
Splunk Enterprise Security (Splunk ES) is a powerful security information and event management (SIEM) solution that helps organizations detect, investigate, and respond to cyber threats in real time. By leveraging machine learning, advanced analytics, and data visualization, Splunk ES provides actionable insights into security incidents across an organization’s IT environment. It integrates seamlessly with existing tools and platforms, making it a go-to solution for modern security operations centers (SOCs).
What is Splunk Enterprise Security?
Splunk Enterprise Security is a data-driven SIEM platform designed to centralize, analyze, and visualize security-related data. It enables security teams to monitor real-time activity, detect anomalies, and respond to threats proactively. Splunk ES is built on the Splunk platform, which processes massive amounts of machine data from various sources, including network devices, servers, applications, and cloud environments.
Key Characteristics of Splunk Enterprise Security:
- Real-Time Threat Detection: Monitors and identifies threats as they emerge.
- Advanced Analytics: Uses machine learning to analyze data and uncover hidden patterns.
- Centralized Security Operations: Consolidates security data from multiple sources for streamlined management.
- Customizable Dashboards: Provides visual insights tailored to organizational needs.
Top 10 Use Cases of Splunk Enterprise Security
- Threat Detection and Response
- Identifies and responds to malicious activities like phishing, malware, and insider threats in real time.
- User Behavior Analytics (UBA)
- Monitors user activities to detect anomalous behavior indicative of compromised accounts or insider threats.
- Compliance Management
- Ensures adherence to regulatory requirements like GDPR, HIPAA, and PCI DSS by providing detailed audit trails.
- Endpoint Security Monitoring
- Tracks endpoint activities to detect and prevent unauthorized access or data exfiltration.
- Cloud Security Monitoring
- Secures cloud environments by analyzing log data from AWS, Azure, and Google Cloud.
- Network Traffic Analysis
- Monitors network traffic to identify potential threats, such as DDoS attacks or suspicious data transfers.
- Incident Investigation and Forensics
- Provides detailed logs and analytics for root cause analysis of security incidents.
- Security Orchestration, Automation, and Response (SOAR)
- Automates repetitive security tasks and integrates with existing tools for faster response.
- Vulnerability Management
- Identifies and prioritizes vulnerabilities in IT assets to reduce exposure to cyber threats.
- Threat Intelligence Integration
- Leverages global threat intelligence feeds to enhance detection and response capabilities.
Features of Splunk Enterprise Security
- Real-Time Threat Monitoring – Continuously monitors and analyzes security data to detect threats instantly.
- Incident Investigation – Enables in-depth forensic analysis of security events for root cause identification.
- Risk-Based Alerting – Prioritizes alerts based on risk scores to focus on the most critical incidents.
- User Behavior Analytics (UBA) – Detects anomalies in user behavior using advanced machine learning models.
- Customizable Dashboards – Offers visual representations of security metrics and activities tailored to organizational needs.
- Integration with Third-Party Tools – Supports integration with firewalls, endpoint protection, and threat intelligence platforms.
- Advanced Correlation Searches – Correlates events across multiple sources to identify complex attack patterns.
- Automated Response Workflows – Facilitates automated incident response through integrations with SOAR tools.
- Compliance Reporting – Generates detailed reports to support regulatory compliance requirements.
- Scalable Architecture – Processes large volumes of data efficiently for enterprises of all sizes.
