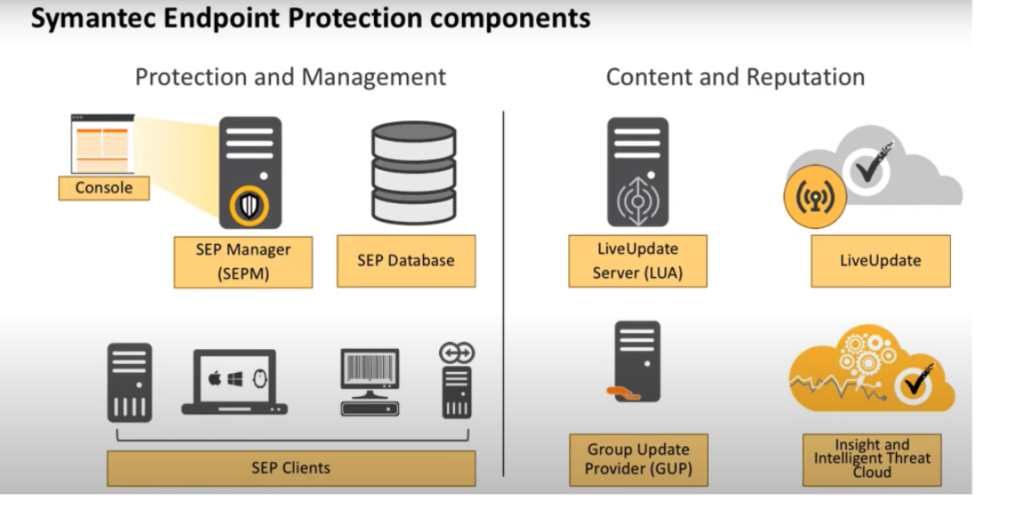
Symantec Endpoint Protection is a comprehensive security solution designed to protect endpoints such as desktops, laptops, and servers from a wide range of cyber threats, including malware, ransomware, and advanced persistent threats (APTs). It integrates multiple security features, including antivirus, firewall protection, device control, and advanced machine learning-based threat detection, offering real-time protection and ensuring minimal system performance impact. The solution is built for enterprise environments, providing centralized management and visibility across large numbers of endpoints.
Use cases for Symantec Endpoint Protection include malware and virus protection, where it safeguards endpoints from various types of malicious software; data loss prevention, ensuring sensitive information remains secure; device control, preventing unauthorized devices from accessing the network; and compliance enforcement, helping organizations meet regulatory requirements for data protection. It is widely used in industries such as finance, healthcare, and manufacturing to secure endpoints against evolving cyber threats and maintain organizational security.
What is Symantec Endpoint Protection?
Symantec Endpoint Protection is an endpoint security software suite that protects devices like desktops, laptops, and servers from malware, ransomware, phishing, and other cyber threats. SEP combines signature-based detection, machine learning, and behavior analysis to provide robust and real-time protection. It supports both on-premises and cloud-based environments, making it adaptable to modern IT infrastructure.
Key Characteristics of Symantec Endpoint Protection:
- Advanced Threat Protection: Combines signature-based detection with AI-powered machine learning.
- Centralized Management: Provides a unified console to manage security policies across all endpoints.
- Multi-Layered Defense: Includes antivirus, firewall, intrusion prevention, and exploit protection.
- Adaptable Deployment: Works in on-premises, cloud, and hybrid environments.
Top 10 Use Cases of Symantec Endpoint Protection
- Malware and Ransomware Protection
- Detects and blocks malicious software, including ransomware, using signature-based and behavior-based detection.
- Intrusion Prevention
- Monitors network traffic to detect and block potential intrusions or unauthorized access attempts.
- Phishing Protection
- Identifies and prevents phishing attacks by blocking malicious emails and URLs.
- Zero-Day Threat Detection
- Leverages machine learning and sandboxing to detect and mitigate zero-day vulnerabilities.
- Application and Device Control
- Restricts unauthorized applications and devices from accessing the network or endpoint systems.
