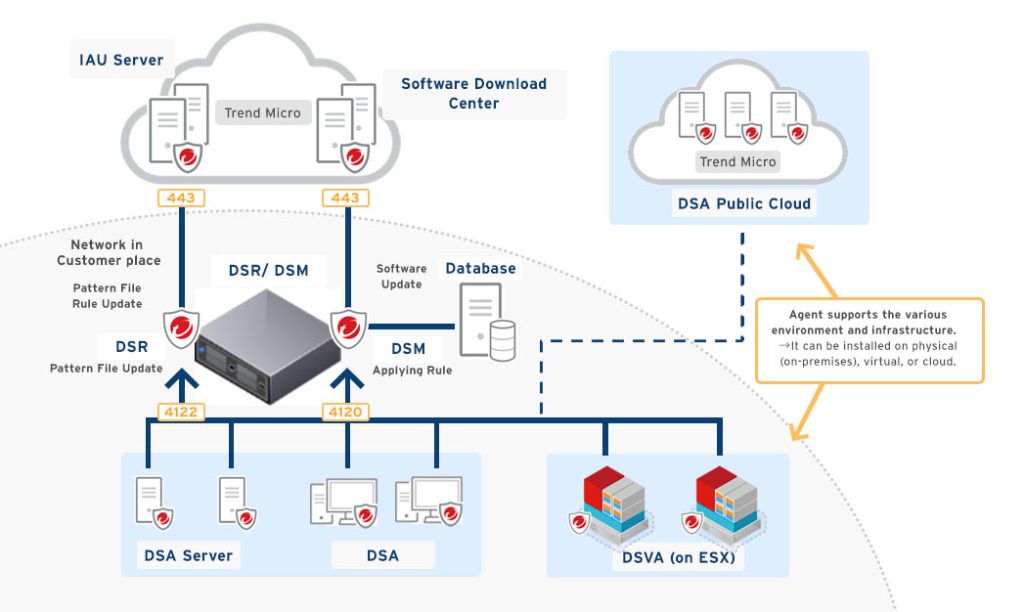
TrendMicro Deep Security is a comprehensive security platform designed to protect virtual, cloud, and physical servers from a wide range of threats. It provides advanced protection features such as intrusion detection and prevention (IDS/IPS), anti-malware, web reputation, firewall, and application control. Deep Security is particularly useful for securing cloud environments, including hybrid and multi-cloud infrastructures, as well as virtualized environments. It enables organizations to achieve continuous security without sacrificing performance, thanks to its lightweight agent-based approach.
Use cases for TrendMicro Deep Security include cloud security, where it ensures the protection of workloads across public and private cloud environments; endpoint security, providing real-time protection for physical and virtual servers; and compliance, where it helps meet regulatory requirements by securing sensitive data and applications. It is widely used in industries such as finance, healthcare, and retail to enhance security posture, prevent breaches, and safeguard critical infrastructure from cyber threats.
What is Trend Micro Deep Security?
Trend Micro Deep Security is a cloud workload protection platform that offers multi-layered security to protect data centers, cloud environments, and containers. It is widely used to secure servers, virtual machines, and hybrid cloud infrastructures, providing a unified platform for monitoring, detecting, and preventing threats in real-time.
Key Characteristics of Trend Micro Deep Security:
- Comprehensive Protection: Offers multiple layers of security, including anti-malware, firewall, and intrusion prevention.
- Cloud-Native: Integrates seamlessly with public cloud providers like AWS, Azure, and Google Cloud.
- Scalability: Designed to protect workloads in both small-scale environments and large enterprises.
- Automation: Automates security processes to improve efficiency and reduce operational overhead.
Top 10 Use Cases of Trend Micro Deep Security
- Cloud Workload Protection
- Secures workloads running on AWS, Azure, and Google Cloud with built-in integrations.
- Virtual Environment Security
- Provides advanced protection for VMware, Microsoft Hyper-V, and other virtualized environments.
- Container Security
- Monitors and protects containerized applications across platforms like Kubernetes and Docker.
- Intrusion Detection and Prevention
- Identifies and blocks unauthorized access attempts and exploits.
- Anti-Malware Protection
- Detects and removes malware from servers and workloads in real-time.
- Compliance Management
- Helps organizations meet compliance requirements like GDPR, HIPAA, and PCI-DSS through log inspection and integrity monitoring.
