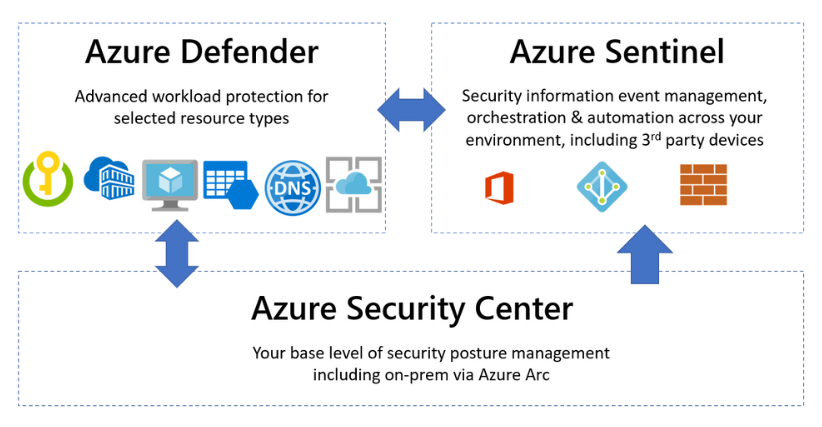
Microsoft Azure Security Center is a unified cloud security management solution designed to provide advanced threat protection for workloads running in Azure, on-premises, and other cloud environments. By leveraging AI and built-in security intelligence, Azure Security Center helps organizations strengthen their security posture, protect against threats, and maintain compliance across their hybrid and multi-cloud environments.
What is Microsoft Azure Security Center?
Azure Security Center is a cloud-native security management tool that provides centralized visibility, threat detection, and security policy management for Azure resources and hybrid infrastructures. It offers integrated tools to monitor and protect workloads, detect vulnerabilities, and automate responses to security incidents. With its real-time threat intelligence and seamless integration with Microsoft Defender, Azure Security Center ensures robust protection for enterprise IT assets.
Key Characteristics of Azure Security Center:
- Cloud-Native Security: Built specifically for Azure and hybrid cloud infrastructures.
- Unified Threat Protection: Provides advanced threat detection and response for workloads and services.
- Continuous Security Assessment: Monitors security posture and suggests recommendations for improvement.
- Integration with Azure Defender: Extends protection to hybrid and multi-cloud environments.
Top 10 Use Cases of Microsoft Azure Security Center
- Threat Detection and Response
- Identifies and mitigates security threats to Azure workloads and hybrid environments in real time.
- Cloud Security Posture Management (CSPM)
- Continuously assesses your cloud resources for misconfigurations and compliance violations.
- Hybrid Security Monitoring
- Extends visibility and threat protection to on-premises and multi-cloud workloads.
- Compliance Management
- Automates compliance checks against standards like CIS, PCI DSS, and ISO 27001.
- Virtual Machine Security
- Protects virtual machines against vulnerabilities, malware, and brute-force attacks.
- Vulnerability Assessment
- Scans workloads for vulnerabilities and provides actionable remediation steps.
- File Integrity Monitoring
- Tracks changes to critical files and directories to detect unauthorized modifications.
- Just-in-Time (JIT) VM Access
- Reduces exposure to brute-force attacks by allowing time-limited access to virtual machines.
- Container Security
- Secures containerized applications running on Azure Kubernetes Service (AKS) by detecting vulnerabilities and runtime threats.
- Integration with SIEM and SOAR
- Enhances incident response by integrating with Microsoft Sentinel and other SIEM tools.
Features of Microsoft Azure Security Center
- Advanced Threat Protection – Detects and prevents threats using machine learning and threat intelligence.
- Security Recommendations – Provides actionable recommendations to strengthen your security posture.
- Compliance Monitoring – Ensures compliance with regulatory standards and provides detailed reports.
- Hybrid Cloud Support – Monitors and protects resources across on-premises, Azure, and other cloud providers.
- Just-in-Time VM Access – Minimizes attack surfaces by granting limited-time access to virtual machines.
- Vulnerability Assessment – Identifies vulnerabilities in workloads and suggests remediation steps.
- File Integrity Monitoring – Tracks changes to critical files and detects unauthorized modifications.
