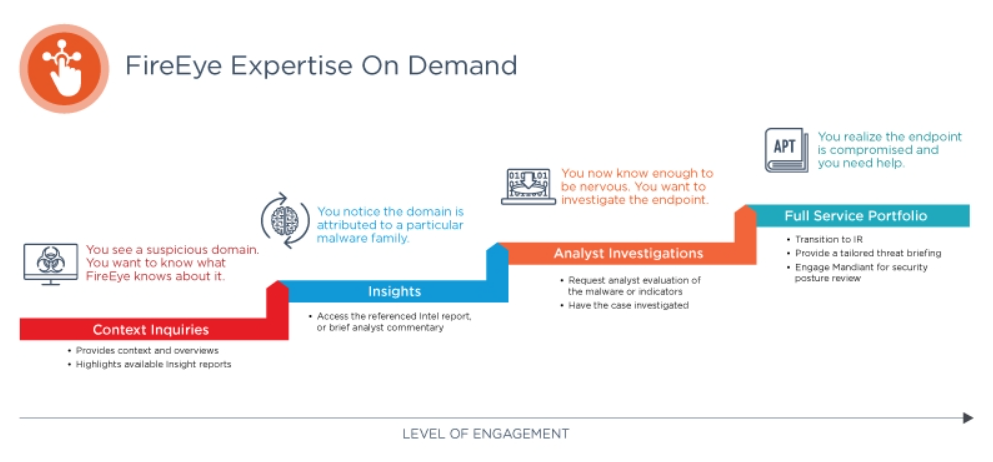
FireEye Mandiant is a leading provider of cybersecurity services and threat intelligence, specializing in incident response, threat hunting, and advanced security solutions. Mandiant helps organizations detect, respond to, and recover from sophisticated cyberattacks by offering expert guidance, real-time threat intelligence, and comprehensive analysis of cyber incidents. Its services include security assessments, managed detection and response (MDR), and forensic investigations, often focused on identifying advanced persistent threats (APTs) and nation-state actors.
Use cases for FireEye Mandiant span various industries, including incident response, where it assists organizations in managing and mitigating cyberattacks; threat intelligence, where it provides actionable insights on emerging threats; and security monitoring, where it helps businesses enhance their defenses with proactive threat detection and response strategies. Mandiant is particularly valuable in highly regulated industries such as finance, government, and healthcare, where it aids in compliance and protects sensitive data.
What is FireEye Mandiant?
FireEye Mandiant is a cybersecurity platform that combines advanced threat intelligence, incident response services, and security automation to detect, analyze, and mitigate cyber threats. Its services and solutions are built to address modern cyber challenges by offering in-depth investigations, threat analysis, and proactive strategies for risk management.
Key Characteristics of FireEye Mandiant:
- Incident Response Expertise: Trusted by organizations worldwide to handle critical incidents and mitigate attacks.
- Threat Intelligence: Offers actionable insights into emerging threats and adversaries.
- Proactive Security Solutions: Provides tailored assessments and strategies to strengthen security defenses.
- Integration with Security Tools: Works seamlessly with SIEMs, endpoint protection systems, and other security platforms.
Top 10 Use Cases of FireEye Mandiant
- Incident Response and Forensics
- Rapidly detects, contains, and mitigates active cyberattacks while providing a comprehensive forensic investigation.
- Threat Hunting
- Proactively identifies hidden threats in an organization’s environment before they cause damage.
- Cybersecurity Assessments
- Evaluates an organization’s security posture and provides recommendations for improvement.
- Advanced Persistent Threat (APT) Detection
- Identifies and mitigates sophisticated, targeted attacks by advanced adversaries.
- Ransomware Defense
- Assists in detecting and responding to ransomware attacks, including post-incident recovery strategies.
- Threat Intelligence Integration
- Enhances security operations with up-to-date intelligence on malware, vulnerabilities, and threat actors.
- Compromise Assessments
- Evaluates whether an organization’s environment has been breached or compromised.
- Security Operations Center (SOC) Optimization
- Improves the efficiency and effectiveness of SOCs through tools, processes, and training.
- Cloud Security
- Protects cloud environments from emerging threats and ensures compliance with best practices.
