LogRhythm is a leading Security Information and Event Management (SIEM) platform designed to help organizations detect, analyze, and respond to security threats in real time. It provides centralized log management, advanced analytics, and automated incident response to enhance security operations and reduce response times. LogRhythm is widely recognized for its ability to simplify complex security environments, making it a go-to solution for modern Security Operations Centers (SOCs).
What is LogRhythm?
LogRhythm is a unified platform that combines SIEM, log management, user and entity behavior analytics (UEBA), and security orchestration, automation, and response (SOAR). It empowers organizations to monitor and analyze data from across their IT infrastructure, detect threats proactively, and streamline incident response processes. By using machine learning and behavioral analytics, LogRhythm delivers actionable insights to improve overall security posture.
Key Characteristics of LogRhythm:
- Centralized Monitoring: Aggregates logs and events from various sources for unified visibility.
- Advanced Analytics: Uses AI and machine learning to detect anomalies and uncover threats.
- Automated Incident Response: Streamlines workflows to mitigate threats faster.
- Compliance-Ready: Provides tools and reports to meet regulatory requirements like GDPR, HIPAA, and PCI DSS.
Top 10 Use Cases of LogRhythm
- Threat Detection and Response
- Identifies and mitigates security threats such as malware, ransomware, and advanced persistent threats (APTs) in real time.
- User Behavior Analytics (UBA)
- Detects anomalies in user activities, such as unauthorized access or account misuse, using UEBA.
- Compliance Management
- Simplifies compliance reporting and audit preparation for regulations like GDPR, HIPAA, and CCPA.
- Cloud Security Monitoring
- Monitors and secures cloud environments like AWS, Azure, and Google Cloud by analyzing logs and events.
- Endpoint Threat Monitoring
- Tracks endpoint activities to detect and block malicious behavior.
- Network Traffic Analysis
- Analyzes network logs to identify potential breaches, DDoS attacks, and lateral movements.
- Incident Investigation
- Provides forensic data and event correlation to investigate and respond to incidents effectively.
- Vulnerability Management
- Integrates with vulnerability scanners to prioritize and address critical security gaps.
- Security Automation and Orchestration
- Automates repetitive tasks like alert triage, threat hunting, and incident response.
- Integration with Threat Intelligence
- Enriches threat detection capabilities with real-time threat intelligence feeds.
Features of LogRhythm
- Advanced Threat Detection – Combines machine learning and behavioral analytics to detect sophisticated threats.
- Log Management and Correlation – Centralizes and normalizes log data for efficient analysis.
- User and Entity Behavior Analytics (UEBA) – Identifies anomalies in user and entity behavior patterns.
- Automated Incident Response – Provides playbooks and workflows for faster threat mitigation.
- Customizable Dashboards – Visualizes security metrics and incidents in real time.
- Compliance Reporting – Offers pre-built reports for regulatory standards such as PCI DSS and GDPR.
- Integration with Security Tools – Connects with third-party tools like firewalls, endpoint protection, and SIEMs.
- Threat Intelligence Integration – Incorporates global threat intelligence for enhanced detection.
- Real-Time Alerts – Generates prioritized alerts based on risk and severity.
- Scalable Architecture – Supports large-scale deployments across hybrid and cloud environments.
