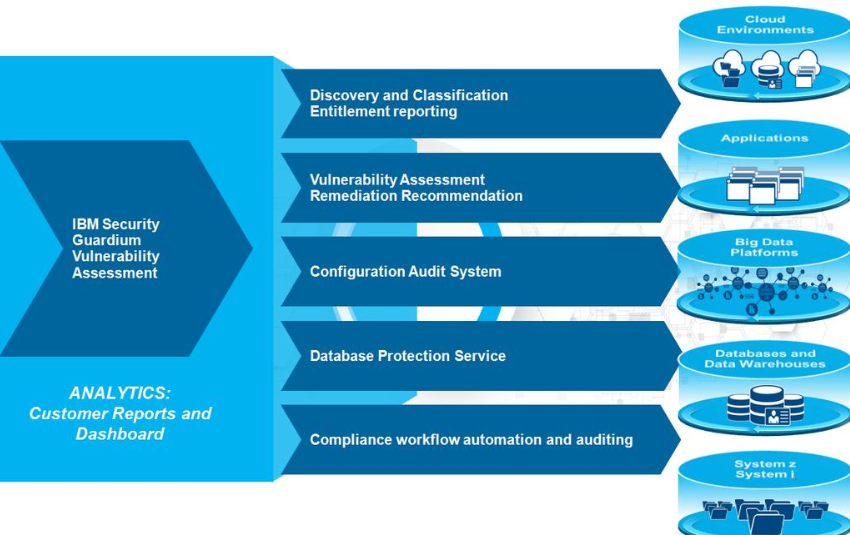
IBM Guardium is a data security and protection platform designed to safeguard sensitive data across multiple environments, including databases, big data platforms, cloud environments, and on-premises systems. It provides real-time monitoring, data activity auditing, vulnerability assessment, and advanced threat detection to ensure the integrity and confidentiality of your data. IBM Guardium is widely used by organizations to protect critical data, comply with regulatory requirements, and mitigate risks associated with data breaches.
What is IBM Guardium?
IBM Guardium is a comprehensive data security solution that helps organizations monitor, protect, and audit their sensitive data assets. It offers automated tools for discovering data vulnerabilities, enforcing security policies, and providing detailed audit reports for compliance. Guardium is built to work across a wide range of environments, ensuring consistent security for modern, hybrid, and multi-cloud infrastructures.
Key Characteristics of IBM Guardium:
- Real-Time Monitoring: Tracks and analyzes database activity in real time.
- Automated Compliance: Simplifies compliance reporting for regulations like GDPR, HIPAA, and PCI DSS.
- Data Discovery: Automatically identifies sensitive data across structured and unstructured data sources.
- Threat Detection: Uses advanced analytics to detect suspicious activities and potential data breaches.
Top 10 Use Cases of IBM Guardium
- Data Activity Monitoring
- Continuously monitors data access and usage to detect unauthorized or suspicious activities.
- Regulatory Compliance
- Automates compliance auditing and reporting for GDPR, HIPAA, PCI DSS, and more.
- Vulnerability Assessment
- Scans databases and big data platforms for vulnerabilities and misconfigurations.
- Sensitive Data Discovery
- Identifies and classifies sensitive data, such as personally identifiable information (PII) and payment card data.
- Threat Detection and Alerts
- Detects potential data breaches and generates real-time alerts for security teams.
- User Behavior Analytics (UBA)
- Analyzes user activities to identify anomalies and prevent insider threats.
- Data Masking
- Protects sensitive data by masking or anonymizing it during non-production use cases.
- Cloud Data Security
- Extends data protection to cloud environments like AWS, Azure, and Google Cloud.
- Access Control and Policy Enforcement
- Enforces data access policies to ensure that only authorized users can access sensitive information.
- Forensic Analysis
- Provides detailed audit logs for investigating data-related incidents.
Features of IBM Guardium
- Data Discovery and Classification – Automatically identifies sensitive data and classifies it based on risk and sensitivity.
- Real-Time Activity Monitoring – Tracks all data activity to detect unauthorized access or anomalous behavior.
- Vulnerability Assessment – Scans for database vulnerabilities and suggests remediation actions.
