CrowdStrike Falcon is a leading cloud-native cybersecurity platform designed to protect endpoints, detect threats, and respond to attacks in real-time. Leveraging artificial intelligence (AI) and threat intelligence, it provides next-generation antivirus (NGAV), endpoint detection and response (EDR), and proactive threat-hunting capabilities. With its lightweight agent and centralized management, CrowdStrike Falcon empowers organizations to secure their endpoints across on-premises, cloud, and hybrid environments.
What is CrowdStrike Falcon?
CrowdStrike Falcon is a robust endpoint protection solution that uses AI-powered analytics, behavioral analysis, and threat intelligence to detect and mitigate cyber threats. Its platform is designed to handle a wide range of cybersecurity needs, including malware protection, threat hunting, and incident response. As a fully cloud-based solution, Falcon offers seamless scalability, rapid deployment, and low performance impact on devices.
Key Characteristics of CrowdStrike Falcon:
- Cloud-Native Platform: Eliminates the need for on-premises hardware or infrastructure.
- AI-Driven Threat Detection: Uses machine learning to analyze behaviors and detect malicious activities.
- Lightweight Agent: Operates with minimal performance impact on endpoints.
- Integrated Threat Intelligence: Combines real-time data with global threat intelligence for accurate detection.
Top 10 Use Cases of CrowdStrike Falcon
- Next-Generation Antivirus (NGAV)
- Protects endpoints from malware, ransomware, and fileless attacks using signature-less detection.
- Endpoint Detection and Response (EDR)
- Provides real-time monitoring and forensic capabilities for advanced threat detection and investigation.
- Ransomware Protection
- Prevents ransomware attacks by detecting and blocking suspicious activities before encryption occurs.
- Threat Hunting
- Enables proactive threat hunting with Falcon OverWatch, identifying hidden threats that evade automated detection.
- Incident Response
- Provides in-depth forensic data and automated containment capabilities for rapid incident resolution.
- Fileless Threat Detection
- Detects and mitigates memory-based and script-based attacks.
- Zero-Day Threat Protection
- Identifies and blocks zero-day vulnerabilities through behavioral analysis and machine learning.
- Cloud Workload Protection
- Secures cloud-hosted workloads, containers, and virtual machines against cyber threats.
- Policy Management
- Enforces security policies across endpoints to reduce attack surfaces and ensure compliance.
- Threat Intelligence and Reporting
- Offers actionable threat intelligence and detailed reporting for security teams and stakeholders.
Features of CrowdStrike Falcon
- Next-Generation Antivirus (NGAV) – Provides signature-less protection against known and unknown threats.
- Endpoint Detection and Response (EDR) – Delivers real-time monitoring and threat investigation capabilities.
- Threat Hunting – Falcon OverWatch offers 24/7 human-driven threat hunting.
- Ransomware Protection – Blocks ransomware activities through behavioral analysis.
- Lightweight Agent – Requires minimal system resources and supports Windows, macOS, and Linux.
- Cloud-Native Architecture – Eliminates the need for on-premises hardware, offering scalability and flexibility.
- Threat Intelligence Integration – Leverages global threat intelligence for better detection and response.
- Automated Remediation – Isolates compromised systems and remediates threats with minimal manual intervention.
- Detailed Dashboards and Reporting – Provides insights into endpoint security and threat trends.
- Integration Ecosystem – Integrates seamlessly with SIEMs, SOAR platforms, and other security tools.