- Application Control
- Restricts unauthorized applications from running, ensuring only approved software operates on workloads.
- File Integrity Monitoring
- Monitors critical system files for unauthorized changes to detect potential tampering or attacks.
- Firewall Protection
- Provides a host-based firewall to prevent unauthorized network access to workloads.
- Log Inspection
- Collects and analyzes logs for suspicious activity to enhance threat detection and compliance.
Features of Trend Micro Deep Security
- Intrusion Detection and Prevention (IDS/IPS) – Protects workloads from vulnerabilities and exploits.
- Anti-Malware – Offers advanced malware detection and removal capabilities.
- File Integrity Monitoring – Tracks changes to critical files for signs of tampering.
- Web Application Protection – Secures web applications against common attacks like SQL injection and cross-site scripting.
- Host-Based Firewall – Filters traffic to and from workloads, reducing the attack surface.
- Log Inspection – Monitors and analyzes logs for suspicious activity and compliance reporting.
- Cloud Integrations – Works seamlessly with AWS, Azure, Google Cloud, and VMware environments.
- Centralized Management – Provides a unified dashboard for managing and monitoring security across environments.
- Scalable Deployment – Protects workloads in on-premises, cloud, and hybrid environments.
- Automation – Automates security processes, including patching and policy updates.
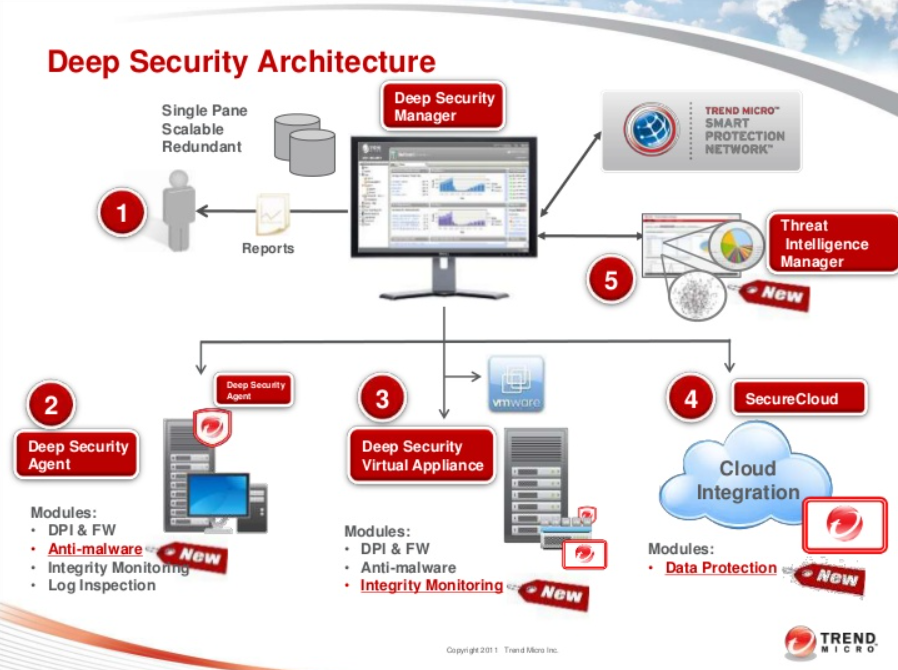
How Trend Micro Deep Security Works and Architecture
1. Agent-Based Protection
Trend Micro Deep Security uses lightweight agents installed on workloads to provide real-time protection. These agents monitor traffic, inspect logs, and enforce security policies.
2. Centralized Management Console
A centralized console allows administrators to configure, manage, and monitor security policies across all workloads.
3. Integration with Cloud Platforms
Deep Security integrates natively with AWS, Azure, and Google Cloud to provide automatic discovery and protection of cloud workloads.
4. Multi-layered Protection
The platform combines intrusion detection and prevention, anti-malware, firewall, and other features to deliver comprehensive security.
5. Automation and Orchestration
Automation features enable the platform to respond to threats in real-time, apply patches, and enforce compliance policies without manual intervention.
How to Install Trend Micro Deep Security
Trend Micro Deep Security is a security solution designed for protecting physical, virtual, and cloud servers from malware, vulnerabilities, and other threats. It typically uses an agent-based architecture where security agents are installed on the target systems. The installation process generally involves setting up the agent on servers or virtual machines, and configuring Deep Security Manager for centralized management.