- Policy Enforcement – Enforces security policies across databases, applications, and users.
- Automated Compliance Reporting – Simplifies audit preparation with pre-built reports for industry standards.
- Advanced Threat Detection – Uses AI and machine learning to identify and respond to potential threats.
- User Behavior Analytics (UBA) – Detects unusual user behavior to mitigate insider threats.
- Data Masking and Encryption – Protects sensitive data by masking or encrypting it to prevent unauthorized exposure.
- Integration with SIEM Tools – Connects with SIEM platforms like Splunk for enhanced threat analysis and response.
- Scalable Architecture – Supports diverse environments, including on-premises, hybrid, and cloud-based infrastructures.
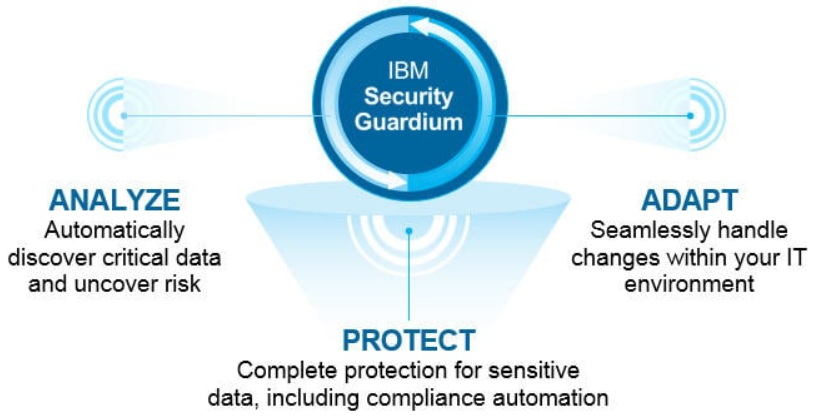
How IBM Guardium Works and Architecture
1. Data Collection and Monitoring
- IBM Guardium collects activity logs and metadata from databases, applications, and cloud environments.
- It monitors data access in real-time, ensuring that unauthorized or suspicious activity is flagged immediately.
2. Vulnerability and Risk Analysis
- The platform scans databases and big data environments to identify vulnerabilities, misconfigurations, and compliance gaps.
3. Policy Management and Enforcement
- Security teams can define and enforce custom policies for data access, usage, and retention.
4. Automated Alerts and Reports
- Guardium generates real-time alerts for suspicious activities and provides detailed reports for audits and investigations.
5. Integration and Extensibility
- The platform integrates with other security tools and SIEM solutions to enhance overall security management and incident response.
How to Install IBM Guardium
IBM Guardium is a comprehensive data security and protection solution that provides real-time monitoring, auditing, and protection for sensitive data across databases, big data platforms, and cloud environments. The installation process for IBM Guardium involves setting up the Guardium Gateway, Collector, and Database Activity Monitoring (DAM) components.
While IBM Guardium does not have a traditional “install-by-code” method, it can be installed programmatically using command-line tools, scripts, and IBM Guardium APIs. Below is a guide on how to install IBM Guardium and automate its configuration using scripts and IBM Guardium API.
1. Prerequisites
Before starting the installation, ensure the following:
- You have a valid IBM Guardium license.
- Linux or Windows systems for installing Guardium Gateway and Collector.
- IBM Guardium installation files (available from IBM’s official website or support portal).
2. Install IBM Guardium on Linux
IBM Guardium typically requires a Linux-based server for installation. Below are the steps to install the Guardium Gateway and Collector on a Linux system.
Step 1: Download IBM Guardium Installation Files
Log in to your IBM Passport Advantage account to download the installation files for IBM Guardium.
- Guardium Gateway and Collector are usually distributed as .tar.gz packages.
Step 2: Prepare Your System
Ensure that your system meets the minimum requirements for IBM Guardium:
- Operating System: RHEL, CentOS, or Ubuntu.
- Disk Space: At least 10 GB of free space for installation.
- Memory: 8 GB of RAM (16 GB recommended for larger environments).