- Endpoint Detection and Response (EDR)
- Provides advanced tools to detect, investigate, and respond to complex threats across endpoints.
- Data Loss Prevention (DLP)
- Prevents unauthorized access or transmission of sensitive information from endpoints.
- Cloud and Virtualization Security
- Protects workloads and virtual environments hosted in cloud infrastructures or on-premises data centers.
- Compliance Management
- Helps organizations meet regulatory compliance requirements, such as GDPR and HIPAA, through robust endpoint protection.
- Real-Time Threat Intelligence
- Uses threat intelligence feeds to stay updated on the latest vulnerabilities and attacks.
Features of Symantec Endpoint Protection
- Antivirus and Antimalware – Provides signature-based and heuristic detection to identify and neutralize malware.
- Intrusion Prevention System (IPS) – Monitors network activity to block malicious traffic and exploits.
- Behavioral Monitoring – Detects suspicious behavior on endpoints to prevent zero-day attacks.
- Exploit Prevention – Protects against vulnerabilities in software by blocking exploit attempts.
- Device Control – Restricts unauthorized USB drives or external devices from accessing endpoints.
- Firewall Protection – Implements rules to allow or block traffic based on network activity.
- Centralized Management Console – Offers a single dashboard for deploying, monitoring, and managing endpoint security policies.
- EDR Capabilities – Includes tools for detecting, investigating, and responding to advanced threats.
- Cloud-Based and On-Premises Options – Supports flexible deployment models to suit various organizational needs.
- Seamless Integration – Works with other security tools and platforms to enhance overall security posture.
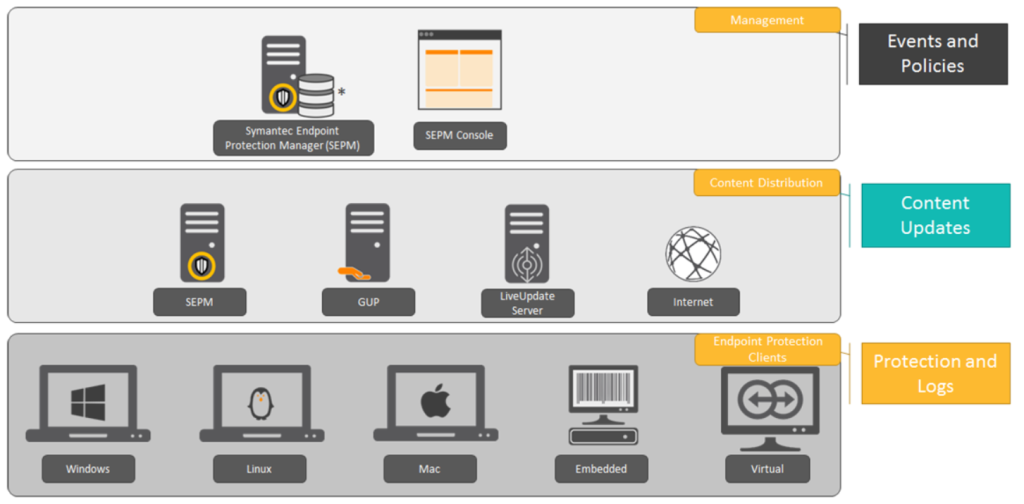
How Symantec Endpoint Protection Works and Architecture
1. Multi-Layered Protection
Symantec Endpoint Protection employs multiple layers of security to protect against known and unknown threats:
- Antivirus and Antimalware: Detects and removes malicious software.
- Behavioral Analysis: Monitors and blocks suspicious activities.
- Intrusion Prevention: Protects against network-based attacks.
2. Centralized Management Console
The SEP Manager provides a unified interface for administrators to configure policies, monitor activity, and generate reports.
3. Endpoint Agents
Lightweight agents are deployed on endpoints to enforce security policies and communicate with the management console.
4. Threat Intelligence Integration
Symantec leverages global threat intelligence feeds to identify new threats and update endpoint protection.
5. Cloud and Hybrid Support
The platform integrates with cloud-based services and supports hybrid environments to secure workloads.