While you generally use the Deep Security Manager (DSM) web interface for configuration and managing the agents, there are also command-line options for installation and automation. Below is a general guide for installing Trend Micro Deep Security on a Linux system or Windows server, and automating the installation of agents.
Steps to Install Trend Micro Deep Security
1. Obtain Trend Micro Deep Security Installer
- Sign up for Trend Micro Deep Security by visiting the Trend Micro website.
- Download the appropriate installer for your operating system (e.g., Linux or Windows).
- You will typically get a management console (Deep Security Manager) and agent installers.
2. System Requirements
Before installation, ensure the target machine meets the system requirements for the Deep Security Agent. These requirements can vary depending on your environment (e.g., virtualized, cloud, or on-premise servers).
3. Install Deep Security Manager (For Centralized Management)
The Deep Security Manager (DSM) is the web interface where you can manage your agents, define policies, and monitor security. The installation steps for DSM typically depend on whether you’re using a cloud or on-premise setup.
If you’re setting up a DSM on a Linux machine, the installation typically looks like this:
# Download the DSM installer (RPM for Linux)
wget https://download.trendmicro.com/DeepSecurityManagerInstaller.rpm
# Install the Deep Security Manager (DSM)
sudo rpm -ivh DeepSecurityManagerInstaller.rpm
Follow the on-screen instructions for setting up the Deep Security Manager.
4. Install Deep Security Agent on Servers or Virtual Machines
Once DSM is set up, you can install the Deep Security Agent on your servers or virtual machines.
Install on Linux (Example):
- Download the Deep Security Agent package for your Linux distribution (RPM, DEB).
- Run the following commands:
# Download the agent installer (for example, RPM)
wget https://download.trendmicro.com/DeepSecurityAgentInstaller.rpm
# Install the Deep Security Agent
sudo rpm -ivh DeepSecurityAgentInstaller.rpm
# After installation, the agent will attempt to register itself with the DSM
- During the installation, the agent will attempt to connect to the Deep Security Manager. If needed, you can manually register the agent using the registration key.
Install on Windows (Example):
- Download the Deep Security Agent installer for Windows.
- Use PowerShell or Command Prompt for silent installation:
# Run the installer silently
Start-Process -FilePath "C:\path\to\DeepSecurityAgentInstaller.exe" -ArgumentList "/quiet /install"
This command will install the agent without any prompts.
5. Configure the Deep Security Agent
After installing the agent, configure it to connect to the Deep Security Manager:
- The agent automatically registers with the Deep Security Manager if the connection is successful.
- You can also manually configure the agent by editing its configuration file located in
/etc/(for Linux) or through the Deep Security Manager web interface.
6. Automation with API (Optional)
If you need to automate the installation or configuration of Deep Security Agents, you can use Trend Micro Deep Security APIs. The API allows you to programmatically manage agent registration, deployment, and configuration.
Here’s an example of using the API to retrieve the status of an agent:
import requests
api_url = "https://your-dsm-server/api/v1/agents"
api_key = "your_api_key"
headers = {
"Authorization": f"APIKey {api_key}",
"Content-Type": "application/json"
}
response = requests.get(api_url, headers=headers)
if response.status_code == 200:
agents = response.json()
print("Agent Status:", agents)
else:
print("Error fetching agent status", response.status_code)
This API request fetches the agent status from your Deep Security Manager instance.
7. Monitor and Maintain
After the agent is installed and configured, you can monitor its status from the Deep Security Manager web interface. It will show active protections, detected threats, and health information for all connected agents.
Basic Tutorials of Trend Micro Deep Security: Getting Started
Step 1: Log In to the Management Console
- Access the Deep Security Manager console using your credentials.
Step 2: Add Workloads
- Navigate to Computers in the console.
- Add workloads manually or enable automatic discovery for cloud environments.
Step 3: Assign Security Policies
- Select a workload and assign a predefined or custom security policy.
- Apply intrusion prevention, anti-malware, and other security modules.
Step 4: Monitor Threats
- Use the dashboard to monitor threats, alerts, and security events in real-time.
Step 5: Generate Reports
- Access the Reports section to generate compliance or threat analysis reports.