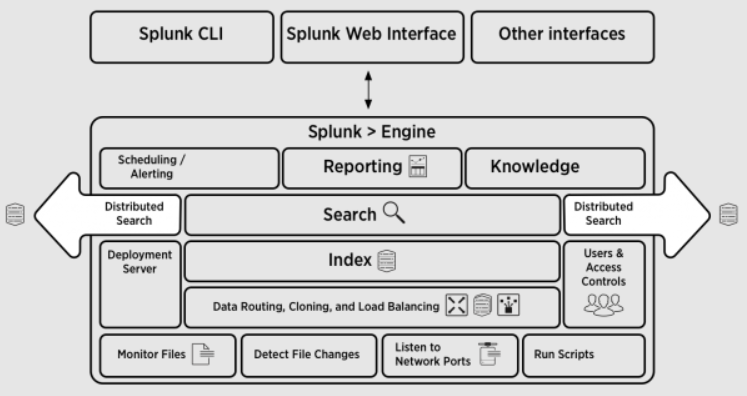
How Splunk Enterprise Security Works and Architecture
1. Data Ingestion
Splunk ES ingests data from various sources, including:
- Network devices (e.g., firewalls, routers)
- Endpoint protection platforms
- Cloud environments (e.g., AWS, Azure)
- Applications and databases
- Threat intelligence feeds
2. Data Processing
The platform normalizes and enriches the data to make it searchable and usable for security analytics.
3. Analytics and Machine Learning
Splunk ES applies advanced analytics and machine learning models to detect anomalies, correlate events, and generate actionable insights.
4. Dashboards and Alerts
Security teams use customizable dashboards to visualize data and receive alerts for critical incidents.
5. Integration with Tools
Splunk ES integrates with other security tools, such as SOAR platforms, to enable automated responses and streamline workflows.
How to Install Splunk Enterprise Security
Splunk Enterprise Security (ES) is an app that runs on top of Splunk Enterprise and provides advanced security analytics, incident management, and real-time monitoring for security information and event management (SIEM). While Splunk Enterprise itself is the core platform, Splunk ES enhances it by offering features like threat detection, compliance reporting, and security operations dashboards.
To install Splunk Enterprise Security (ES) programmatically, you would first need to install Splunk Enterprise, then install the Splunk Enterprise Security app on top of it. Here’s a step-by-step guide for installing both Splunk Enterprise and Splunk Enterprise Security using command-line and automation techniques.
1. Obtain Splunk Enterprise Installer
- Download the installer for Splunk Enterprise from the official Splunk website.
- After Splunk Enterprise is installed, you can install the Splunk Enterprise Security app from the Splunkbase marketplace (https://splunkbase.splunk.com/).
2. System Requirements
Ensure your system meets the minimum requirements for Splunk Enterprise and Splunk Enterprise Security:
- Operating System: Linux (CentOS, RHEL, Ubuntu), Windows
- Memory: Minimum 8 GB of RAM (16 GB or more recommended)
- Disk Space: Minimum 100 GB free (depending on data ingestion)
3. Install Splunk Enterprise
Step 1: Download Splunk Enterprise
- Download the Splunk Enterprise installer for your platform (Windows or Linux).
Step 2: Install Splunk Enterprise (Linux Example)
For Linux-based systems, you can install Splunk Enterprise using the following steps.
# Download Splunk (RHEL/CentOS-based systems)
wget -O splunk-8.2.1.1-XXXXXXX.rpm "https://www.splunk.com/download/splunk_enterprise"
# Install Splunk
sudo rpm -ivh splunk-8.2.1.1-XXXXXXX.rpm
# Start Splunk service
sudo /opt/splunk/bin/splunk start --accept-license
For Debian-based systems (Ubuntu):
# Download Splunk (Debian package)
wget -O splunk-8.2.1.1-XXXXXXX.deb "https://www.splunk.com/download/splunk_enterprise"
# Install Splunk
sudo dpkg -i splunk-8.2.1.1-XXXXXXX.deb
# Start Splunk service
sudo /opt/splunk/bin/splunk start --accept-license
Step 3: Start and Access Splunk Web Interface
After installation, you can start Splunk Enterprise and access the web interface at http://localhost:8000 (or any configured IP/port).
sudo /opt/splunk/bin/splunk start
4. Install Splunk Enterprise Security (ES)
Step 1: Download Splunk Enterprise Security from Splunkbase
- Go to Splunkbase and download Splunk Enterprise Security (the app).
