
McAfee Enterprise Security Manager (ESM) is a Security Information and Event Management (SIEM) platform designed to provide real-time threat detection, incident response, and centralized security management. By collecting and analyzing data from across the organization’s IT infrastructure, McAfee ESM enables security teams to identify and respond to threats efficiently. The platform leverages advanced correlation rules, analytics, and threat intelligence to improve the organization’s overall security posture.
What is McAfee Enterprise Security Manager?
McAfee Enterprise Security Manager is a SIEM solution that helps organizations detect, prioritize, and respond to security incidents by providing real-time visibility into events and logs. It aggregates data from endpoints, networks, applications, and other sources to analyze potential threats. By incorporating threat intelligence, McAfee ESM enables organizations to respond proactively to evolving cyber threats.
Key Characteristics of McAfee ESM:
- Real-Time Threat Detection: Monitors and identifies security incidents as they occur.
- Log Management and Correlation: Collects and analyzes log data from multiple sources.
- Scalability: Supports large-scale environments with distributed deployments.
- Threat Intelligence Integration: Leverages McAfee Global Threat Intelligence (GTI) for proactive threat detection.
Top 10 Use Cases of McAfee Enterprise Security Manager
- Threat Detection and Response
- Identifies and mitigates threats such as malware, ransomware, and phishing attacks in real time.
- Compliance Management
- Simplifies compliance reporting for regulations like GDPR, HIPAA, and PCI DSS by generating detailed audit logs and reports.
- User Behavior Analytics (UBA)
- Detects insider threats and compromised accounts by analyzing user activities and identifying anomalies.
- Network Security Monitoring
- Tracks network traffic to detect unauthorized access, lateral movement, and data exfiltration.
- Incident Investigation
- Provides forensic tools for investigating the root cause and scope of security incidents.
- Cloud Security Monitoring
- Secures cloud environments like AWS and Azure by analyzing log data and identifying vulnerabilities.
- Advanced Persistent Threat (APT) Detection
- Detects sophisticated attacks through advanced correlation and anomaly detection.
- Vulnerability Management
- Integrates with vulnerability scanners to correlate vulnerability data with threat information.
- Security Automation and Orchestration
- Automates response workflows to reduce manual intervention and improve efficiency.
- Threat Intelligence Integration
- Incorporates McAfee GTI and third-party threat intelligence feeds to enrich threat detection.
Features of McAfee Enterprise Security Manager
- Real-Time Threat Monitoring – Continuously monitors and analyzes events to detect threats as they occur.
- Advanced Correlation Rules – Correlates events across multiple data sources to identify complex attack patterns.
- Centralized Log Management – Aggregates and normalizes logs for comprehensive analysis.
- Customizable Dashboards – Offers real-time visual insights into security metrics and incidents.
- Automated Incident Response – Automates remediation tasks using pre-defined playbooks and integrations.
- Scalability – Supports distributed environments, making it suitable for large enterprises.
- Threat Intelligence Integration – Leverages global threat intelligence to stay ahead of emerging threats.
- Compliance Reporting – Provides pre-configured reports to meet regulatory requirements.
- Behavioral Analytics – Monitors user and system behavior to identify anomalies and potential threats.
- Integration Ecosystem – Works with McAfee and third-party security tools for seamless security management.
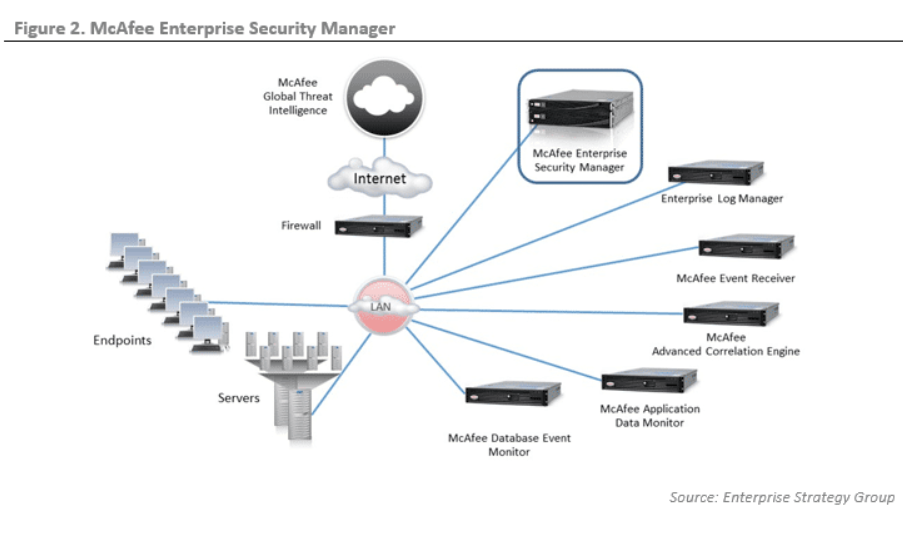
How McAfee Enterprise Security Manager Works and Architecture
1. Data Ingestion and Normalization
McAfee ESM collects logs, events, and flow data from a variety of sources, including endpoints, network devices, and cloud environments. The data is normalized for consistency, enabling effective analysis and correlation.
2. Threat Detection and Correlation
The platform uses advanced correlation rules, machine learning, and analytics to detect suspicious activities and prioritize alerts based on severity.
3. Centralized Management Console
McAfee ESM provides a single interface for monitoring security events, managing alerts, and generating reports.
4. Integration with Threat Intelligence
The platform integrates with McAfee GTI and other threat intelligence feeds to provide context and enhance detection capabilities.
5. Automated Workflows
McAfee ESM includes automation features for alert triage, incident response, and remediation, helping organizations save time and resources.