- Integration with Azure Defender – Offers extended threat protection for virtual machines, storage, databases, and Kubernetes.
- Custom Security Policies – Enables the creation of tailored security policies to meet specific business requirements.
- Centralized Security Dashboard – Provides a unified view of security alerts, recommendations, and compliance status.
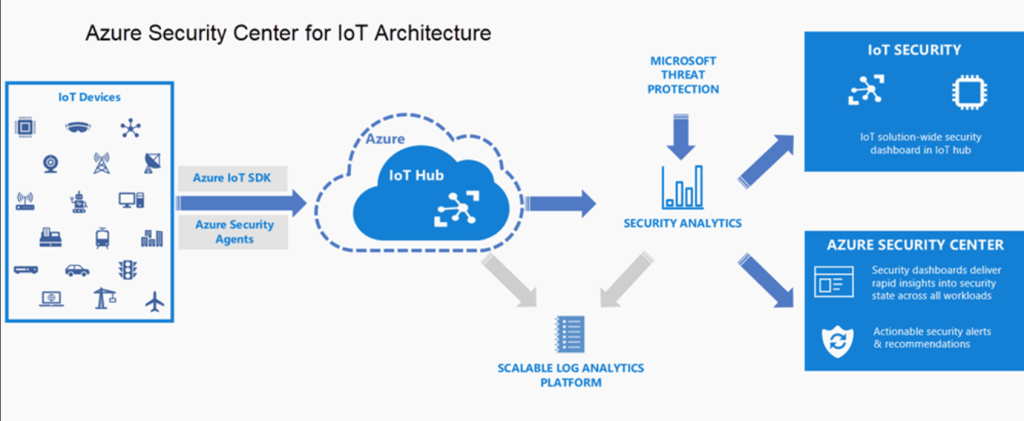
How Microsoft Azure Security Center Works and Architecture
1. Data Collection and Analysis
Azure Security Center collects telemetry data from Azure resources, on-premises workloads, and multi-cloud environments. It uses AI and machine learning to analyze the data and detect potential security risks.
2. Continuous Assessment
The platform continuously evaluates the security posture of your environment, identifies misconfigurations, and provides recommendations for improvement.
3. Threat Detection
By leveraging Microsoft’s threat intelligence and machine learning, Azure Security Center detects and responds to advanced threats in real time.
4. Hybrid Security Integration
Azure Security Center integrates with Azure Arc to extend its capabilities to on-premises and multi-cloud environments.
5. Centralized Management
All security data, alerts, and recommendations are consolidated into a centralized dashboard, making it easier for administrators to monitor and respond to threats.
How to Install Microsoft Azure Security Center
Microsoft Azure Security Center is a unified security management system that provides advanced threat protection across your Azure resources. It helps you monitor and manage the security of Azure-based services, offering tools for identifying vulnerabilities, managing compliance, and responding to security threats.
While Azure Security Center does not have a direct “installation” like traditional software, it can be enabled and configured programmatically using Azure CLI, PowerShell, or Azure Resource Manager (ARM) templates. Below are the steps to enable and configure Azure Security Center programmatically.
1. Prerequisites
Before you begin:
- Ensure you have an Azure subscription and access to the Azure Portal.
- Make sure that you have Azure CLI, Azure PowerShell, or ARM templates set up in your environment.
- Permissions: Make sure you have the necessary permissions to enable and configure Azure Security Center (e.g., Owner or Security Admin role).
2. Enable Azure Security Center Using Azure CLI
You can enable Azure Security Center using the Azure CLI by enabling Security Center Standard tier, which unlocks advanced security features and provides full visibility into your Azure resources.
Step 1: Install Azure CLI (if not installed)
First, make sure that Azure CLI is installed on your system. If you haven’t already, you can install it from Azure CLI download page.
For Linux, you can install it using the following commands:
# For Ubuntu
sudo apt-get update
sudo apt-get install azure-cli
For Windows, use the MSI installer from the Azure website.
Step 2: Log in to Azure
You need to authenticate using your Azure credentials:
az login
This will open a login page, or you can use a service principal if automating the process in a non-interactive way.
