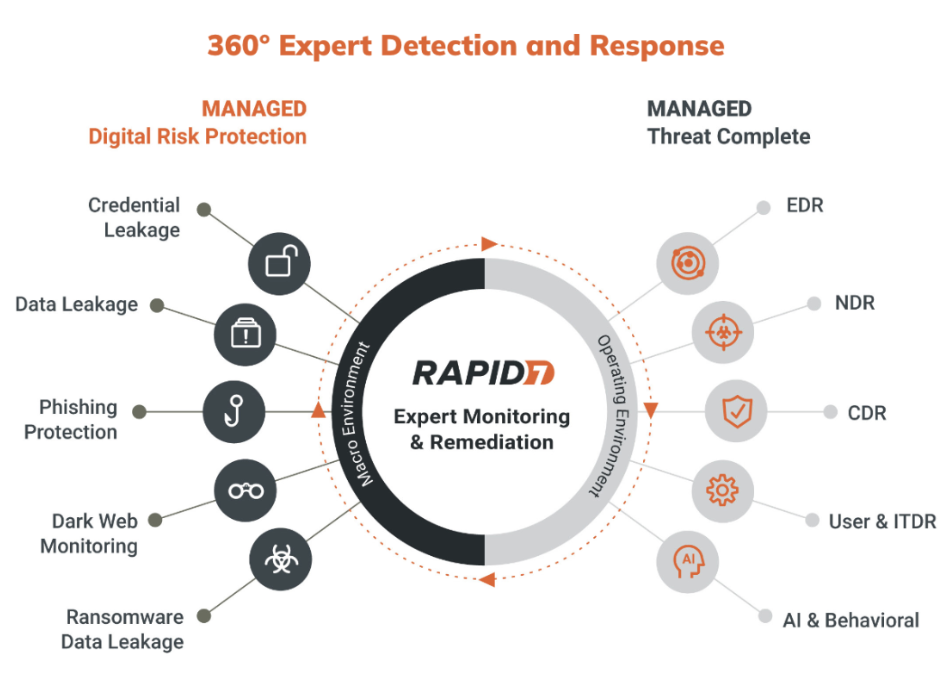
Rapid7 is a leading cybersecurity platform that provides organizations with tools for vulnerability management, incident detection and response, penetration testing, and application security. It offers comprehensive solutions to help businesses improve their security posture, reduce risk, and protect critical assets. With its advanced automation, threat intelligence, and analytics capabilities, Rapid7 helps organizations detect and respond to threats faster.
What is Rapid7?
Rapid7 is a cloud-based cybersecurity platform that enables organizations to manage vulnerabilities, detect cyber threats, and automate security workflows. It offers an integrated suite of products and services, including InsightVM for vulnerability management, InsightIDR for threat detection and response, and InsightAppSec for application security testing. Rapid7’s solutions provide visibility into security risks and facilitate efficient responses to mitigate them.
Key Characteristics of Rapid7:
- Comprehensive Security Platform: Covers vulnerability management, incident detection, response, and application security.
- Automation and Orchestration: Automates repetitive tasks to improve security operations efficiency.
- Threat Intelligence: Leverages real-time threat intelligence to detect and respond to emerging threats.
- Cloud-Native Architecture: Provides scalable and flexible deployment options for businesses of all sizes.
Top 10 Use Cases of Rapid7
- Vulnerability Management
- Identify, prioritize, and remediate vulnerabilities in IT assets using Rapid7 InsightVM.
- Threat Detection and Response
- Detect malicious activity and respond to threats with InsightIDR, Rapid7’s SIEM solution.
- Application Security Testing
- Test and secure web applications against vulnerabilities with InsightAppSec.
- Penetration Testing
- Simulate real-world attacks to identify security weaknesses using Rapid7 Metasploit.
- Cloud Security
- Monitor and secure cloud infrastructure against misconfigurations and unauthorized access.
- Endpoint Protection
- Detect and respond to endpoint threats, ensuring devices are safeguarded from attacks.
- Incident Response
- Automate incident response workflows to contain and mitigate security breaches efficiently.
- Compliance Management
- Simplify compliance reporting for standards like GDPR, HIPAA, and PCI-DSS.
- User Behavior Analytics
- Monitor user behavior to detect insider threats and compromised accounts.
- Security Orchestration and Automation (SOAR)
- Automate repetitive security tasks and integrate workflows across multiple tools to improve operational efficiency.
Features of Rapid7
- InsightVM for Vulnerability Management – Provides visibility into vulnerabilities across assets and prioritizes remediation based on risk.
