyze the application’s behavior while it is running. IAST tools provide real-time feedback on potential vulnerabilities and are suited for applications that require a high level of security.
Runtime Application Self-Protection (RASP)
RASP tools are used to protect applications by detecting and blocking attacks from potential hackers. RASP tools detect potential attacks by analyzing the application’s behavior and provide immediate feedback to prevent attacks.
Container Security
Container security tools are used to identify vulnerabilities in containerized applications. Container security tools help businesses secure their applications in a containerized environment.
Cloud Security
Cloud security tools are used to identify vulnerabilities in cloud-based infrastructure. Cloud security tools provide business with real-time feedback on potential vulnerabilities, helping to secure their infrastructure.
Key Features to Look for in a Continuous Security Testing Tool
Automation Capabilities
Continuous Security Testing tools should have automation capabilities to reduce the time required to identify and remediate vulnerabilities.
Accuracy and Precision of Results
Continuous Security Testing tools should provide accurate and precise results to reduce false positives and false negatives, ensuring vulnerabilities are correctly identified and remediated.
Integration with DevOps Tools
Continuous Security Testing tools should integrate with DevOps tools to ensure vulnerabilities are detected early in the development process, reducing the overall cost of remediation.
Scalability and Flexibility
Continuous Security Testing tools should be scalable and flexible, allowing businesses to test applications and infrastructure of any size and complexity.
Best Practices for Implementing Continuous Security Testing
Continuous security testing is becoming an essential part of the software development lifecycle (SDLC) as it allows teams to identify and eliminate vulnerabilities early on. To ensure the success of your continuous security testing program, it’s important to implement some best practices:
1. Integrate Security Testing Early in the SDLC
Integrating security testing early in the SDLC helps identify vulnerabilities at the beginning of the development process, reducing the risk of security flaws making it into production. It’s crucial to involve security teams in the early stages of the SDLC to ensure security testing is built-in from the start.
2. Set Realistic Goals
When implementing continuous security testing, it’s essential to set realistic goals for the program. Start by prioritizing the most critical areas to test and build upon that. Be sure to communicate the goals and expectations to all stakeholders involved in the process.
3. Establish Clear Communication Channels
Effective communication is essential to the success of a continuous security testing program. Establish clear channels of communication between security and development teams to ensure that vulnerabilities are addressed promptly. It’s also important to share insights and findings with all relevant stakeholders.
4. Provide Regular Training to Security and Development Teams
Continuous training for the security and development teams is crucial to keep up with the constantly evolving threat landscape. Continuous training will ensure that all teams are up-to-date with best practices and new security tools.
Challenges Faced During Continuous Security Testing
Continuous security testing also comes with its set of challenges. Here are some of the most common challenges faced during the process:
1. Technical Challenges
Technical challenges include choosing the right set of security testing tools, managing and prioritizing the vulnerabilities and finding false positives. It requires an experienced team to address these technical challenges.
2. Cultural Challenges
Continuous security testing may require cultural change, especially if the development and security teams have not worked closely together in the past. It requires a culture of collaboration and trust.
3. Organizational Challenges
Organizational challenges may include obtaining management buy-in, securing budget and resources, and aligning priorities across teams.
Future of Continuous Security Testing Tools
1. Emerging Trends
Continuous security testing is rapidly evolving, and there are many emerging trends in this area, including AI and machine learning-based testing, security testing as a service, and the integration of security testing tools with DevOps.
2. New Technologies
New technologies are being developed to help address the challenges posed by continuous security testing. For example, container security tools are being developed to secure containers during the build and runtime stages.
Conclusion: Why Continuous Security Testing is Critical for Your Organization
Continuous security testing is no longer an optional add-on to software development but is becoming an essential part of the SDLC. Failure to address vulnerabilities early in the process can lead to costly security breaches and reputational damage. Implementing best practices, addressing challenges, and leveraging emerging trends and new technologies will enable organizations to stay ahead in this rapidly evolving field.Continuous security testing tools play a critical role in ensuring that software applications are secure and that organizations are able to protect themselves from potential cyber attacks. By choosing the right tools, implementing best practices, and staying up-to-date with emerging trends, organizations can take proactive steps to keep their systems safe and secure. With the constant evolution of technology and increasing sophistication of cyber threats, continuous security testing is no longer a luxury, but rather a necessity for any organization that wants to remain competitive and safeguard its operations.
FAQ
What is continuous security testing?
Continuous security testing is an approach to security that involves ongoing scanning of code and infrastructure for vulnerabilities and weaknesses. This is done on a regular basis, rather than as a one-time security audit.
What are the benefits of using continuous security testing tools?
The benefits of using continuous security testing tools include improved security posture, early detection of security vulnerabilities, and cost savings. By scanning for vulnerabilities on an ongoing basis, organizations are able to detect and remediate issues before they become major problems.
What are the types of continuous security testing tools?
The types of continuous security testing tools include static application security testing (SAST), dynamic application security testing (DAST), interactive application security testing (IAST), runtime application self-protection (RASP), container security, and cloud security.
What are the challenges faced during continuous security testing?
The challenges faced during continuous security testing include technical challenges, cultural challenges, and organizational challenges. Technical challenges can include false positives and negatives, while cultural challenges can include a lack of buy-in from development teams. Organizational challenges can include a lack of budget or resources for security testing.