Step 3: Enable Azure Security Center Standard Tier
Azure Security Center comes with a free tier and a standard tier. To use advanced capabilities like threat protection, vulnerability assessment, and security policy management, you need to enable the Standard tier.
To enable Security Center Standard Tier, use the following command:
az security pricing create --name 'Default' --tier 'Standard'
This enables the Standard Tier for all resources in your subscription.
Step 4: Check Security Center Status
You can verify if the Security Center is enabled by running:
az security pricing show --name 'Default'
This will display the pricing tier status for Security Center. If it shows the Standard tier, it is enabled for your subscription.
3. Enable Azure Security Center Using PowerShell
If you prefer using PowerShell, you can enable Azure Security Center with the following steps.
Step 1: Install Azure PowerShell (if not installed)
First, install the Azure PowerShell module. Run the following in PowerShell:
Install-Module -Name Az -AllowClobber -Force -Scope CurrentUser
Step 2: Log in to Azure PowerShell
Authenticate with your Azure account:
Connect-AzAccount
Step 3: Enable Azure Security Center Standard Tier
Enable the Standard Tier of Azure Security Center for your subscription:
Set-AzSecurityPricing -PricingTier "Standard" -Name "Default"
Step 4: Verify Security Center Status
To verify if Azure Security Center is set to the Standard Tier:
Get-AzSecurityPricing -Name "Default"
This will display the pricing tier status for Security Center.
4. Enable Azure Security Center Using ARM Templates
You can also enable Azure Security Center using ARM templates for automated deployments. Below is an example ARM template to enable Security Center Standard tier for a subscription.
Step 1: Create an ARM Template
Here’s a simple example of an ARM template that enables Azure Security Center with the Standard tier:
{
"$schema": "https://schema.management.azure.com/schemas/2019-08-01/subscriptionDeploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Security/pricings",
"apiVersion": "2019-01-01",
"name": "Default",
"properties": {
"pricingTier": "Standard"
}
}
]
}
Step 2: Deploy the ARM Template
You can deploy the template using Azure CLI:
az deployment sub create --location eastus --template-file ./securitycenter-enable-template.json
This will deploy the template to your subscription and enable the Standard tier for Azure Security Center.
5. Monitor and Use Azure Security Center
Once you have enabled Azure Security Center in the Standard tier, you can monitor the security state of your resources through the Azure Portal or use Azure CLI/PowerShell to retrieve security findings, generate reports, and manage security policies.
Step 1: List Security Findings via CLI
You can list the security findings with the following CLI command:
az security alert list --resource-group <your-resource-group> --output table
This will show the security findings in a tabular format for the specified resource group.
Step 2: Use Azure Security Center APIs for Integration
Azure Security Center also provides REST APIs to interact with the platform programmatically. For example, you can use the Azure Security Center API to list all security policies or retrieve security alerts.
Example API request to get security alerts:
curl -X GET "https://management.azure.com/subscriptions/{subscriptionId}/providers/Microsoft.Security/alerts?api-version=2019-01-01" \
-H "Authorization: Bearer <access_token>"
6. Automate Post-Installation Tasks
After enabling Azure Security Center, you can automate tasks such as:
- Setting up Security Policies: Use Azure Policy to enforce compliance with security standards.
- Configuring Data Sources: Integrate with Azure services like Azure Firewall, Azure Defender, or third-party services to collect security findings.
- Alert Configuration: Create alerts for security events using Azure Monitor.
Basic Tutorials of Microsoft Azure Security Center: Getting Started
Step 1: Access Azure Security Center
- Log in to the Azure Portal and navigate to Microsoft Defender for Cloud.
Step 2: Assess Your Security Posture
- View the Secure Score to understand your current security posture.
- Review recommendations and implement suggested changes to improve your score.
Step 3: Enable Azure Defender
- Activate Azure Defender for workloads such as virtual machines, Kubernetes clusters, and storage accounts.
Step 4: Monitor Security Alerts
- Go to the Security Alerts section to view and manage detected threats in your environment.
Step 5: Automate Remediation
- Use Azure Logic Apps to create automated workflows for responding to specific security findings.
Step 6: Generate Compliance Reports
- Navigate to the Regulatory Compliance tab to review and download compliance reports.