- Compliance and Regulatory Support
- Helps organizations meet industry regulations and standards such as GDPR, HIPAA, and PCI-DSS.
Features of FireEye Mandiant
- Incident Response Services – Offers on-demand and retainer-based incident response to handle active cyber threats.
- Threat Intelligence – Provides actionable intelligence about emerging threats and adversaries.
- Security Validation – Validates the effectiveness of security tools and processes with continuous testing.
- Threat Detection and Analytics – Uses advanced machine learning and analytics to detect threats in real time.
- Proactive Threat Hunting – Identifies and neutralizes hidden threats within an organization’s environment.
- Managed Defense – Delivers continuous monitoring and response with expert analysts.
- Advanced Forensics – Provides forensic analysis of compromised systems to determine root causes and attack vectors.
- Integration Capabilities – Works with SIEMs, EDR tools, and third-party security solutions.
- Ransomware Protection – Detects and mitigates ransomware attacks with detailed recovery plans.
- Security Training and Awareness – Offers tailored training programs for security teams.
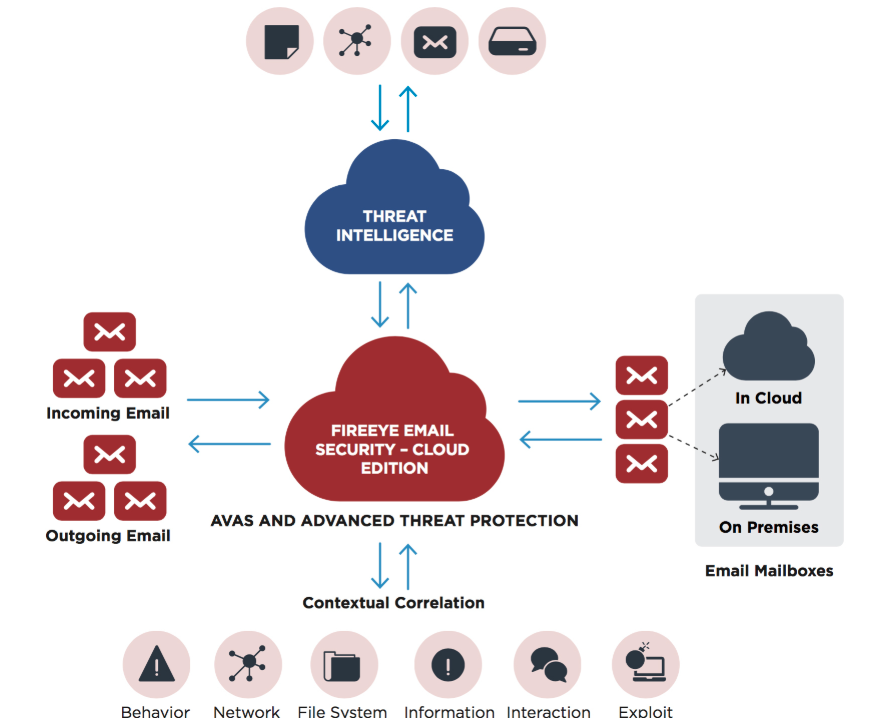
How FireEye Mandiant Works and Architecture
1. Integration with Security Tools
- FireEye Mandiant integrates with existing security solutions like SIEMs, endpoint protection platforms, and cloud security tools to gather and analyze data.
2. Incident Management Workflow
- Detection: Identifies threats using threat intelligence, machine learning, and expert analysis.
- Containment: Isolates affected systems to prevent further spread of the attack.
- Eradication: Removes malware, compromised accounts, and other threats from the environment.
- Recovery: Restores systems and implements measures to prevent future attacks.
3. Threat Intelligence Delivery
- Provides insights on current threat actors, malware families, and vulnerabilities via feeds and reports.
4. Proactive Services
- Includes threat hunting, compromise assessments, and security validation to strengthen defenses before incidents occur.
5. Advanced Forensic Capabilities
- Conducts deep investigations into incidents to identify root causes, attack vectors, and adversary techniques.
How to Install FireEye Mandiant
FireEye Mandiant is a suite of security products and services, rather than a software that you would install in the traditional sense via code. Mandiant primarily provides cybersecurity services such as incident response, threat intelligence, and managed detection and response (MDR), and these are typically delivered by Mandiant professionals rather than installed directly on an organization’s infrastructure.