Step 3: Install IBM Guardium Gateway and Collector
- Extract the IBM Guardium installation package:
tar -xvzf Guardium-installer.tar.gz
cd Guardium-installer
- Run the Installer:
The installer script can be run using the following command:
sudo ./install.sh
- Follow the installation prompts to:
- Accept the license agreement.
- Choose the installation directory.
- Set up necessary configurations, such as the Guardium Gateway and Collector components.
- Once the installation completes, the Guardium Gateway and Collector will be set up and can be verified using:
# Check Guardium service status
sudo systemctl status guardium-gateway
sudo systemctl status guardium-collector
Step 4: Configure IBM Guardium
After installation, you need to configure IBM Guardium for your environment, including:
- Configuring database sensors for monitoring.
- Setting up monitoring policies and audit logging.
- Integrating IBM Guardium with other security tools.
This can typically be done through the Guardium Console or using command-line tools.
3. Install IBM Guardium on Windows
For Windows-based installations, the process involves running the .exe installer package.
Step 1: Download the Guardium Installer
Download the Windows installer for IBM Guardium from the IBM Passport Advantage website.
Step 2: Run the Installer
Double-click the installer and follow the instructions to install IBM Guardium:
- Accept the license terms.
- Choose the installation path.
- Select the Guardium Gateway or Collector component.
Step 3: Verify the Installation
After installation, the Guardium service should be running. You can check this by navigating to the Windows Services panel and verifying the status of the Guardium services.
4. Automating IBM Guardium Configuration with CLI
After installing IBM Guardium, much of its configuration can be automated via the Guardium Command Line Interface (CLI).
Step 1: Use Guardium CLI for Configuration
Once installed, you can use the Guardium CLI to configure sensors, data sources, and policy settings. For example:
- Configuring a Database Sensor:
# Add a database sensor using Guardium CLI
guardiumcli -cmd "add sensor" -sensor_name "MySQL Sensor" -db_ip "192.168.1.100" -db_port 3306
- Creating a Policy:
guardiumcli -cmd "create policy" -policy_name "MySQL Activity Monitoring" -type "Audit"
Step 2: Guardium API for Advanced Automation
You can also use IBM Guardium REST APIs for further automation, such as retrieving security events, managing sensors, and handling alerts.
For example, to fetch security findings from Guardium using Python:
import requests
# Guardium API endpoint
api_url = "https://<guardium-server>/api/v1/findings"
# Authentication
auth = ('admin', 'your-password') # Use your credentials
# Fetch findings
response = requests.get(api_url, auth=auth)
# Check response status
if response.status_code == 200:
print("Security Findings:", response.json())
else:
print("Error fetching findings:", response.status_code)
Replace <guardium-server> with your Guardium server address and use valid authentication credentials.
5. Automate with Terraform
If you prefer infrastructure-as-code, Terraform can also be used to automate the deployment of IBM Guardium components, particularly when working with cloud environments.
provider "ibm" {
ibm_api_key = "your-ibm-api-key"
}
resource "ibm_guardium_gateway" "example" {
name = "Guardium-Gateway"
location = "us-south"
}
This is an example of how you could automate the deployment of Guardium Gateway on IBM Cloud using Terraform. You would need to have the appropriate IBM Guardium Terraform provider configured and access to your API keys.
6. Monitor and Maintain IBM Guardium
Once IBM Guardium is installed and configured, you can use the Guardium Console, CLI, or REST APIs to monitor the environment for security incidents and configure additional security policies or alerts. Regularly review findings and ensure the system is up-to-date with the latest patches.
Basic Tutorials of IBM Guardium: Getting Started
Step 1: Log in to Guardium
- Access the Guardium dashboard using your admin credentials.
Step 2: Add Data Sources
- Navigate to Settings > Data Sources.
- Configure connections to databases, cloud environments, or applications.
Step 3: Configure Policies
- Create custom policies for monitoring, access control, and compliance enforcement.
Step 4: Enable Vulnerability Scanning
- Go to Vulnerability Assessment.
- Schedule scans to identify and address risks in your environment.
Step 5: Review Alerts and Reports
- Check the Alerts section for suspicious activities and generate compliance reports from the Reports tab.
Step 6: Automate Responses
- Use predefined workflows to automate responses to common security incidents.