How to Install McAfee Enterprise Security Manager
McAfee Enterprise Security Manager (ESM) is a centralized management system for McAfee security solutions that helps monitor and respond to security events across an enterprise environment. Installing McAfee ESM typically involves setting up the server, installing required components, and configuring network settings. While most of the installation process requires manual configuration, much of the deployment can be automated through scripts, command-line tools, and APIs once the necessary components are downloaded.
General Steps to Install McAfee Enterprise Security Manager (ESM) Using Code
1. Download McAfee ESM
- Obtain the McAfee ESM installer from the McAfee Website or through your McAfee support portal. You will need a valid subscription to access the installer.
- The installer is typically available as an ISO file for physical or virtual machine deployments.
2. System Requirements
Ensure that the system meets the following minimum requirements:
- Operating System: Red Hat-based Linux distributions (RHEL, CentOS) or Windows Server (2016 or later).
- RAM: At least 8 GB for basic installations (recommended 16 GB or more).
- Disk Space: At least 100 GB of free space for logs and events.
- Processor: 2-4 cores, depending on deployment size.
3. Prepare the Installation Media
- If using a physical machine, burn the ISO file to a DVD or create a bootable USB drive.
- For virtual machine (VM) installation, mount the ISO file in the VM’s optical drive or attach it directly.
4. Install McAfee ESM (Using Command-Line for Linux)
The installation of McAfee ESM on Linux-based systems can be done via the command line after booting from the ISO.
Step 1: Boot and Begin Installation
- Boot the machine or virtual machine from the McAfee ESM ISO.
- Once the system boots, select Install to begin the process.
Step 2: Install McAfee ESM
For Linux-based installations, after the boot, you will typically see a command-line installation option. You can use install.sh to automate the process.
# Log into the system and start the installer script
sudo ./install.sh
The installer script will guide you through the following steps:
- Disk partitioning (if applicable).
- Network configuration (setting up the static IP, gateway, DNS).
- Configuration of McAfee ESM settings (including hostname and admin credentials).
Step 3: Post-Installation Configuration
- Once the installation completes, the McAfee ESM service should be running. You can verify this with the following command:
# Verify McAfee ESM service is running
sudo systemctl status mcafee-esm
- Log in to McAfee ESM Web Console via
https://<hostname_or_ip>:8443using the credentials set during the installation.
Step 4: Configure McAfee ESM via Command-Line
You can also configure McAfee ESM services using its built-in configuration utilities.
- Use
esmclifor command-line management tasks like:
# Example of setting the management IP via esmcli
esmcli set-network --hostname <hostname> --ip <ip_address>
5. Install McAfee ESM (Using Command-Line for Windows)
For Windows Server, the process is similar but involves running an executable installer.
Step 1: Run the Installer
Run the McAfee ESM installer executable (e.g., McAfeeESMInstaller.exe) from the Command Prompt:
# Silent installation using command line
McAfeeESMInstaller.exe /quiet /install
This will install McAfee ESM without user interaction. You can also use additional arguments to specify installation directories or configuration options.
Step 2: Post-Installation Configuration
After the installation, McAfee ESM will typically start the service automatically. You can verify the service status in Windows Services.
# Check McAfee ESM service status on Windows
Get-Service McAfeeESM
Once the installation completes, navigate to https://<hostname_or_ip>:8443 in your browser to access the McAfee ESM Console.
6. Automate Deployment for Multiple Machines (Windows Example)
For large-scale deployments across multiple Windows machines, you can use PowerShell to automate the installation process.
PowerShell Script for Installing McAfee ESM on Multiple Machines:
# List of remote computers
$computers = Get-Content -Path "C:\computers.txt"
foreach ($computer in $computers) {
Invoke-Command -ComputerName $computer -ScriptBlock {
Start-Process "C:\path\to\McAfeeESMInstaller.exe" -ArgumentList "/quiet /install" -Wait
}
}
This script reads the list of computer names from computers.txt and installs McAfee ESM remotely on each machine.
7. Post-Installation Tasks and Configuration
After installation, configure McAfee ESM by:
- Adding log sources such as firewalls, intrusion detection systems (IDS), or other security devices.
- Configuring alerting and monitoring policies.
- Enabling compliance features if needed for regulatory reporting.
8. Monitor McAfee ESM Services
Once the system is up and running, you can monitor the McAfee ESM services using the web interface or programmatically via REST APIs.
# Example to check logs from McAfee ESM CLI
sudo /opt/McAfee/esm/bin/esmcli show-log --level info
You can also automate tasks like updating the system, managing incidents, or querying the status of data feeds using the McAfee ESM REST APIs.
9. Maintaining and Updating McAfee ESM
Keep McAfee ESM up to date by installing patches and updates via the McAfee ePolicy Orchestrator (ePO) or by using the CLI for manual updates:
# Updating McAfee ESM to the latest patch
sudo /opt/McAfee/esm/bin/esmcli updateBasic Tutorials of McAfee Enterprise Security Manager: Getting Started
Step 1: Log in to the Management Console
- Access the McAfee ESM console using your admin credentials to start managing the platform.
Step 2: Add Log Sources
- Navigate to Data Sources in the console.
- Configure log sources like firewalls, endpoint tools, and network devices.
Step 3: Configure Correlation Rules
- Use the Rules Editor to create or customize correlation rules for detecting specific threats.
Step 4: Set Up Dashboards
- Build dashboards to visualize security metrics, alerts, and trends in real time.
Step 5: Investigate Incidents
- Use the Event Explorer to analyze incidents, correlate data, and determine root causes.
Step 6: Automate Responses
- Implement playbooks to automate repetitive tasks like alert triage and threat remediation.