How to Install Symantec Endpoint Protection
To install Symantec Endpoint Protection (SEP) programmatically, you typically need to use installation scripts or automated deployment tools, especially in enterprise environments. The installation process involves downloading the SEP client and running the installer with specific configurations.
Here is a general guide for installing Symantec Endpoint Protection (SEP) using code or script for Windows and Linux systems.
Installing Symantec Endpoint Protection on Windows (using Command Line)
1. Obtain the SEP Installer
First, you need to obtain the Symantec Endpoint Protection installer package, which is typically distributed as a .exe file for Windows. You can get the installer from the Symantec website or through your Symantec admin console.
2. Silent Installation using Command Line
For a silent installation (i.e., without user interaction), you can use the following command:
setup.exe /quiet /install
This will install Symantec Endpoint Protection with the default settings.
3. Advanced Silent Installation with Custom Options
If you want to customize the installation (e.g., specify the location of the installation or configure features), you can use additional command-line options. Here’s an example of a more customized command:
setup.exe /quiet /install /components=Antivirus,Firewall /installpath="C:\Program Files\Symantec\Endpoint Protection"
/quietensures the installation is silent./installstarts the installation./componentsspecifies which components to install (e.g., Antivirus, Firewall)./installpathspecifies the installation directory.
4. Post-Installation (Optional)
You may need to restart the machine after installation:
shutdown /r /t 0
This will restart the system immediately after the SEP installation is complete.
Installing Symantec Endpoint Protection on Linux (using Command Line)
For Linux systems, the process involves downloading the SEP Linux package (.rpm or .tar.gz format) and running the appropriate installation commands.
1. Obtain the SEP Installer
Download the appropriate Symantec Endpoint Protection for Linux installer from the Symantec website.
2. Install on Linux (RPM Example)
For Red Hat/CentOS-based systems (RPM package), use the following command:
sudo rpm -ivh Symantec_Endpoint_Protection.rpm
For Ubuntu/Debian-based systems, use the .deb package and install with:
sudo dpkg -i symantec_endpoint_protection.deb
3. Silent Installation
For a silent installation on Linux, you can add the -i flag, like so:
sudo ./install.sh -i
This ensures that the installation proceeds without requiring user input.
4. Start Symantec Endpoint Protection Service
After installation, ensure that the SEP service is running:
sudo service symantec-agent start
Or check its status:
sudo service symantec-agent status
Automating Deployment in Enterprise Environments
In enterprise environments, you often need to deploy Symantec Endpoint Protection to multiple machines. This can be done using Symantec Endpoint Protection Manager (SEPM) or using deployment scripts like PowerShell (for Windows) or Bash (for Linux) to automate the installation across multiple systems.
For example, to deploy to multiple machines using a PowerShell script on Windows, you can use the following example:
$computers = Get-Content -Path "C:\computers.txt"
foreach ($computer in $computers) {
Invoke-Command -ComputerName $computer -ScriptBlock {
Start-Process "C:\path\to\setup.exe" -ArgumentList "/quiet /install"
}
}
This script reads a list of computer names from computers.txt and installs SEP on each machine remotely.
Monitoring and Post-Installation
Once SEP is installed, ensure that the product is running correctly by checking the status of the Symantec services or by accessing the Symantec Endpoint Protection Manager (SEPM) to manage the agents.
Basic Tutorials of Symantec Endpoint Protection: Getting Started
Step 1: Log In to the Management Console
- Access the SEP Manager console using your admin credentials.
Step 2: Add Endpoints
- Navigate to the Clients tab.
- Deploy agents to devices manually or through automated discovery.
Step 3: Configure Policies
- Go to the Policies tab.
- Create and assign policies for antivirus, firewall, intrusion prevention, and device control.
Step 4: Monitor Security Events
- Use the Dashboard to view real-time alerts, incidents, and endpoint status.
Step 5: Generate Reports
- Access the Reports section to create detailed reports on malware detection, endpoint activity, and compliance.
- Share these reports with stakeholders for analysis and decision-making.