- Alternatively, you can use the Splunk CLI to install the app from Splunkbase:
# Install Splunk Enterprise Security app via CLI
/opt/splunk/bin/splunk install app https://splunkbase.splunk.com/app/263/tarball/enterprise-security_XXXX.tgz
Alternatively, if you already have the .tar or .tgz package:
# Install app from a downloaded tarball
sudo /opt/splunk/bin/splunk install app /path/to/splunk-enterprise-security.tgz
Step 2: Enable and Configure Splunk Enterprise Security
- After installing, navigate to the Splunk Web interface (
http://localhost:8000). - Go to the Apps menu and select Enterprise Security.
- You may be prompted to configure data sources, such as Splunk Indexes or Security Intelligence Feeds.
Step 3: Configure Splunk ES Data Inputs
In order to begin monitoring security data, configure the following common data inputs:
- Security Event Logs (Windows Event Logs, Syslog, etc.)
- Threat Intelligence Feeds (e.g., STIX/TAXII integrations)
- Firewall, Intrusion Detection/Prevention Logs
You can configure these inputs either through the web interface or using configuration files under $SPLUNK_HOME/etc/apps/SplunkEnterpriseSecuritySuite.
5. Automate Installation on Multiple Machines (Windows Example)
If you need to deploy Splunk Enterprise and Splunk ES on multiple Windows machines, you can automate this using PowerShell.
# Download Splunk Enterprise Installer
Invoke-WebRequest -Uri "https://www.splunk.com/download/splunk_enterprise" -OutFile "C:\path\to\splunk_installer.exe"
# Silent installation of Splunk Enterprise
Start-Process -FilePath "C:\path\to\splunk_installer.exe" -ArgumentList "/quiet /install" -Wait
# Install Splunk Enterprise Security App
Start-Process -FilePath "C:\path\to\splunk-enterprise-security.tgz" -ArgumentList "/quiet /install" -Wait
6. Automate Installation on Multiple Linux Machines (Example)
For Linux-based systems, you can create a script to install Splunk Enterprise and Splunk Enterprise Security on multiple machines.
#!/bin/bash
# List of target machines
servers=("server1" "server2" "server3")
# Install Splunk Enterprise and Splunk ES
for server in "${servers[@]}"; do
ssh $server "wget https://www.splunk.com/download/splunk_enterprise"
ssh $server "sudo rpm -ivh splunk-8.2.1.1-XXXXXXX.rpm"
ssh $server "sudo /opt/splunk/bin/splunk start --accept-license"
ssh $server "sudo /opt/splunk/bin/splunk install app /path/to/splunk-enterprise-security.tgz"
done
7. Monitor and Maintain
After installation, use the Splunk Enterprise Security dashboards to monitor security events, analyze alerts, and manage incidents. You can also automate reports and configure alerting based on security events.
Summary:
To install Splunk Enterprise Security:
- Install Splunk Enterprise on your system using the provided installer for your platform (Windows or Linux).
- Download and install the Splunk Enterprise Security app either via the web interface or command line (
splunk install app). - Configure security data inputs for monitoring logs, alerts, and threat intelligence feeds.
- Use automation scripts (PowerShell for Windows, Bash for Linux) to deploy Splunk Enterprise and Splunk ES on multiple machines.
Once installed and configured, you can start using Splunk Enterprise Security for enhanced security monitoring, incident response, and threat intelligence management.
Basic Tutorials of Splunk Enterprise Security: Getting Started
Step 1: Log in to Splunk ES
- Access the Splunk ES dashboard using your admin credentials.
Step 2: Add Data Sources
- Navigate to Settings > Data Inputs.
- Add sources like syslogs, cloud services, and threat intelligence feeds.
Step 3: Configure Dashboards
- Set up dashboards to monitor metrics such as login activities, network traffic, and endpoint alerts.
Step 4: Create Correlation Searches
- Use the Correlation Searches section to create rules that detect complex attack patterns.
- Set up alerts for critical incidents.
Step 5: Investigate Incidents
- Use the Incident Review section to analyze alerts, correlate events, and investigate root causes.
Step 6: Automate Responses
- Integrate with SOAR tools to create automated workflows for incident containment and remediation.