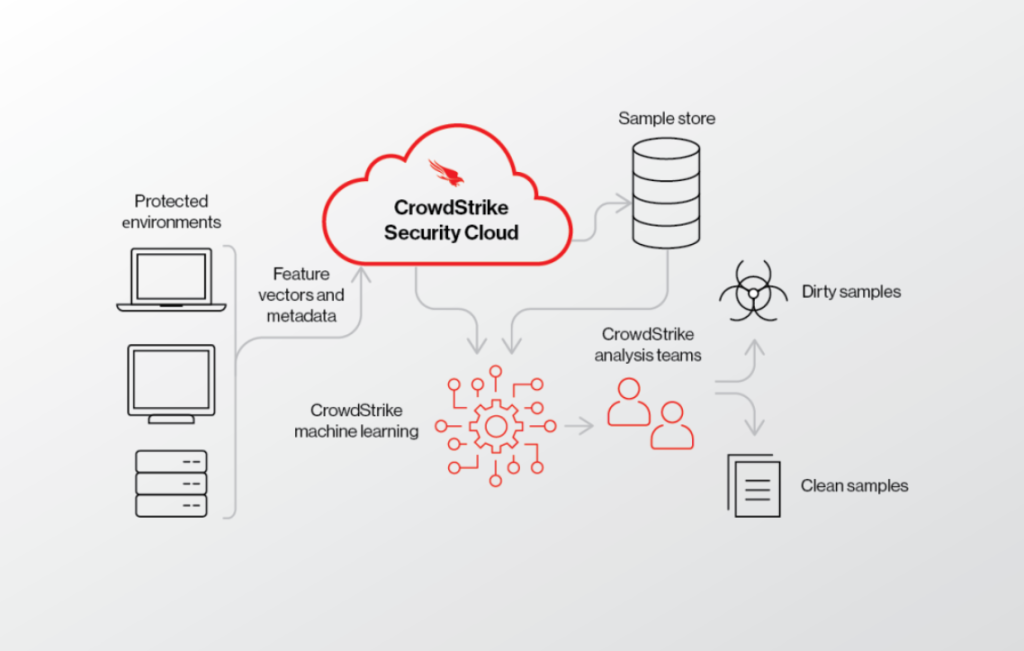
How CrowdStrike Falcon Works and Architecture
1. Lightweight Agent
CrowdStrike Falcon deploys a lightweight agent on endpoints to monitor activities, detect threats, and enforce policies. The agent consumes minimal resources and operates silently.
2. Cloud-Native Threat Detection
All data collected by the agent is sent to CrowdStrike’s cloud-based platform, where advanced analytics and machine learning models detect threats in real time.
3. Continuous Monitoring
The Falcon platform continuously monitors endpoint behaviors to identify anomalies, block malicious activities, and gather forensic data.
4. Threat Intelligence Integration
The platform integrates with CrowdStrike’s threat intelligence feeds to enhance detection accuracy and provide context for investigations.
5. Automated and Proactive Response
Falcon provides automated remediation capabilities, including endpoint isolation, threat removal, and policy enforcement, to contain and mitigate threats quickly.
How to Install CrowdStrike Falcon
CrowdStrike Falcon is a next-generation endpoint protection solution that provides threat detection, prevention, and response capabilities. The installation process involves installing the Falcon Sensor on endpoints, which communicates with the CrowdStrike cloud platform for real-time threat analysis and incident response.
Here’s how you can install CrowdStrike Falcon programmatically using command-line tools or scripts for Windows and Linux systems.
1. Obtain the Falcon Sensor Installer
- First, you need to log in to the CrowdStrike Falcon Console and download the appropriate Falcon Sensor installer for your platform (Windows or Linux).
- The installer is usually available as a
.pkg,.rpm,.deb, or.exefile depending on the target operating system.
2. Install CrowdStrike Falcon on Windows (Command Line)
The Falcon Sensor for Windows can be installed silently using the command line. Below is a step-by-step guide.
Step 1: Download the Falcon Sensor for Windows
- Download the Windows installer (typically
falcon-sensor-installer.exe) from the CrowdStrike Falcon Console.
Step 2: Install the Sensor Silently
You can perform a silent installation using the following command:
Start-Process -FilePath "C:\path\to\falcon-sensor-installer.exe" -ArgumentList "/quiet /install" -Wait
This will install CrowdStrike Falcon Sensor without prompting the user for input. The /quiet flag ensures the installation is silent, and /install starts the installation.