However, FireEye products, including Mandiant services, may have software or appliances that integrate with your infrastructure for threat detection, incident response, and security monitoring. To automate some of Mandiant’s offerings or integrate them into your environment programmatically, you would typically use their APIs or configure their integrations with existing security tools.
Here’s an overview of the steps you might take to integrate FireEye Mandiant’s services and data into your infrastructure:
1. Engage with FireEye Mandiant Services
- Subscription/Services: Contact FireEye Mandiant for access to their products or services. Many of their services, such as incident response and threat intelligence, are provided as part of a subscription or engagement. They will typically provide cloud-based tools or security appliances to deploy.
- You can visit FireEye Mandiant’s official website for details about their products and services.
2. Set Up and Integrate Mandiant with Your Security Infrastructure
FireEye Mandiant integrates with various security solutions like SIEM systems (Splunk, ArcSight), firewalls, endpoint detection, and other cybersecurity tools. To automate or programmatically interact with Mandiant’s data and incident response, you would typically use their APIs.
3. Use FireEye Mandiant APIs for Integration
If you want to automate the integration of Mandiant’s services (such as threat intelligence feeds or incident reports) with your internal systems, you will interact with their REST APIs. Below is a general approach to interacting with APIs to pull data from Mandiant (assuming API access is provided).
Example: Using Mandiant’s Threat Intelligence API (hypothetical example):
import requests
# Replace with actual API endpoint for Mandiant services
api_url = "https://api.mandiant.com/v1/threat-intelligence"
api_key = "your_api_key_here" # Use your actual API key for authentication
# Define the headers for the API request
headers = {
"Authorization": f"Bearer {api_key}",
"Content-Type": "application/json"
}
# Fetching threat intelligence data
response = requests.get(api_url, headers=headers)
if response.status_code == 200:
threat_data = response.json()
print("Threat Data:", threat_data)
else:
print("Error fetching data:", response.status_code, response.text)
This script demonstrates how you might access threat intelligence data from Mandiant using their API. Replace the api_url and api_key with the actual details provided by FireEye Mandiant.
4. Integrate Mandiant with SIEMs and Other Security Tools
Mandiant offers integration with popular SIEM tools like Splunk and ArcSight. These integrations can be automated and configured to ingest data from Mandiant for real-time monitoring and automated responses to security incidents.
- Splunk Integration: If you’re using Splunk, you can integrate FireEye’s data feeds (such as alert data, threat intelligence) into your Splunk instance for correlation, visualization, and automated alerting.
- Endpoint Security: If Mandiant has specific endpoint protection tools, they may come with APIs for integration into your IT environment for data collection, analysis, and automated responses.
5. Use Mandiant’s Managed Detection and Response (MDR)
While FireEye Mandiant does not offer a simple “code-based” installation process like typical software, it provides services and integrations that help organizations improve their cybersecurity posture. To integrate Mandiant’s tools into your environment, you will typically use APIs to automate data exchange and integration with security tools like SIEMs. The installation of Mandiant itself usually involves configuring appliances, deploying threat intelligence tools, and engaging with their team for managed services. You can leverage APIs for real-time integration with your existing infrastructure, monitor threat intelligence, and automate responses accordingly.
Basic Tutorials of FireEye Mandiant: Getting Started
Step 1: Set Up Threat Intelligence Feeds
- Access your SIEM or endpoint detection tool.
- Configure it to receive Mandiant threat intelligence feeds.
Step 2: Incident Response Workflow
- In the event of a breach, open an incident in the Mandiant platform.
- Follow automated or guided workflows for detection, containment, and eradication.
Step 3: Proactive Threat Hunting
- Use the Mandiant platform to analyze logs and telemetry data.
- Identify and neutralize suspicious activity using predefined hunting playbooks.
Step 4: Validate Security Posture
- Deploy Mandiant Security Validation tools to test the effectiveness of your security controls.
- Review reports and implement recommended improvements.
Step 5: Generate Reports
- Use the reporting feature to generate detailed incident reports.
- Share these reports with stakeholders for compliance and auditing purposes.