- InsightIDR for Threat Detection and Response – Combines user behavior analytics and SIEM capabilities to detect advanced threats.
- InsightAppSec for Application Security – Tests and protects web applications from vulnerabilities and exploits.
- Metasploit for Penetration Testing – A powerful open-source framework for simulating real-world attacks.
- Threat Intelligence Integration – Uses real-time threat intelligence to identify and mitigate risks.
- Automation and Orchestration – Automates security workflows to improve efficiency and reduce response times.
- Cloud Security Monitoring – Monitors cloud environments for misconfigurations, vulnerabilities, and compliance gaps.
- Incident Reporting and Analytics – Offers detailed reporting and dashboards for incident analysis and security posture assessment.
- Customizable Dashboards – Provides insights into vulnerabilities, threats, and remediation progress.
- Scalable Deployment Options – Supports cloud-based, on-premises, and hybrid deployments.
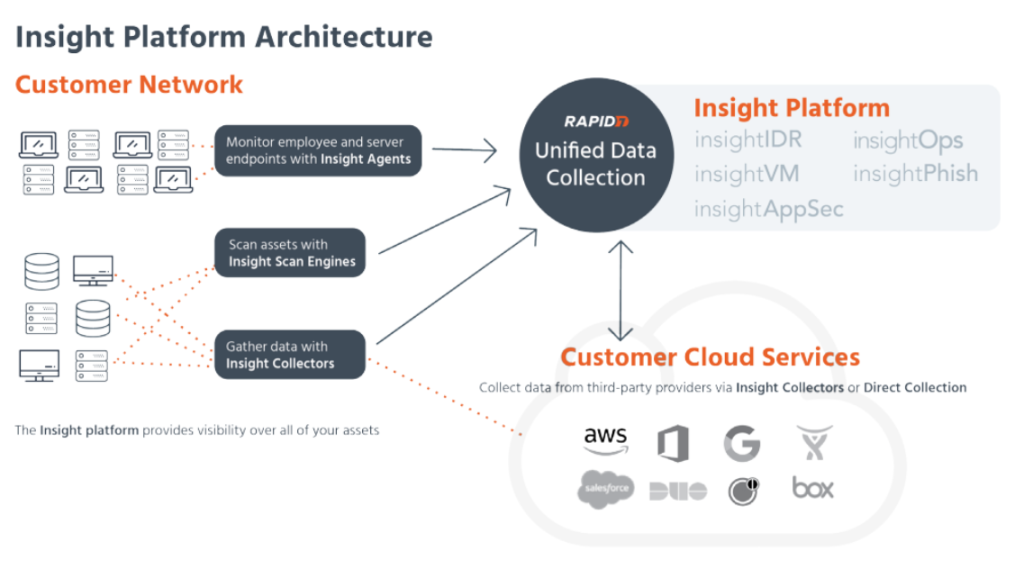
How Rapid7 Works and Architecture
1. Data Collection and Analysis
- Rapid7 collects data from endpoints, networks, applications, and cloud environments using agents, integrations, and APIs.
- The collected data is analyzed using advanced machine learning algorithms to identify vulnerabilities and threats.
2. Threat Detection and Response
- Rapid7 InsightIDR uses user behavior analytics and real-time threat intelligence to detect anomalous activities.
- Automated response workflows enable rapid containment and mitigation of threats.
3. Vulnerability Management
- InsightVM scans IT assets for vulnerabilities, assigns risk scores, and provides actionable recommendations for remediation.
4. Application Security Testing
- InsightAppSec scans web applications for vulnerabilities and integrates with development pipelines to secure code before deployment.
5. Integration and Orchestration
- Rapid7 integrates with third-party tools like SIEMs, endpoint protection platforms, and cloud services to provide a unified security ecosystem.
How to Install Rapid7
Rapid7 provides various security solutions, with InsightVM and Nexpose being two of the most commonly installed products for vulnerability management. These tools are typically set up via installation packages, and while they don’t have a “code-based” installation process like some software, you can automate or script parts of the installation process, particularly for Linux servers. Below is a guide for installing Rapid7 InsightVM (formerly Nexpose) and automating the setup with code, focusing on installation and integration tasks.