How LogRhythm Works and Architecture
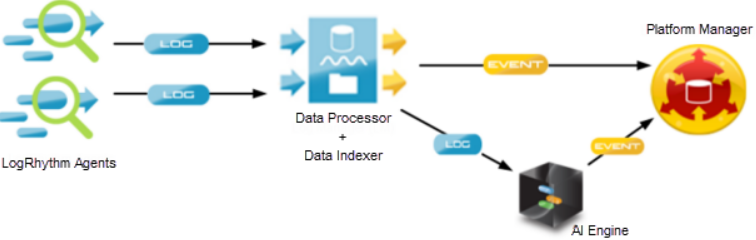
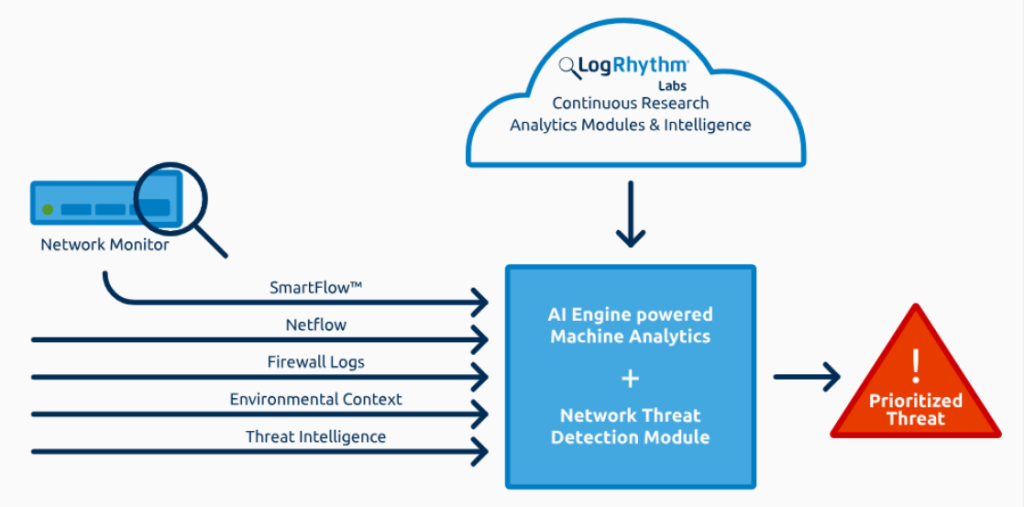
1. Data Ingestion and Normalization
- LogRhythm collects logs, events, and data from various sources, including network devices, endpoints, cloud platforms, and applications.
- The data is normalized into a consistent format for easier analysis.
2. Advanced Threat Detection
- It uses analytics, machine learning, and threat intelligence to detect known and unknown threats.
3. Incident Response
- Automates response workflows using pre-defined playbooks and integrates with SOAR capabilities for faster mitigation.
4. Centralized Management Console
- Provides a single interface for monitoring, analyzing, and managing security events across the organization.
5. Integration Ecosystem
- Works seamlessly with other security tools like firewalls, vulnerability scanners, and endpoint protection platforms.
How to Install LogRhythm
LogRhythm is a leading Security Information and Event Management (SIEM) platform that provides capabilities for threat detection, monitoring, and incident response. Installing LogRhythm involves setting up the LogRhythm Platform, which includes components such as LogRhythm Collectors, LogRhythm Processors, and the LogRhythm Console. This platform can be installed on both physical and virtual machines.
Here is a step-by-step guide on how to install LogRhythm in a typical enterprise environment.
1. Obtain LogRhythm Software
To start the installation, you need to obtain the LogRhythm installer package. LogRhythm software can be obtained from the official LogRhythm website or by contacting LogRhythm support for an installation package or trial version. You will need valid credentials to access the installer.
2. System Requirements
Before proceeding with the installation, ensure that your system meets the minimum requirements:
- Operating System: LogRhythm supports Windows Server (2012, 2016, or newer) for certain components and Linux (CentOS or RHEL) for others.
- RAM: At least 16 GB, but 32 GB or more is recommended for larger environments.
- Disk Space: 100 GB or more for the system, depending on the amount of data being processed.
- Processor: 4 cores or more (recommendation for production environments).
3. Download LogRhythm Software
Once you’ve received the installer from LogRhythm, you can begin downloading the necessary components for installation:
- LogRhythm Platform (All-in-one): This includes the management console and other components bundled together for smaller deployments.
- LogRhythm Collectors: Collectors are responsible for gathering log data from various sources (e.g., syslog, file collection).
- LogRhythm Processors: Processors analyze log data and execute security analytics.
4. Install LogRhythm Console
The LogRhythm Console is the web-based user interface that administrators use to configure, monitor, and analyze data. This can be installed on a Windows Server.
Windows Installation (LogRhythm Console):
- Run the LogRhythm Console Installer:
- If using a Windows Server, you can use the
.exeinstaller.
# Execute the installer LogRhythmConsoleInstaller.exe - If using a Windows Server, you can use the
- Follow the installation wizard to configure the following:
- Database Configuration: LogRhythm uses a PostgreSQL database or a Microsoft SQL Server to store event data. Ensure that the correct database is installed and connected.
- Networking Configuration: Configure the required ports for communication between the LogRhythm Console, Collectors, and Processors.