Step 3: Confirm Installation
After installation, you can confirm if the sensor is running by checking the services:
Get-Service -Name "CrowdStrike Falcon Sensor"
This should show the status of the Falcon Sensor service.
3. Install CrowdStrike Falcon on Linux (Command Line)
The installation process for Linux involves downloading the appropriate .rpm or .deb package and using the package manager to install it.
Step 1: Download the Falcon Sensor for Linux
- Download the Linux installer from the CrowdStrike Falcon Console. The installer will be available as a
.rpmfor RedHat/CentOS-based systems or.debfor Debian/Ubuntu-based systems.
Step 2: Install the Sensor (RPM-based systems)
For RPM-based systems (CentOS, RHEL, Fedora), run:
sudo rpm -ivh falcon-sensor.rpm
Step 2: Install the Sensor (DEB-based systems)
For DEB-based systems (Ubuntu, Debian), run:
sudo dpkg -i falcon-sensor.deb
Step 3: Confirm Installation
After installation, you can verify that the Falcon Sensor is running with the following command:
sudo systemctl status falcon-sensor
This should show the status of the Falcon Sensor service.
4. Automating Falcon Sensor Deployment on Multiple Machines (Windows Example)
If you need to deploy the CrowdStrike Falcon Sensor across multiple machines, you can use PowerShell or batch scripts to automate the installation.
PowerShell Script for Remote Deployment on Windows:
Here’s an example of a PowerShell script to deploy the Falcon Sensor to multiple remote computers:
# List of computers to install the sensor
$computers = Get-Content -Path "C:\computers.txt"
foreach ($computer in $computers) {
Invoke-Command -ComputerName $computer -ScriptBlock {
Start-Process -FilePath "C:\path\to\falcon-sensor-installer.exe" -ArgumentList "/quiet /install" -Wait
}
}
- This script reads a list of machine names from
computers.txtand installs the Falcon Sensor on each machine remotely using PowerShell’sInvoke-Command.
5. Automating with CrowdStrike API (Optional)
If you need to automate further aspects of the CrowdStrike Falcon installation or management, CrowdStrike provides a REST API that allows you to interact programmatically with your endpoint protection platform.
For example, you could use the API to retrieve installation details or manage policies for deployed sensors.
import requests
# Example of interacting with CrowdStrike API
api_url = "https://api.crowdstrike.com"
api_token = "your_api_token_here"
headers = {
"Authorization": f"Bearer {api_token}",
"Content-Type": "application/json"
}
# Example API call to get a list of endpoints
response = requests.get(f"{api_url}/devices/entities/devices/v1", headers=headers)
if response.status_code == 200:
devices = response.json()
print("Devices:", devices)
else:
print("Error:", response.status_code)
This example uses the CrowdStrike Falcon API to fetch a list of endpoint devices that are currently registered with the CrowdStrike platform.
6. Monitor and Manage with CrowdStrike Console
Once installed, you can monitor the CrowdStrike Falcon Sensor through the CrowdStrike Falcon Console. The console provides a central dashboard to:
- View sensor status.
- Manage security policies.
- Perform incident response actions.
Basic Tutorials of CrowdStrike Falcon: Getting Started
Step 1: Log in to the Falcon Console
- Use your CrowdStrike credentials to access the management console and explore its features.
Step 2: Deploy and Verify Agents
- Deploy Falcon agents on endpoints.
- Verify the installation status and connectivity in the Host Management section.
Step 3: Configure Security Policies
- Navigate to the Policy Management section.
- Create and apply policies for malware protection, device control, and application management.
Step 4: Monitor Endpoint Activity
- Use the Dashboard to monitor endpoint activities, security alerts, and threat intelligence updates.
Step 5: Conduct Threat Hunting
- Use the Falcon OverWatch interface to proactively identify and investigate potential threats.
Step 6: Generate Reports
- Access the Reports section to create detailed security reports for analysis and compliance.