Steps to Install Rapid7 InsightVM (or Nexpose) Using Code:
1. Prepare Your Environment
Ensure that your system meets the necessary requirements for InsightVM or Nexpose:
- Operating System: Linux (CentOS, RHEL, Ubuntu), Windows Server
- Database: PostgreSQL (used by default, can be configured with other databases)
- Memory: Minimum 8 GB of RAM, recommended 16 GB or more
- Storage: 100 GB or more depending on the number of assets being scanned
2. Download the Installer
Rapid7 InsightVM and Nexpose are usually downloaded from the Rapid7 website. You’ll need a valid Rapid7 account or trial license to access the installer.
- For Linux, download the installer (e.g.,
.tar.gzor.rpm) from the Rapid7 website. - For Windows, download the
.exeinstaller.
3. Automated Installation on Linux
For Linux-based installations, you can automate the download and installation process using a bash script.
Here’s an example of how to automate the process using bash:
Step 1: Download the Installer
# Set the URL for the Rapid7 InsightVM installer
INSTALLER_URL="https://download2.rapid7.com/download/InsightVM"
# Define the file names for different Linux distributions
INSTALLER_FILE="rapid7_installer.tar.gz"
# Download the installer
wget -O $INSTALLER_FILE $INSTALLER_URL
Step 2: Extract the Installer
# Extract the downloaded installer
tar -xvzf $INSTALLER_FILE
Step 3: Run the Installation
cd rapid7-installer # Navigate to the extracted folder
# Start the installation process
sudo ./install.sh
During the installation process, you will be prompted to configure a few things, such as the database and the server configuration. You can automate some of this by passing parameters to the installer script (for example, specifying the database host, port, and credentials).
Step 4: Setup Database (Optional)
If you’re setting up a PostgreSQL database, you can configure it through the script or manually by editing the configuration files.
# Example: Configuring PostgreSQL as the database backend
sudo vi /opt/rapid7/insightvm/config/database.yml
You can edit this file to include your database credentials if you’re using a custom database.
4. Automate the Installation for Windows (Using PowerShell)
For Windows, you can automate the installation using a PowerShell script.
Step 1: Download the Installer
You can use PowerShell to download the installer for Rapid7 InsightVM:
$installerUrl = "https://download2.rapid7.com/download/InsightVM/rapid7_installer.exe"
$installerPath = "C:\path\to\rapid7_installer.exe"
Invoke-WebRequest -Uri $installerUrl -OutFile $installerPath
Step 2: Run the Installer
# Run the installer silently
Start-Process -FilePath $installerPath -ArgumentList "/S /D=C:\Rapid7" -Wait
This command runs the installer with the /S flag for silent installation, meaning it will not prompt for user input during the installation process.
5. Access the Rapid7 Console
After installation, the Rapid7 console can typically be accessed via a web browser on https://<your-server-ip>:3780 (or another port if configured differently). You will need to configure the initial setup (database, credentials, etc.) through the web interface.
6. Automate Configuration and Integration
Once installed, you may want to automate tasks like adding assets, defining scan schedules, and setting up alerting. You can do this using the Rapid7 REST API.
Here’s an example of interacting with the Rapid7 REST API to fetch information about assets:
import requests
# Set the base URL for Rapid7 InsightVM
base_url = "https://your-rapid7-instance.com/api/3"
api_key = "your_api_key"
# Define the headers
headers = {
"Authorization": f"APIKey {api_key}",
"Content-Type": "application/json"
}
# Get a list of assets
response = requests.get(f"{base_url}/assets", headers=headers)
# Check if the request was successful
if response.status_code == 200:
assets = response.json()
print("Assets:", assets)
else:
print(f"Failed to fetch assets: {response.status_code}")
This script authenticates via the API and fetches information about assets in your environment. You can automate creating assets, defining scan templates, and setting up alerting or reporting.
7. Integrating with SIEM Tools
Rapid7 InsightVM integrates with SIEM tools like Splunk for alerting and data analysis. You can configure these integrations through the InsightVM interface or programmatically via the API.
Basic Tutorials of Rapid7: Getting Started
Step 1: Install InsightVM
- Log in to the Rapid7 console and deploy InsightVM.
- Scan your IT environment for vulnerabilities and review the risk scores.
Step 2: Set Up InsightIDR
- Enable log collection and user behavior analytics.
- Configure threat detection rules to identify suspicious activities.
Step 3: Use InsightAppSec
- Connect your web applications to InsightAppSec.
- Scan for vulnerabilities and generate detailed reports for remediation.
Step 4: Automate Workflows
- Create automation workflows using Rapid7’s built-in orchestration tools.
- Test workflows to ensure seamless execution during incident response.
Step 5: Generate Reports
- Access the reporting module to generate compliance and security posture reports.
- Share reports with stakeholders to track progress and demonstrate risk reduction.