- After installation, the console should be accessible via a web browser on
https://<your-server-ip>:<port>(default port 443).
Verify the Installation:
After installation, ensure that the LogRhythm Console service is running by checking the service status on Windows:
# Check if LogRhythm Console service is running
Get-Service -Name LogRhythmConsole
5. Install LogRhythm Collectors
The LogRhythm Collectors are used to collect logs from various devices such as firewalls, servers, and applications. The installation of Collectors is done on the target machines (either on physical or virtual systems).
Linux Installation (LogRhythm Collector):
- Download the Collector Installer from the LogRhythm portal.
- Install the Collector: For RPM-based systems (e.g., CentOS/RHEL):
sudo rpm -ivh LogRhythmCollector.rpmFor DEB-based systems (e.g., Ubuntu/Debian):sudo dpkg -i LogRhythmCollector.deb - Start the Collector:
sudo systemctl start logrhythm-collector - Verify the Collector Status: Ensure the Collector is running by checking the service status:
sudo systemctl status logrhythm-collector
Windows Installation (LogRhythm Collector):
- Run the Collector Installer (
LogRhythmCollectorInstaller.exe) on your Windows Server. - The installer will configure the collector to communicate with the LogRhythm Console and other components.
- Start the LogRhythm Collector after installation. You can monitor its status through the Windows Services panel.
6. Install LogRhythm Processors
Processors are responsible for the analysis of logs. Depending on your deployment, you can install the LogRhythm Processors either on Windows Server or Linux. These components scale out for larger environments.
Step 1: Install Processors
- Download the Processor Installer from the LogRhythm portal.
- Install the Processor (on Linux or Windows) using the respective commands for RPM/DEB or EXE installers.
Step 2: Configure Processors
- After installation, you must configure the processors to communicate with the LogRhythm Console and Collectors.
- You will need to specify the indexing and data storage settings for log analysis.
7. Post-Installation Configuration
Once all components are installed:
- Configure Data Sources: Set up log sources (such as syslog servers, firewall logs, etc.) in the LogRhythm Console.
- Define Analytics: Set up rules and analytics for detecting security events.
- Configure Alerts: Set thresholds for event severity, and configure alerting rules for when critical events are detected.
8. Verify System Health
You can use the LogRhythm Health Monitoring dashboard to ensure that all components (Collectors, Processors, Console) are functioning properly. This provides visibility into performance metrics and potential issues in your deployment.
9. Automate Post-Installation Tasks with Scripts (Optional)
You can automate certain post-installation tasks such as configuring log sources and data inputs using REST APIs provided by LogRhythm.
Here is an example of how you might use Python to interact with the LogRhythm API to configure data sources:
import requests
# LogRhythm API URL and Authentication
api_url = "https://<your-logrhythm-console>/api/v1/log_sources"
api_key = "your_api_key_here"
headers = {
"Authorization": f"Bearer {api_key}",
"Content-Type": "application/json"
}
# Example: Add a new data source
data = {
"name": "MyFirewall",
"type": "syslog",
"address": "192.168.1.10",
"port": 514
}
response = requests.post(api_url, headers=headers, json=data)
if response.status_code == 201:
print("Data source added successfully")
else:
print(f"Failed to add data source: {response.status_code}")
10. Monitor and Maintain
Once installed, use LogRhythm’s Web Console to monitor your logs, analyze security events, and respond to incidents. Regularly check for software updates, new patches, and any issues with system performance.
Basic Tutorials of LogRhythm: Getting Started
Step 1: Log in to the LogRhythm Console
- Use your admin credentials to access the web-based console and explore its features.
Step 2: Add Data Sources
- Navigate to Admin > Data Sources.
- Add and configure log sources such as network devices, cloud platforms, and endpoints.
Step 3: Set Up Dashboards
- Create dashboards to visualize security metrics, real-time alerts, and trends.
Step 4: Configure Correlation Rules
- Go to AI Engine > Rules.
- Create rules to detect specific threats and prioritize alerts based on severity.
Step 5: Monitor Alerts and Incidents
- Use the Monitor section to view real-time alerts and investigate incidents.
Step 6: Automate Incident Response
- Implement playbooks and integrate with SOAR tools to automate incident containment and remediation.